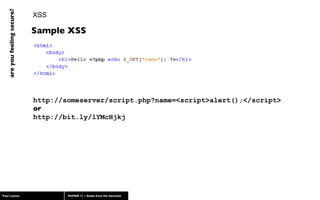
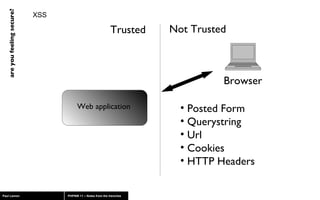
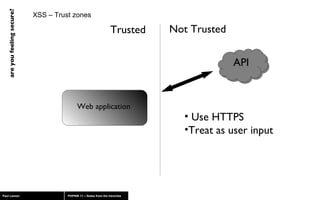
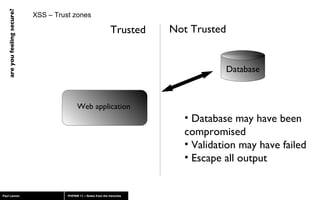
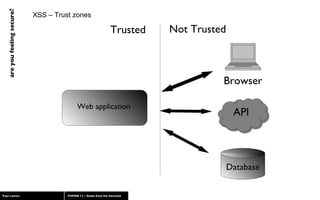
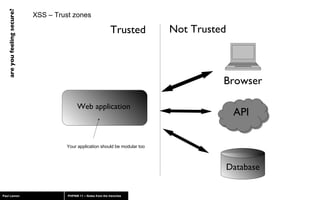
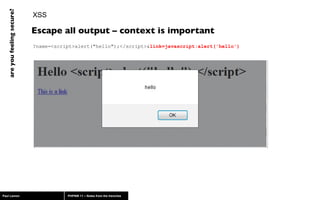
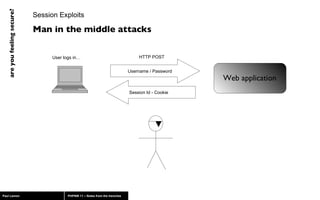
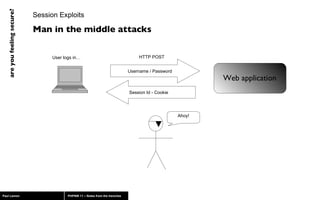
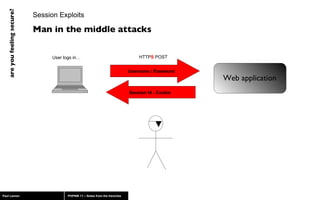
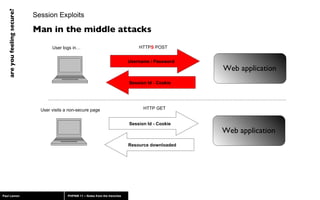
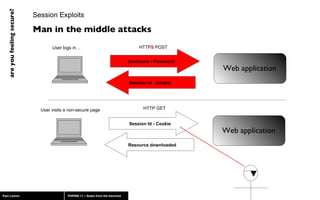
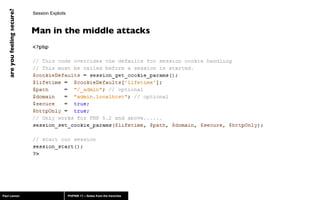
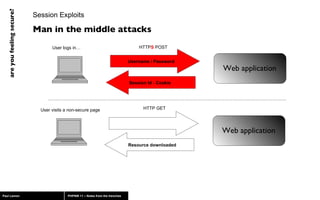
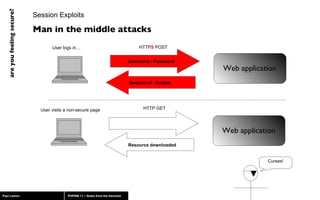
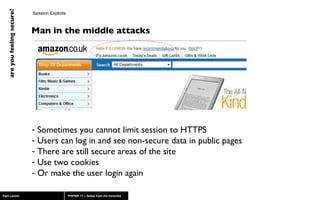
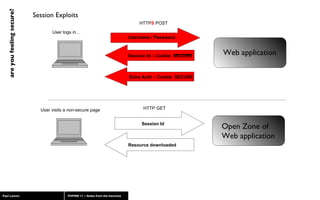
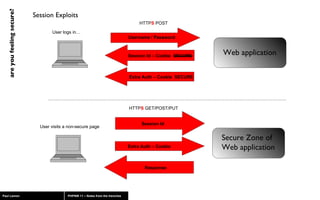
The document discusses web application security, highlighting risks like SQL injection, cross-site scripting (XSS), and session exploitation while providing strategies for prevention. It emphasizes the importance of input validation, parameterized queries, and proper session management to protect applications from vulnerabilities. Additionally, the author advocates for using well-supported frameworks and regular monitoring to ensure security.