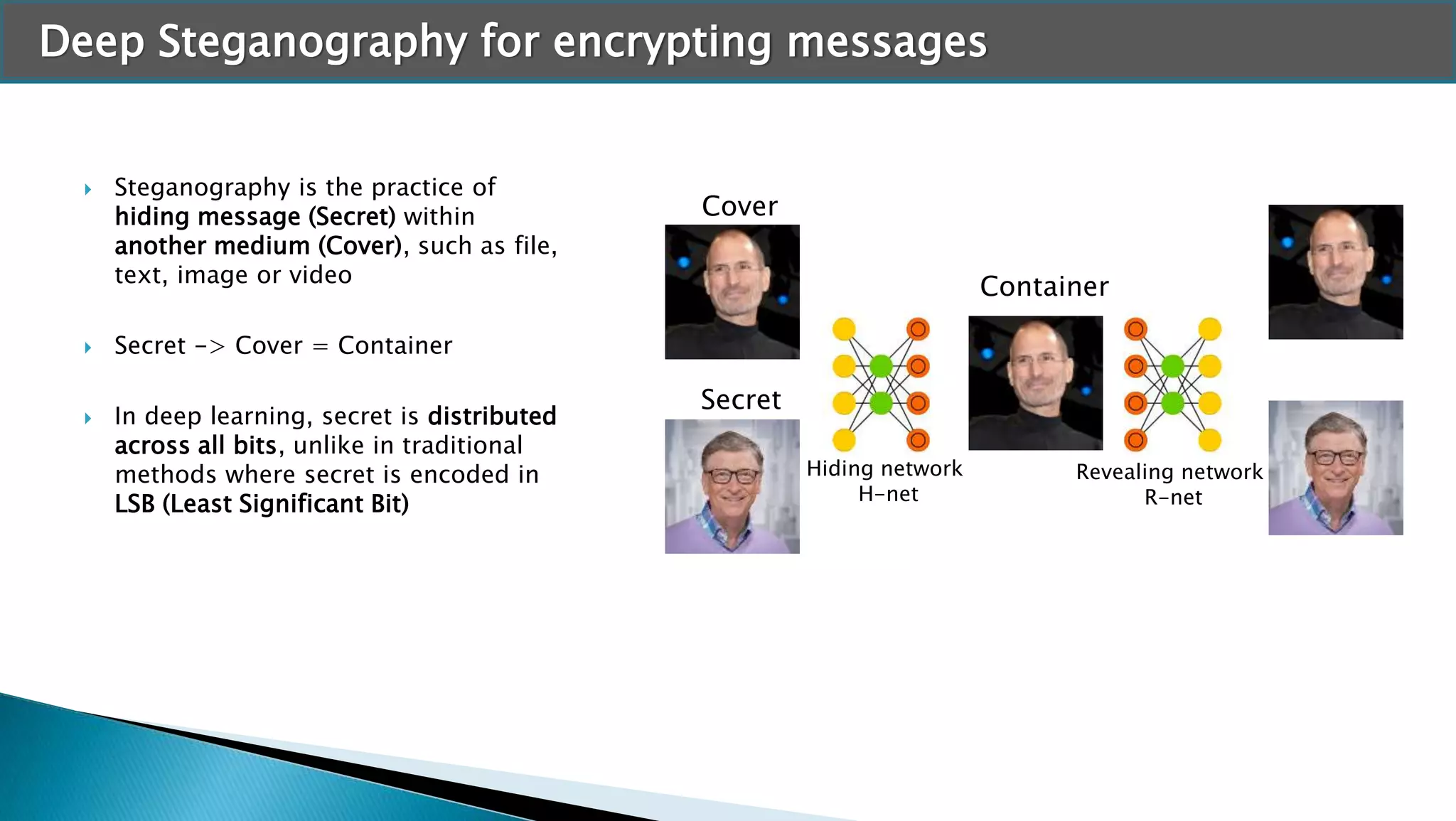
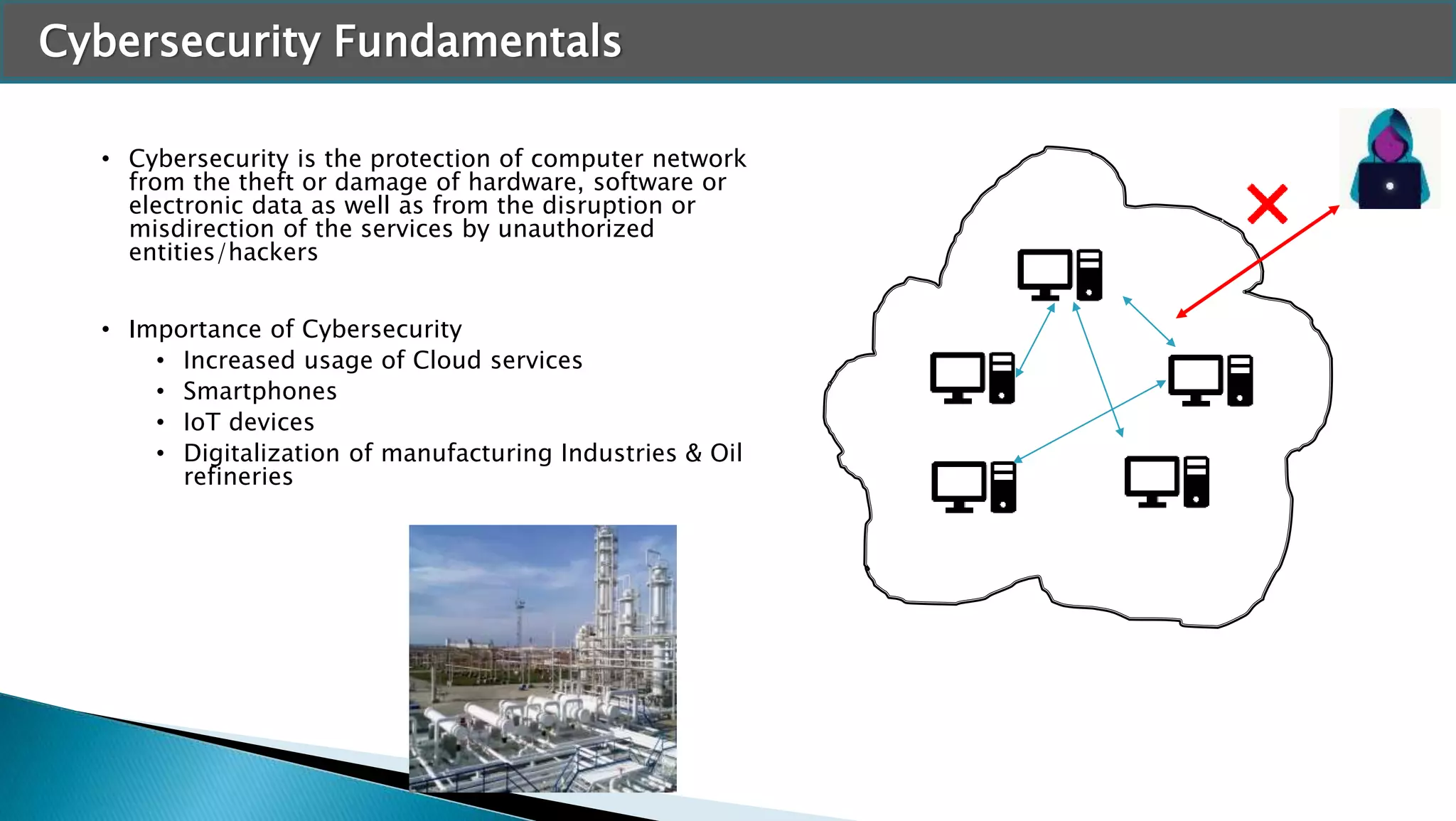
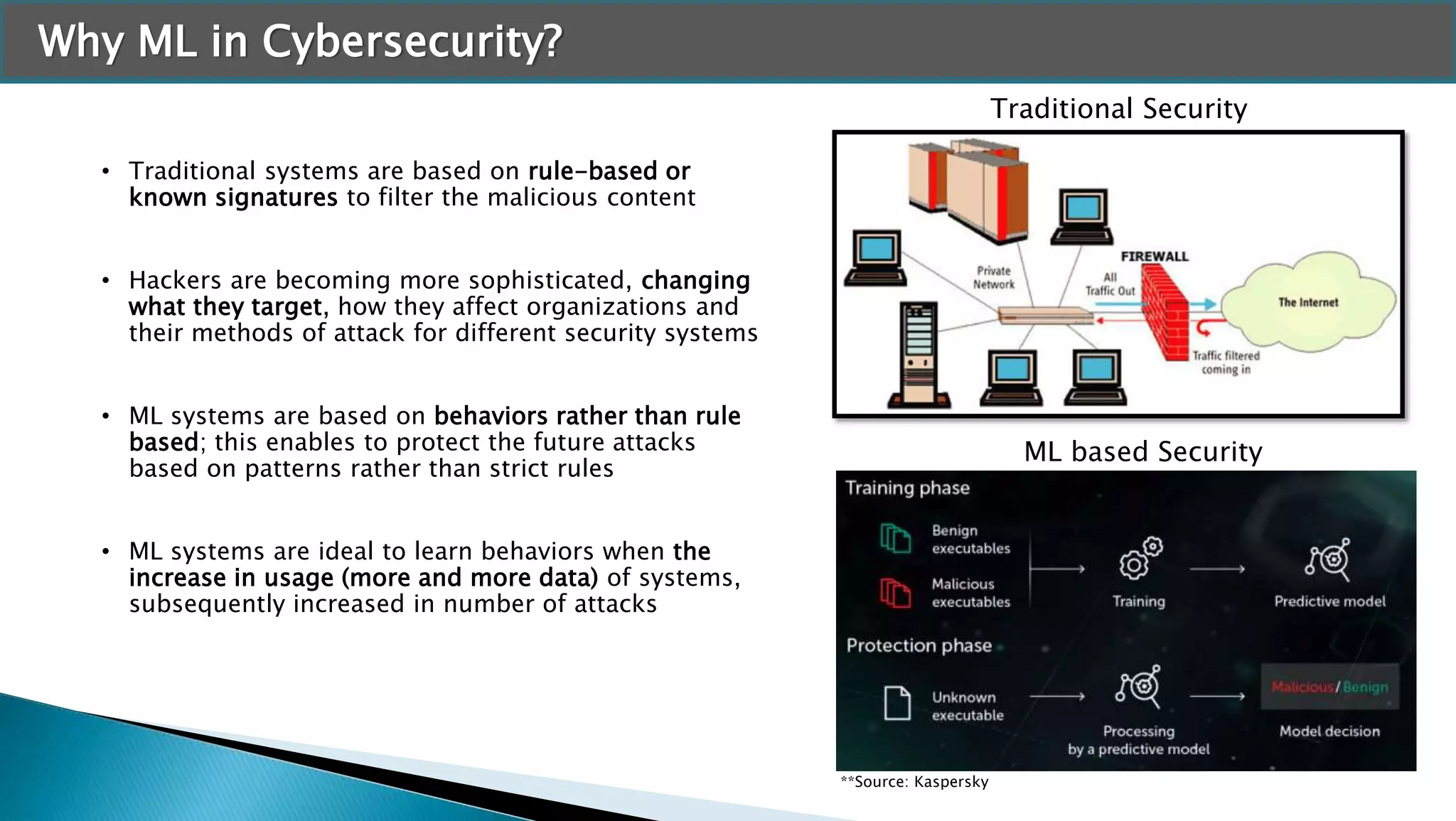
