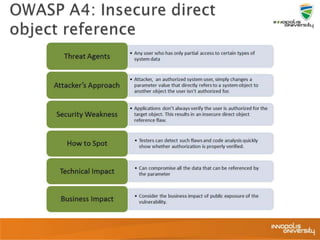
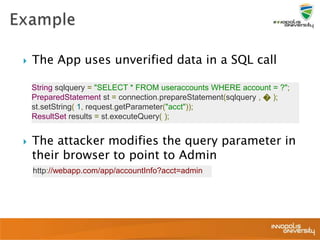
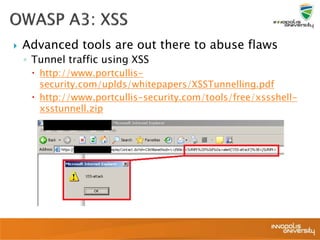
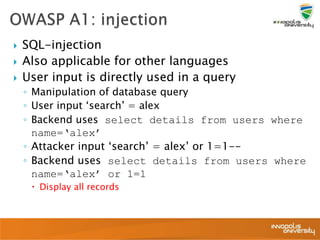
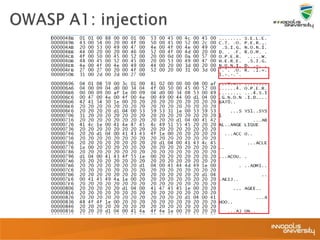
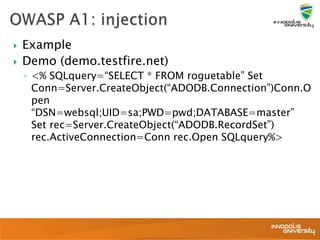
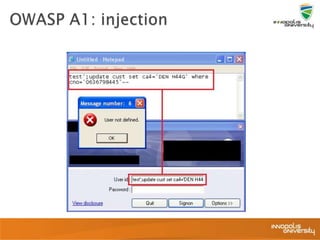
This document summarizes a presentation on web application security and the OWASP Top 10. It discusses the motivation for securing web apps, common causes of data breaches, and an overview of the OWASP Top 10 project and the most critical web application security flaws. The presentation recommends ways to address these issues, such as keeping software updated, using automated scanning tools, and implementing input validation and authorization checks. Specific attacks covered include cross-site scripting, insecure direct object references, and broken authentication and session management.












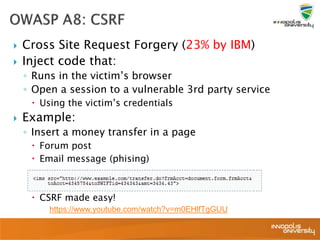

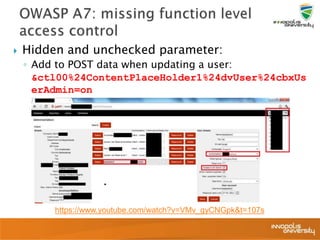



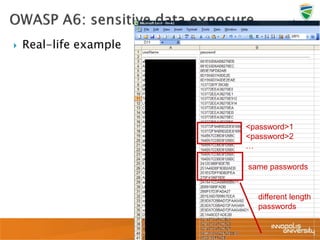

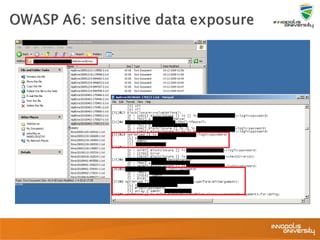
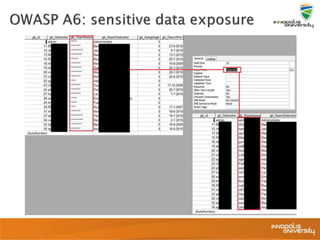



![ User can access and
modify object values
Example:
◦ Login using your credentials
◦ Link refers to
http://app/details?userid=1
◦ Script download of all files
userid=[1-9999]
Hashing doesn’t help
◦ Reverse MD5 hash lookup
◦ http://tools.benramsey.com/md5/](https://image.slidesharecdn.com/6-webapplicationsecurity-240210204208-099031ed/85/6-Web-Application-Security-pptx-30-320.jpg)