This document discusses web application security from the perspectives of web developers and attackers. It covers common issues web developers face, such as tight deadlines and lack of security standards. It also describes how attackers exploit vulnerabilities like injection attacks and XSS. Recent attacks are presented as examples, such as compromising a power grid operator's website through SQL injection. The document aims to raise awareness of web security challenges.









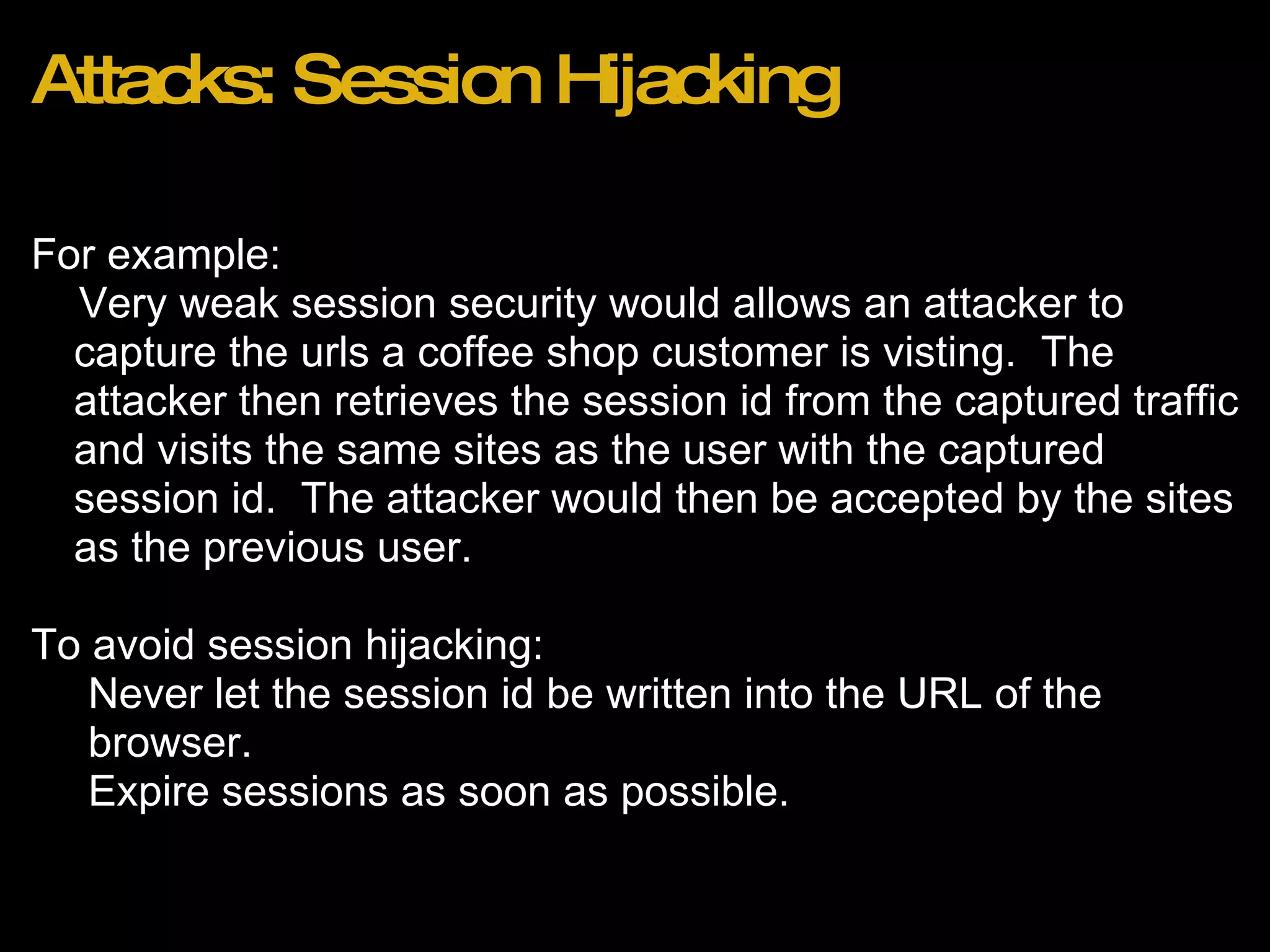
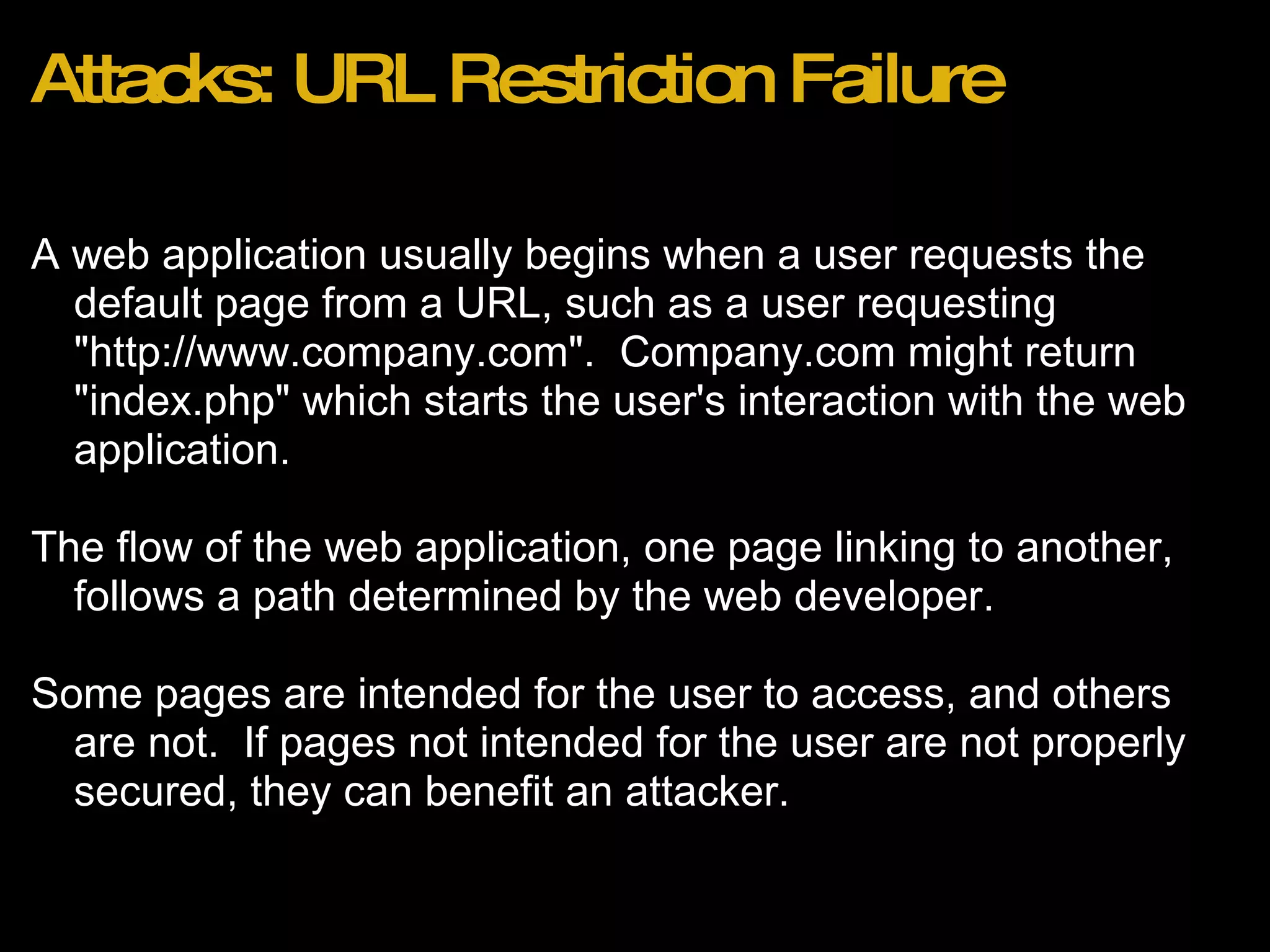
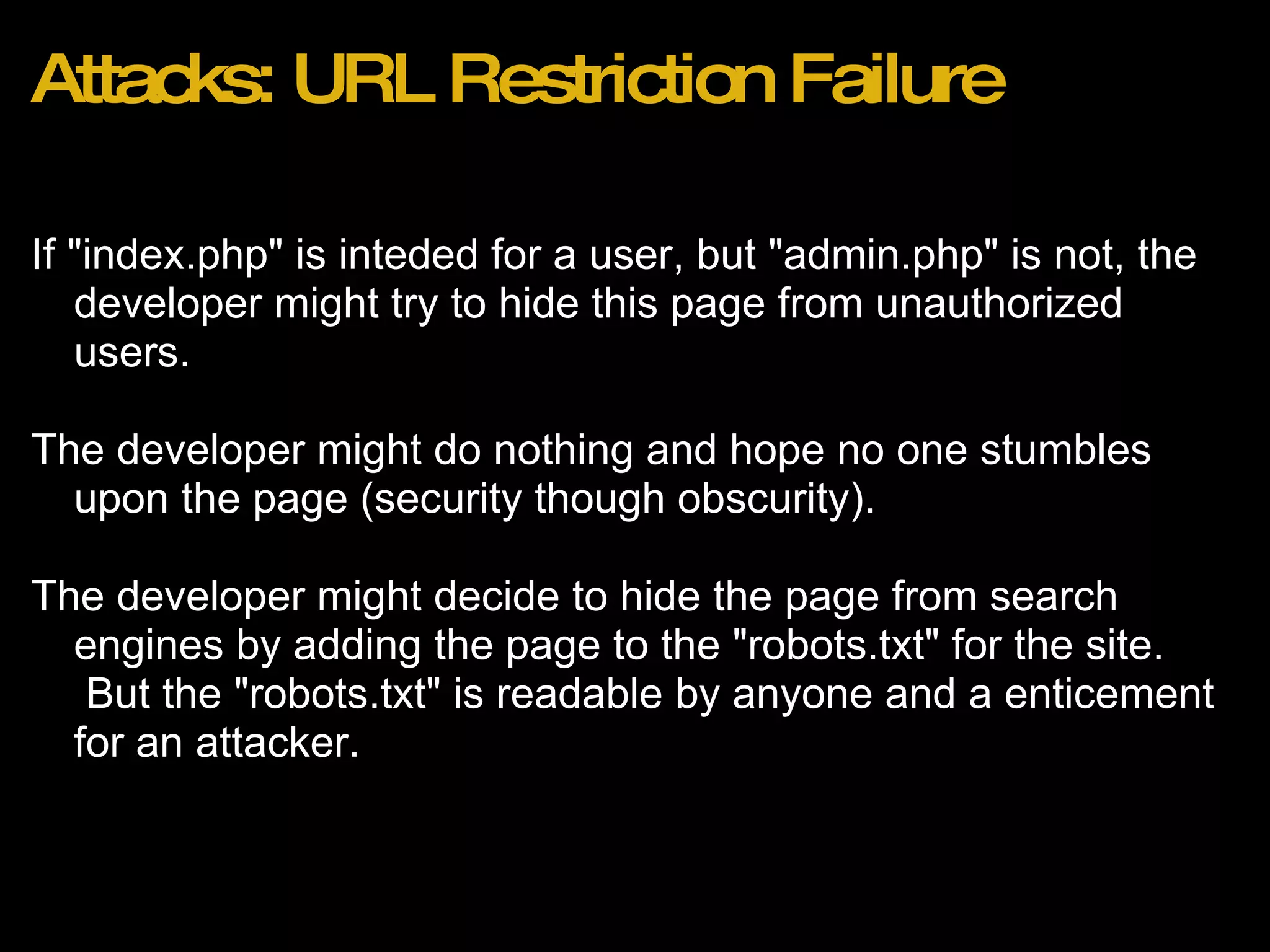

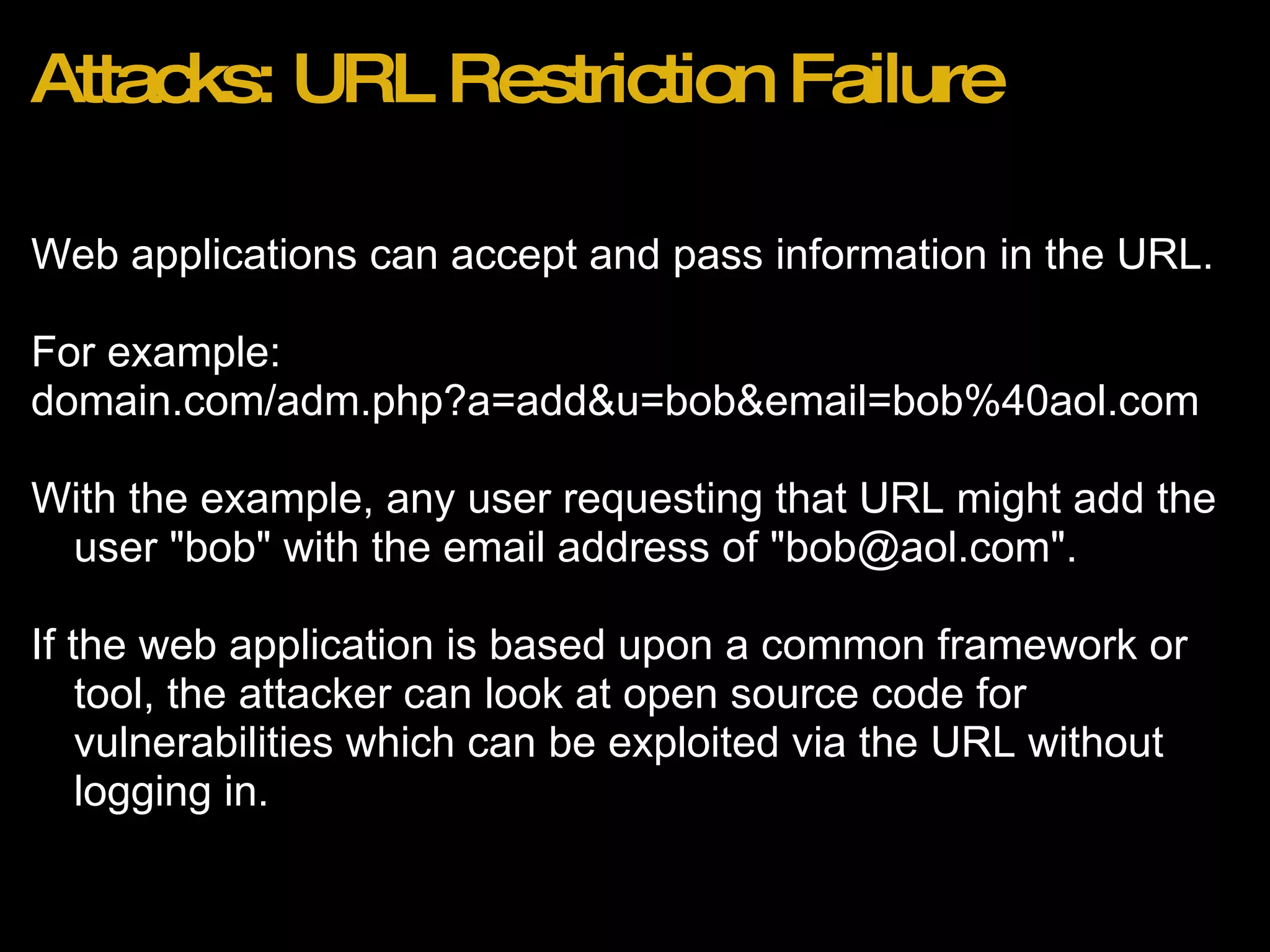