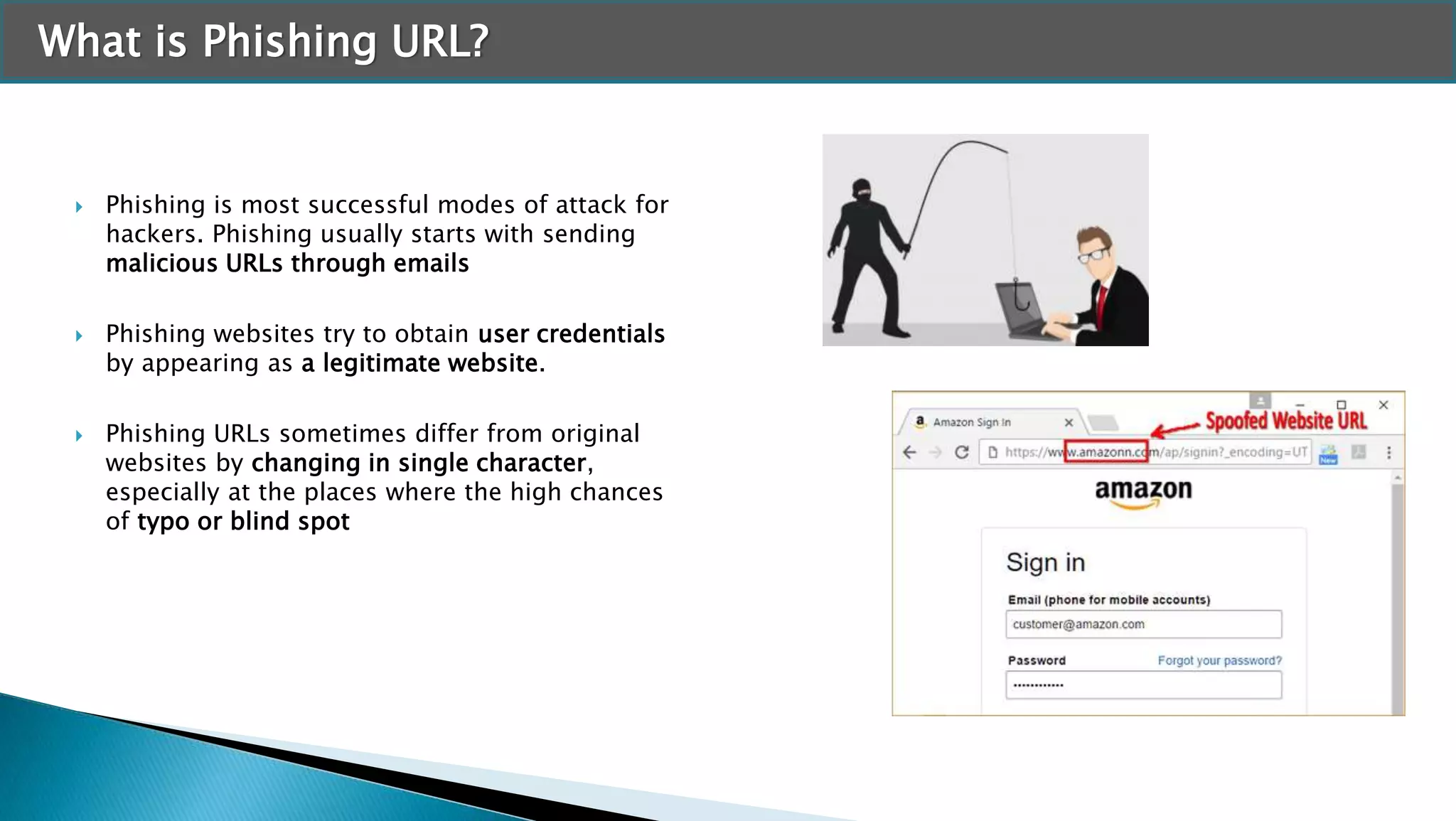
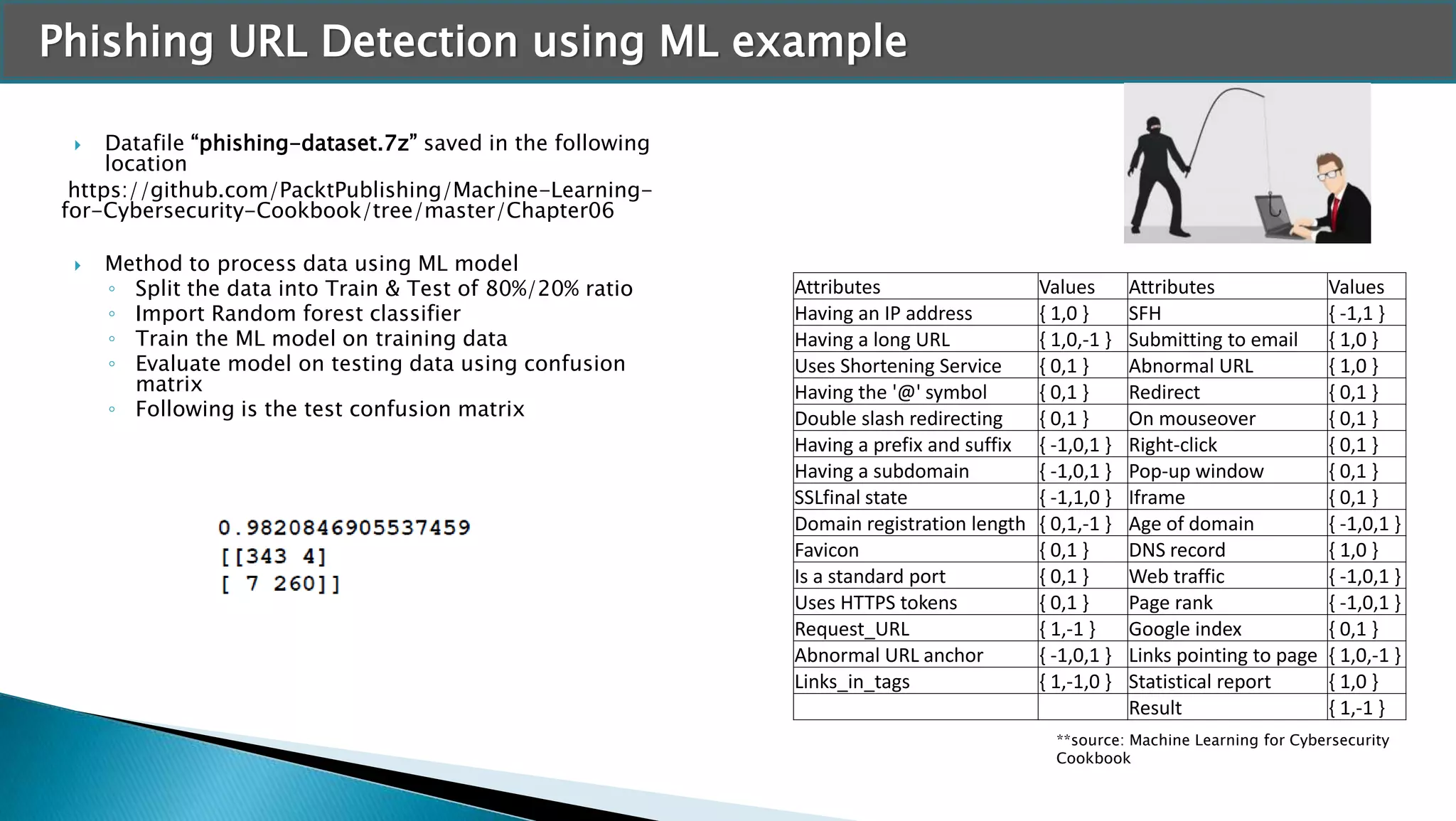
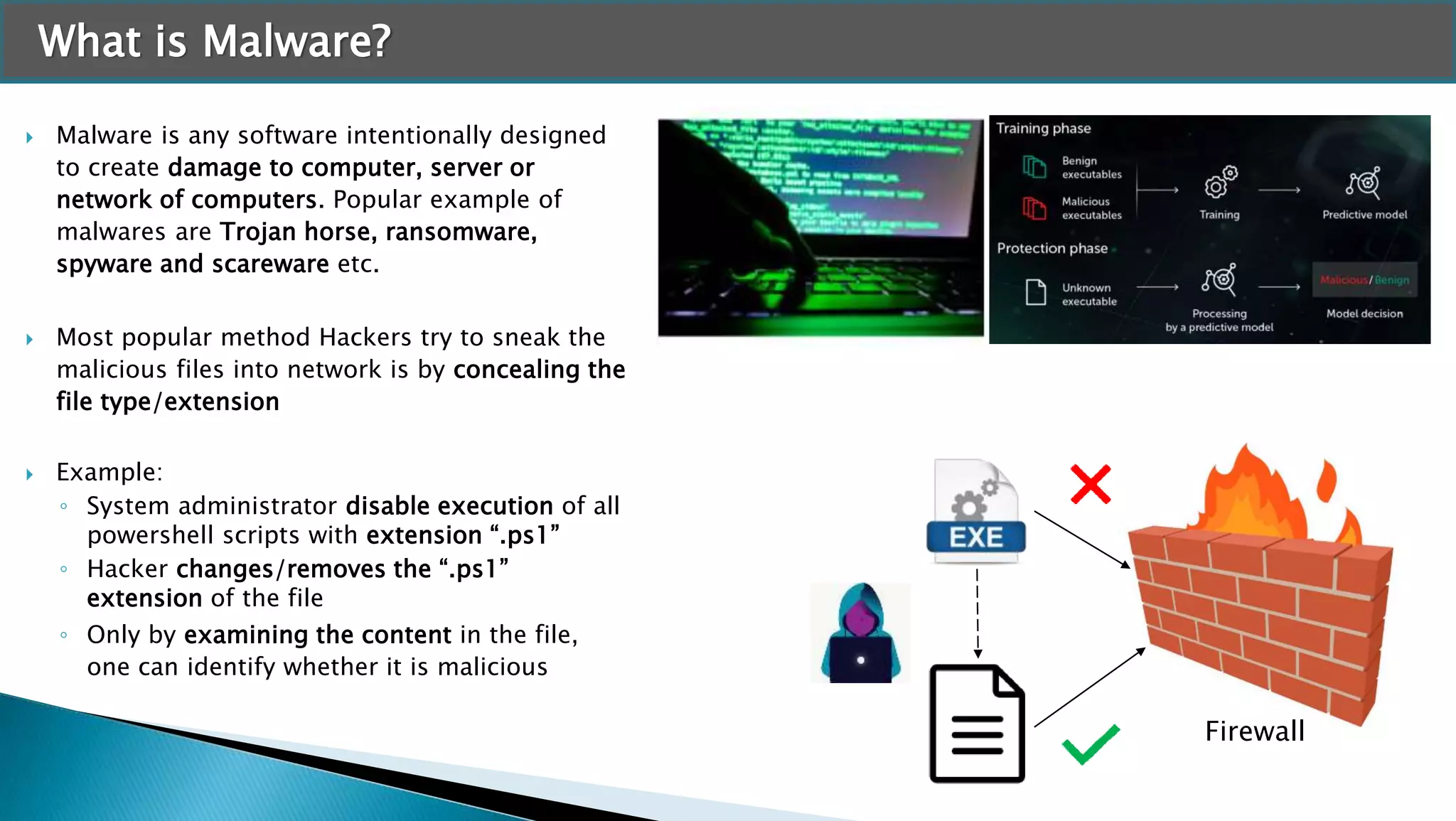
