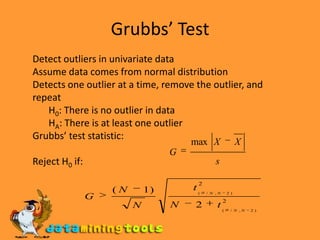
Anomaly detection techniques aim to identify outliers or anomalies in datasets. Statistical approaches assume a data distribution and detect anomalies that differ significantly. Distance-based approaches measure distances between data points to find outliers that are far from neighbors. Clustering approaches group normal data and detect outliers in small clusters or far from other clusters. Challenges include determining the number of outliers, handling unlabeled data, and scaling to high dimensions where distances become similar.