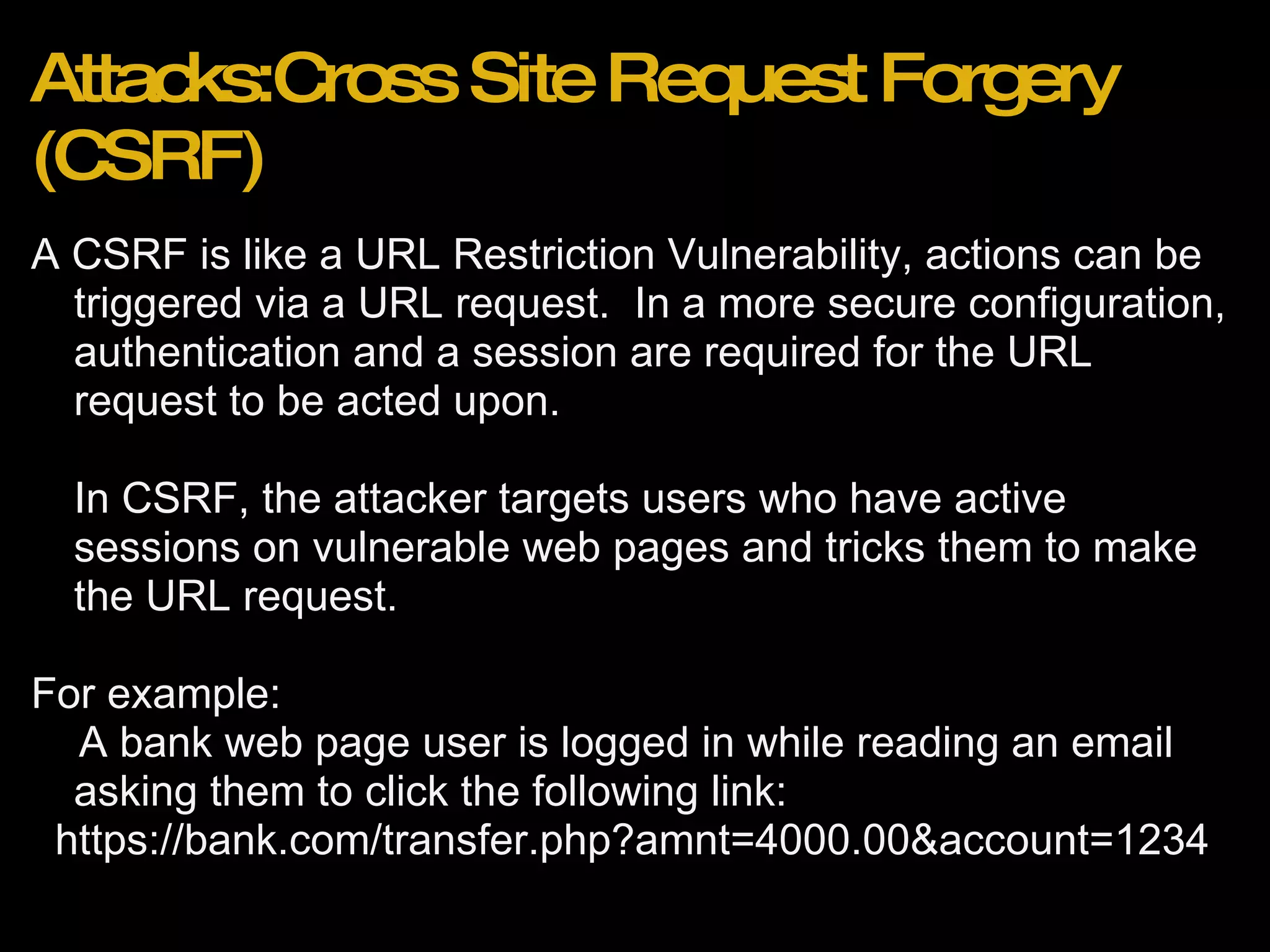
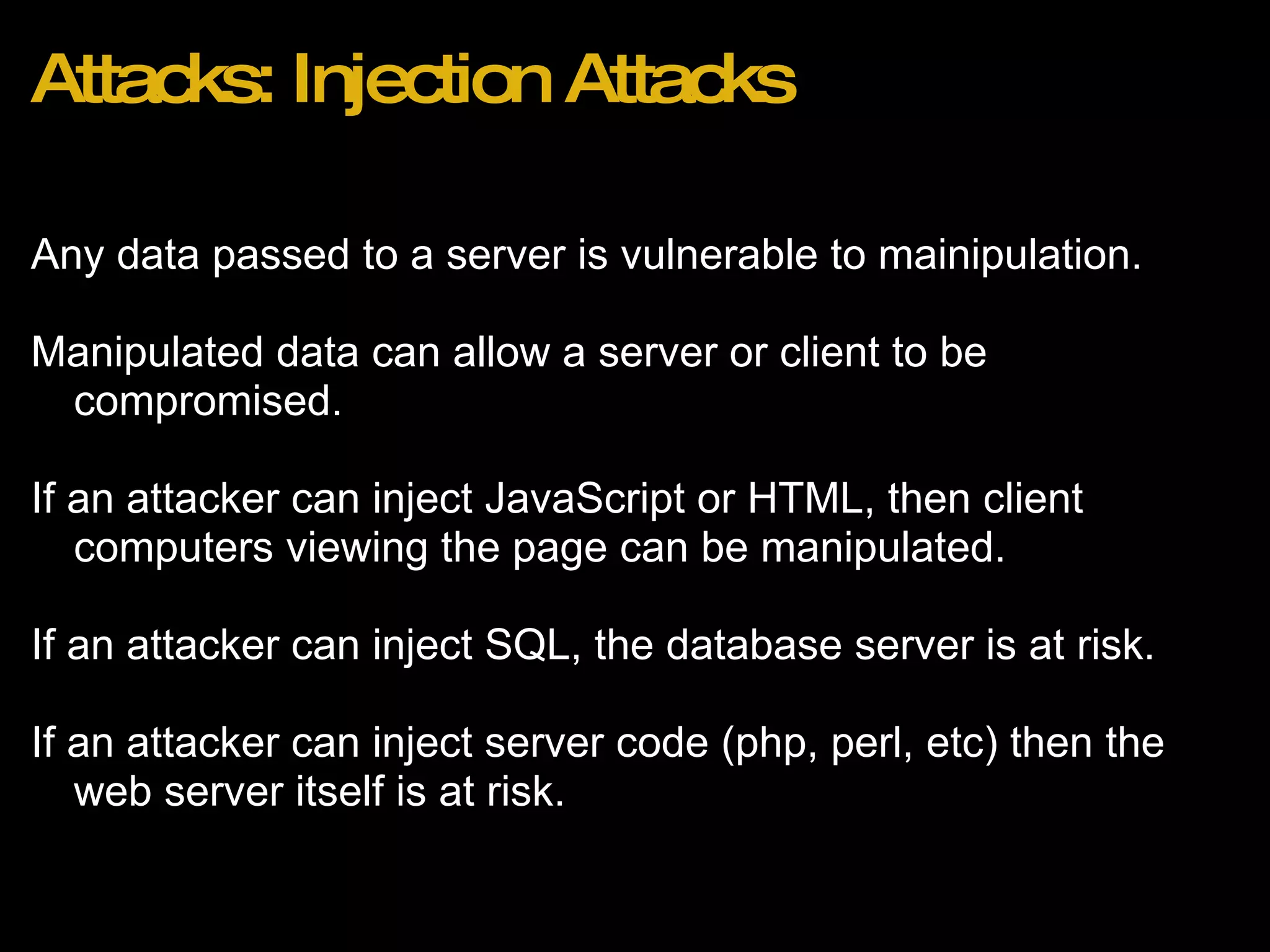


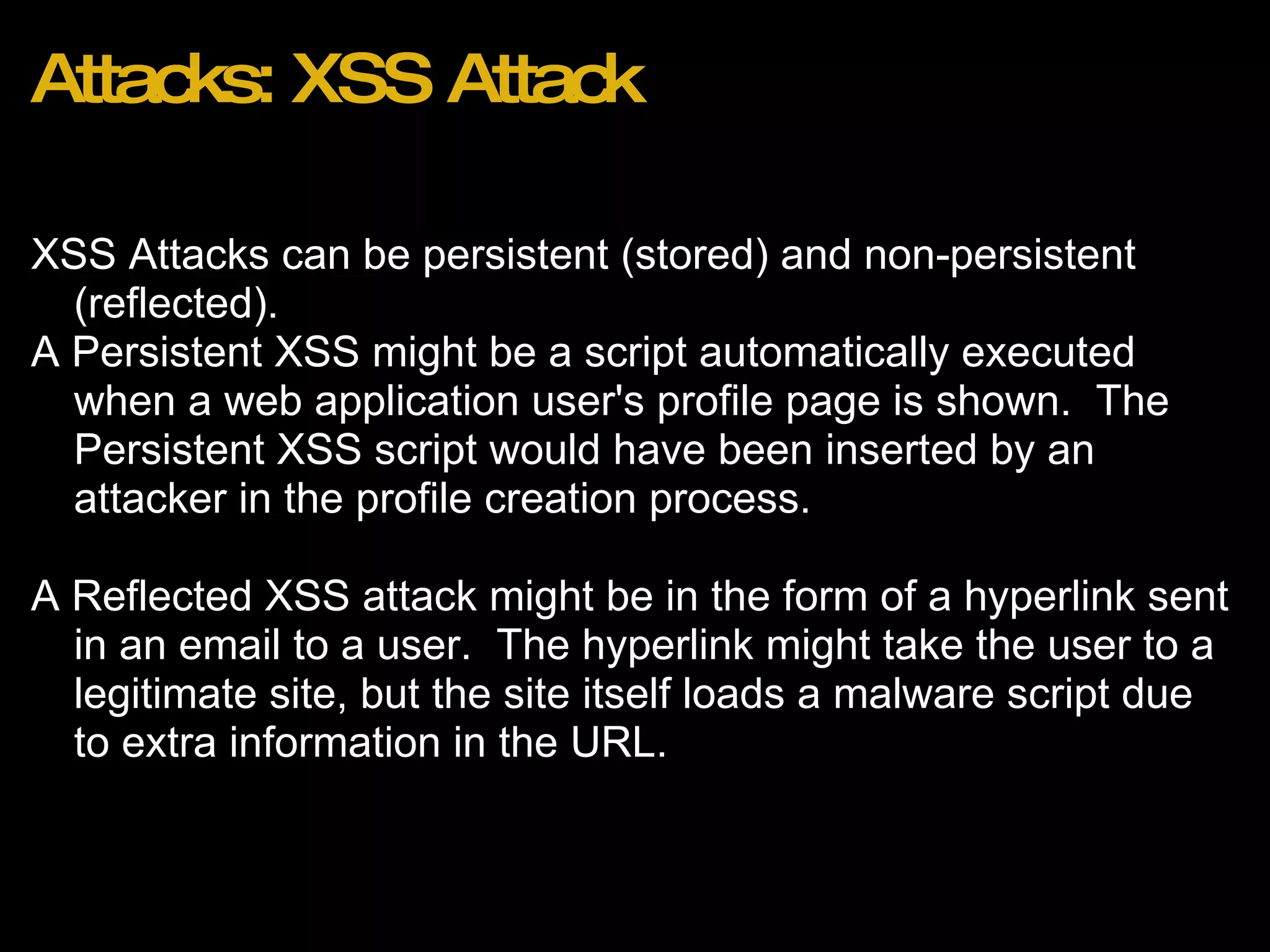