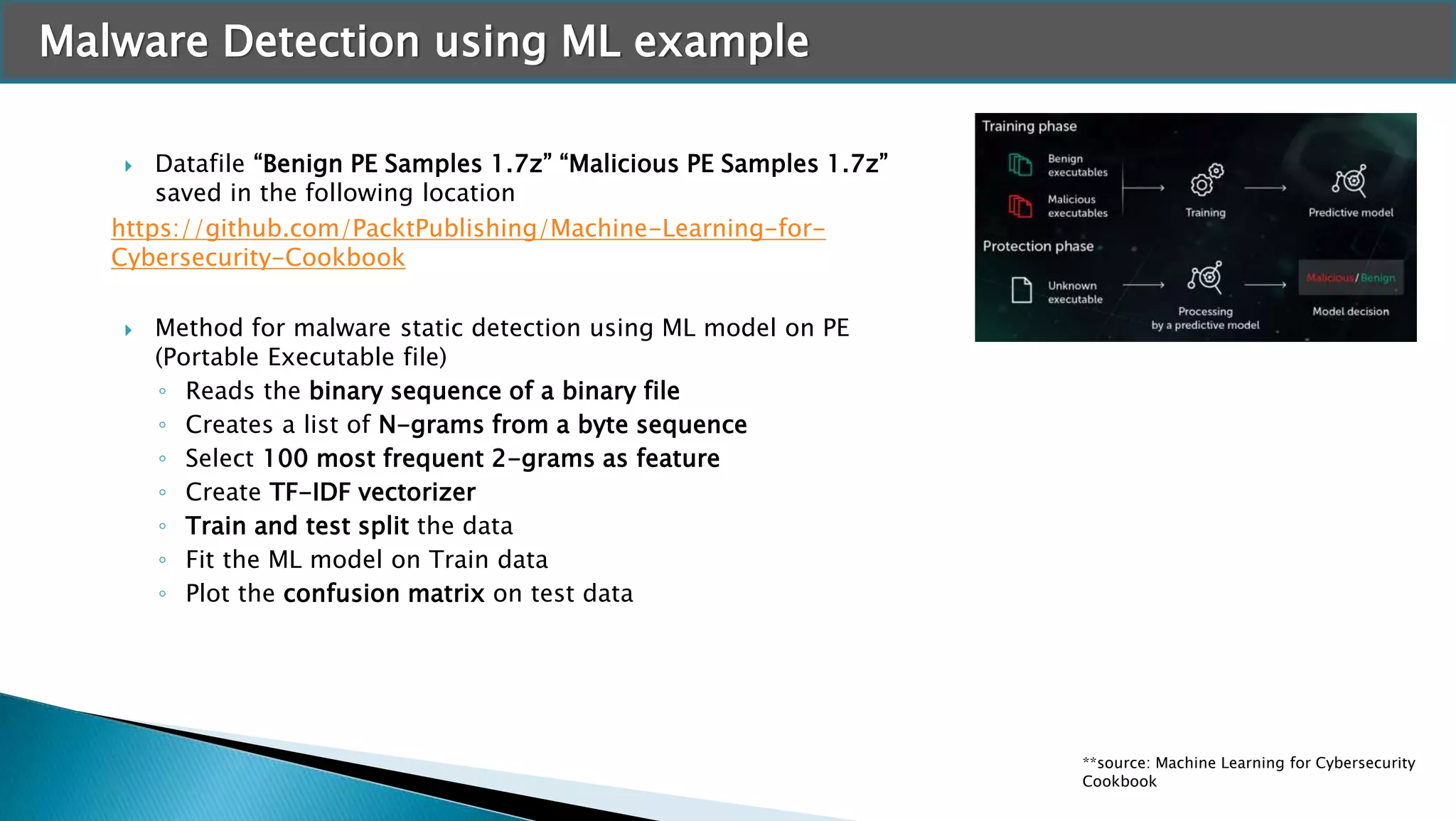
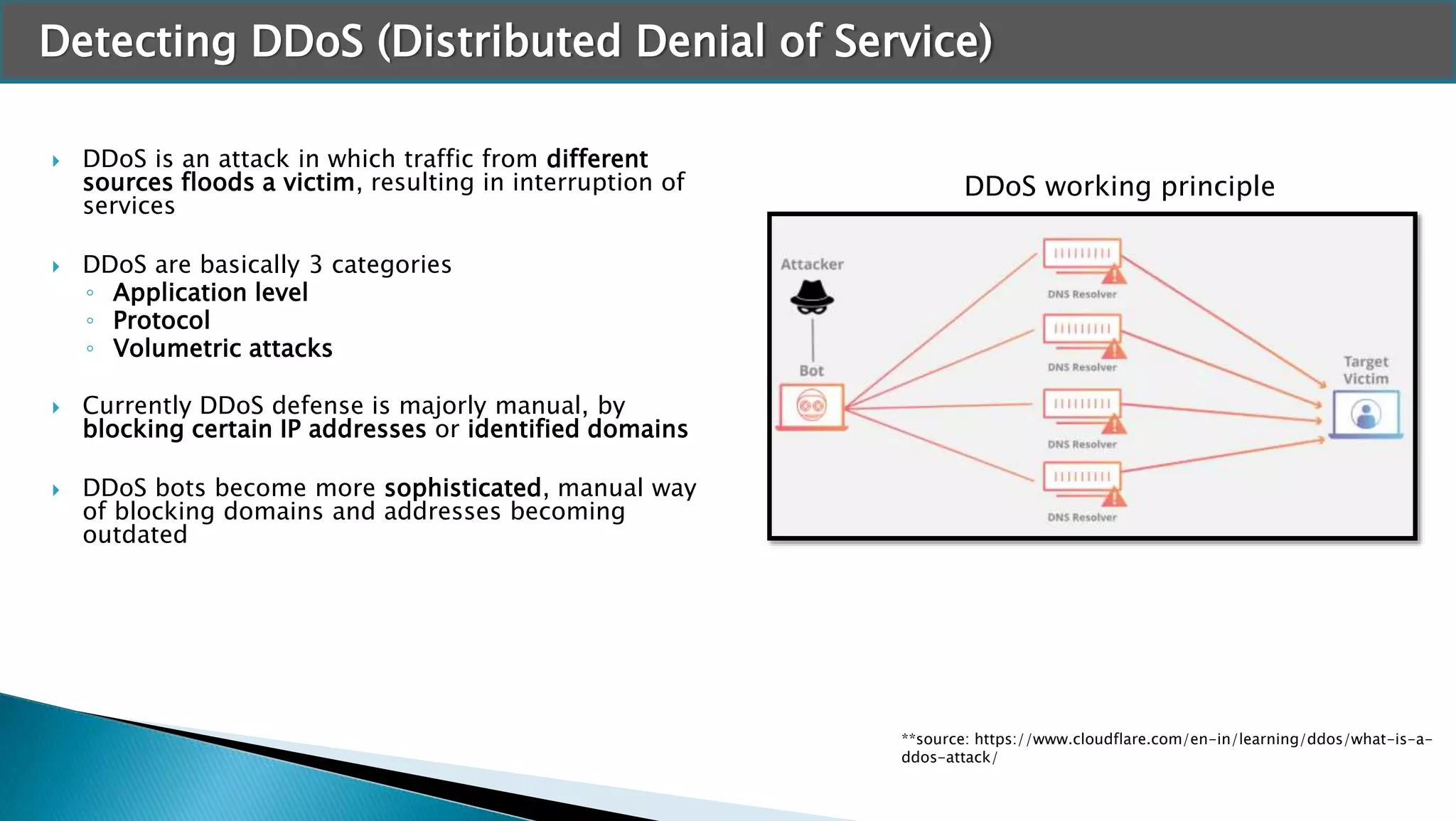
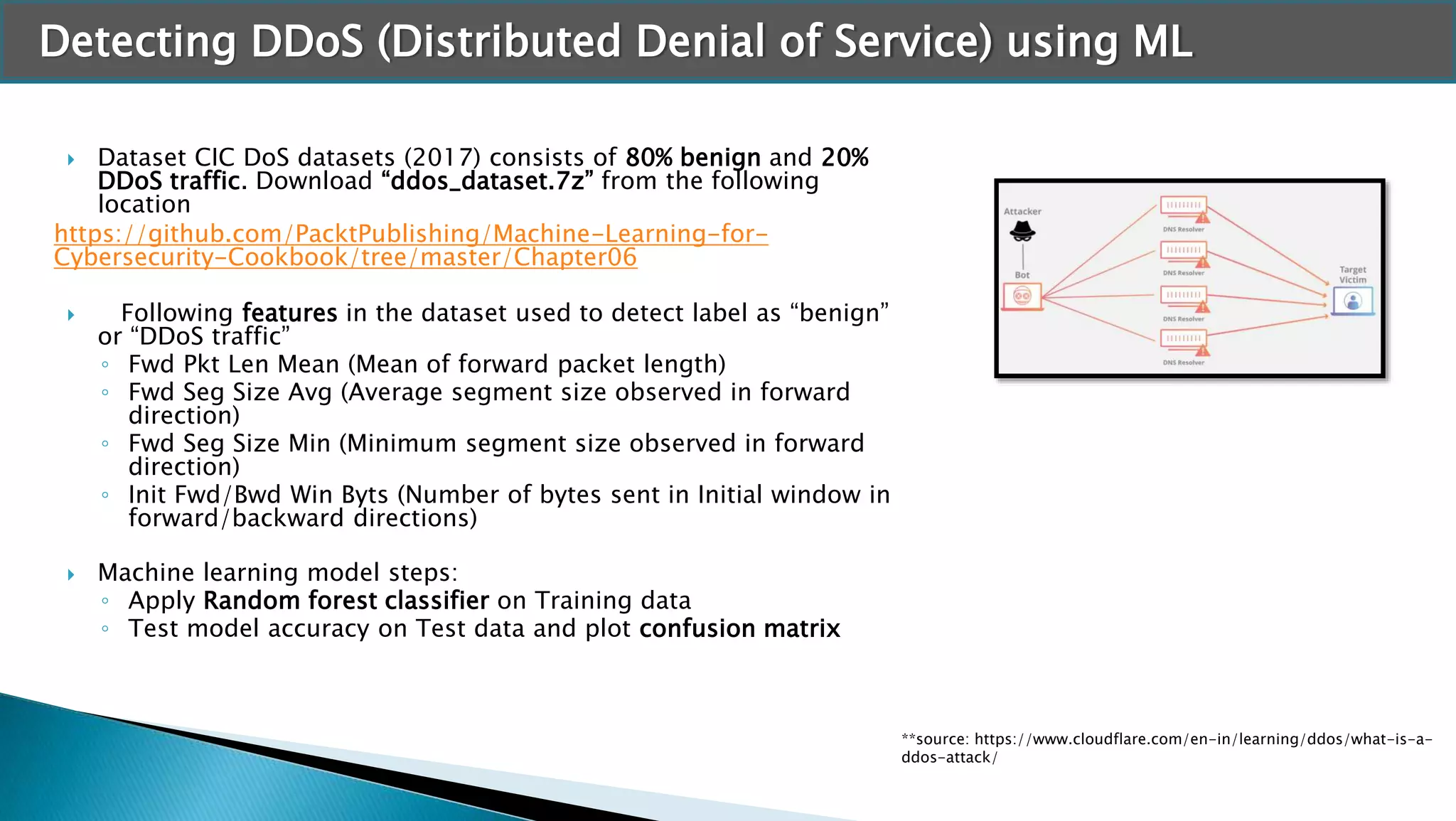
The document discusses applying machine learning techniques in cybersecurity. It provides examples of using ML for automatic intrusion detection, including phishing URL detection, malware detection, network behavior anomaly detection, and insider threat detection. Additional applications covered include assessing password strength and using deep steganography for encrypting messages. The document references several datasets and outlines the machine learning workflow and evaluation metrics for each application.