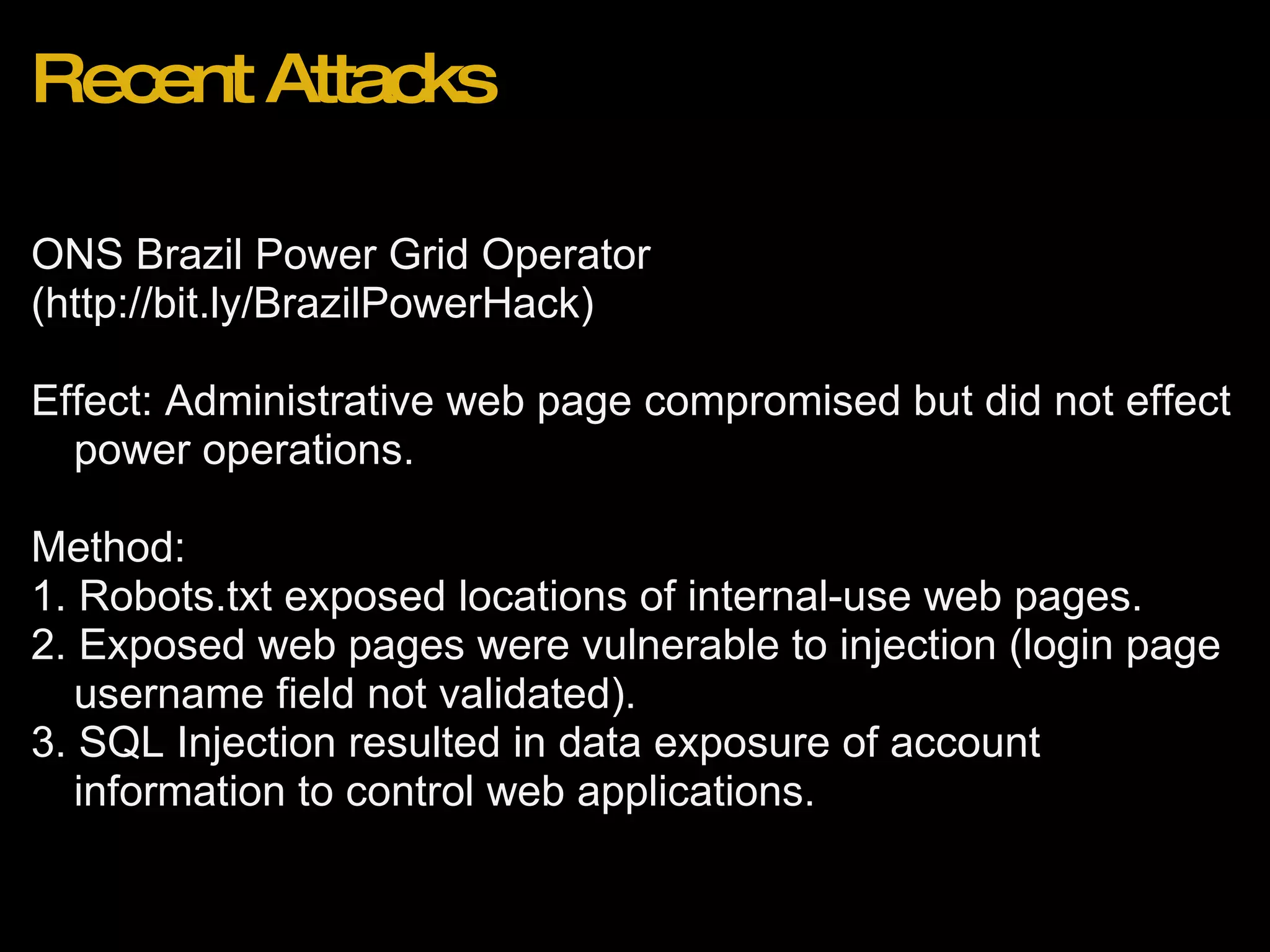
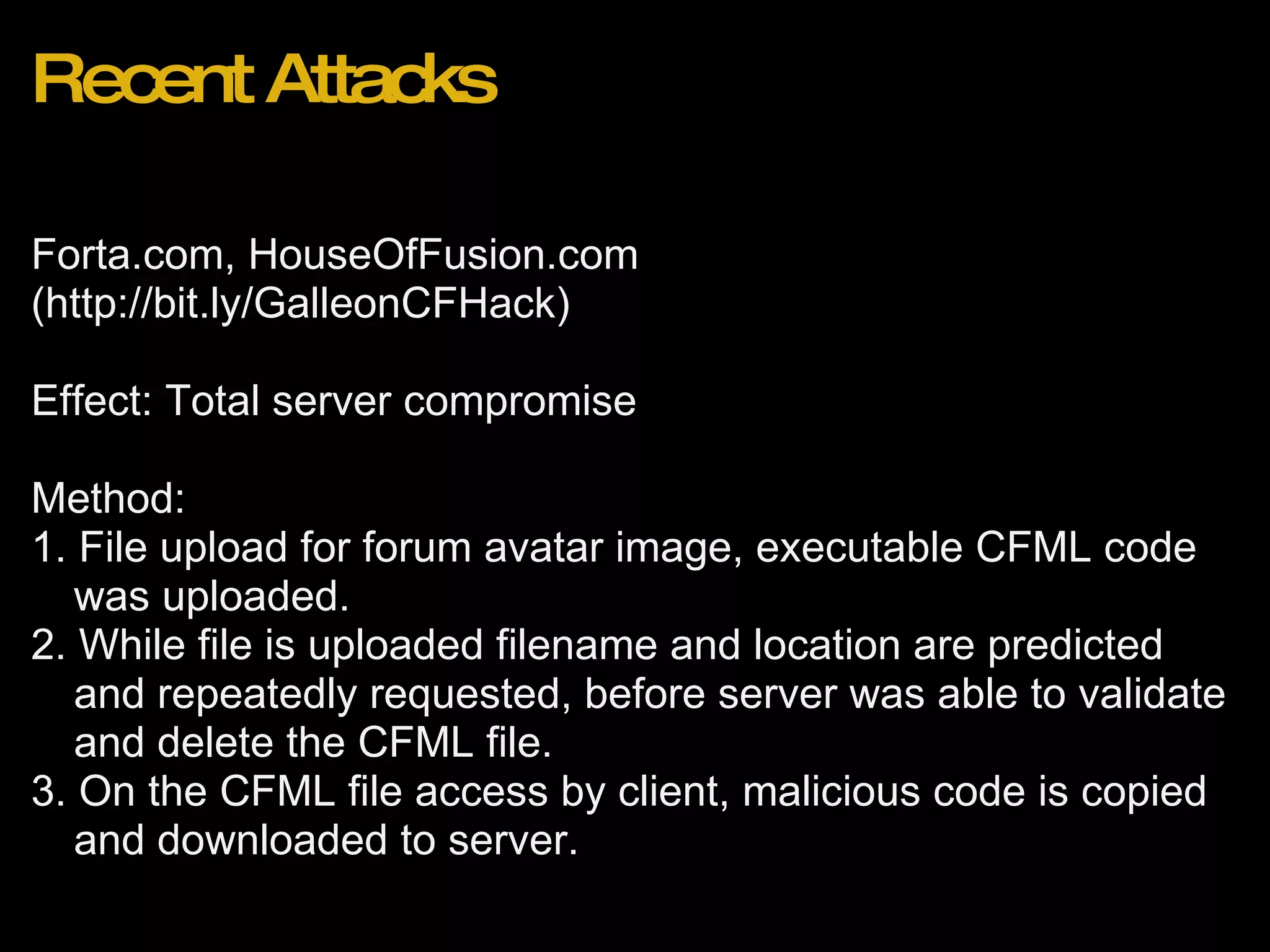
![Recent Attacks Wordpress 2.8.3 Blogs (http://bit.ly/wordpress283hack) Effect: Reset of admin account password to unknown value. Method: 1. Attacker browses to http://domain.com/wp-login.php?action=rp&key[] 2. Admin account password is reset to random string with no confirmation email.](https://image.slidesharecdn.com/webapplicationsecurity-091205210001-phpapp02/75/Web-Application-Security-25-2048.jpg)