![Assessing password Strength using ML
Cracking password is the systematic endeavor of discovering the
password of a secure system
Assessing password using ML is based on training dataset
“passwordDataset.7z” https://github.com/PacktPublishing/Machine-
Learning-for-Cybersecurity-Cookbook/tree/master/Chapter07/
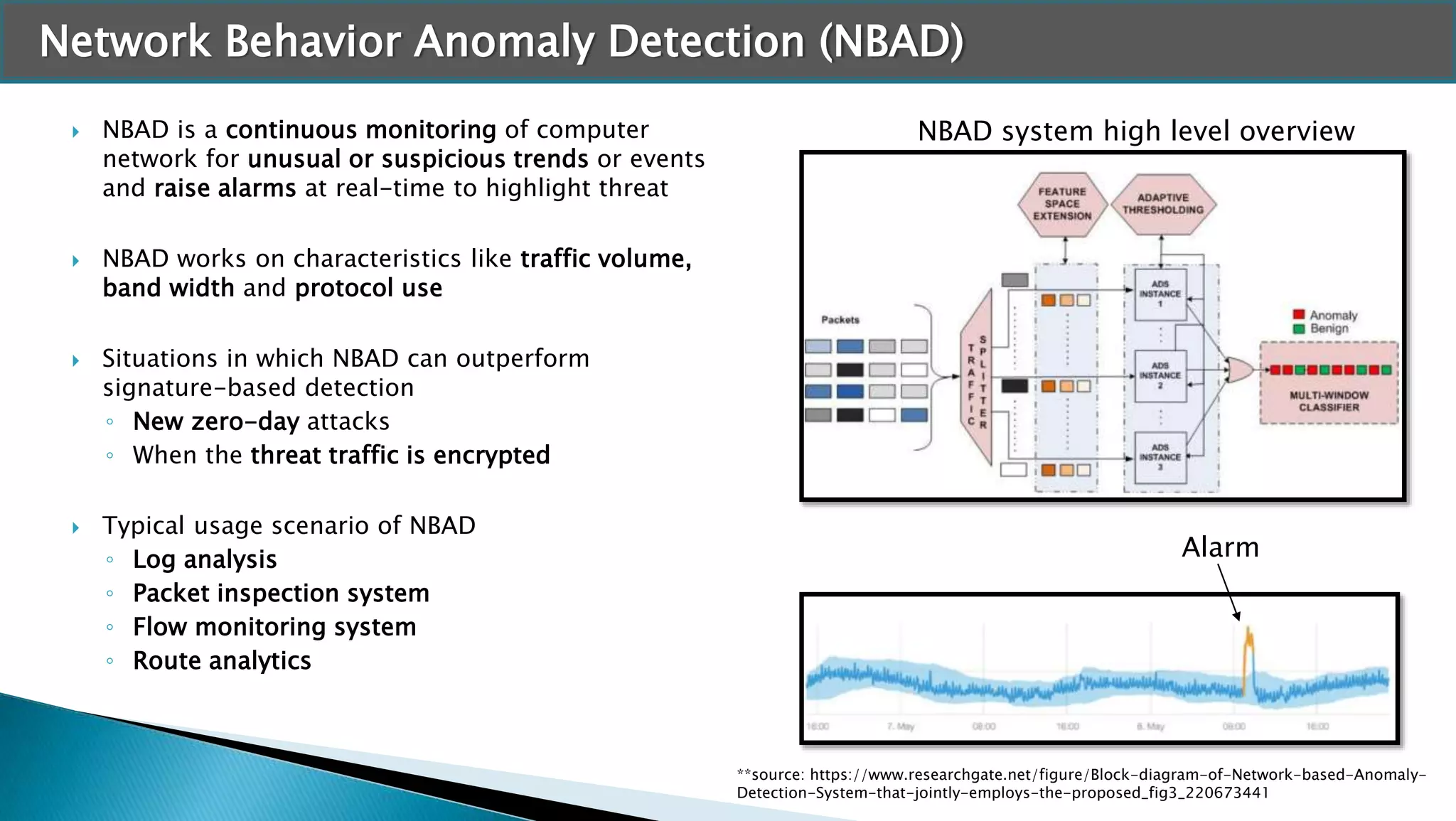
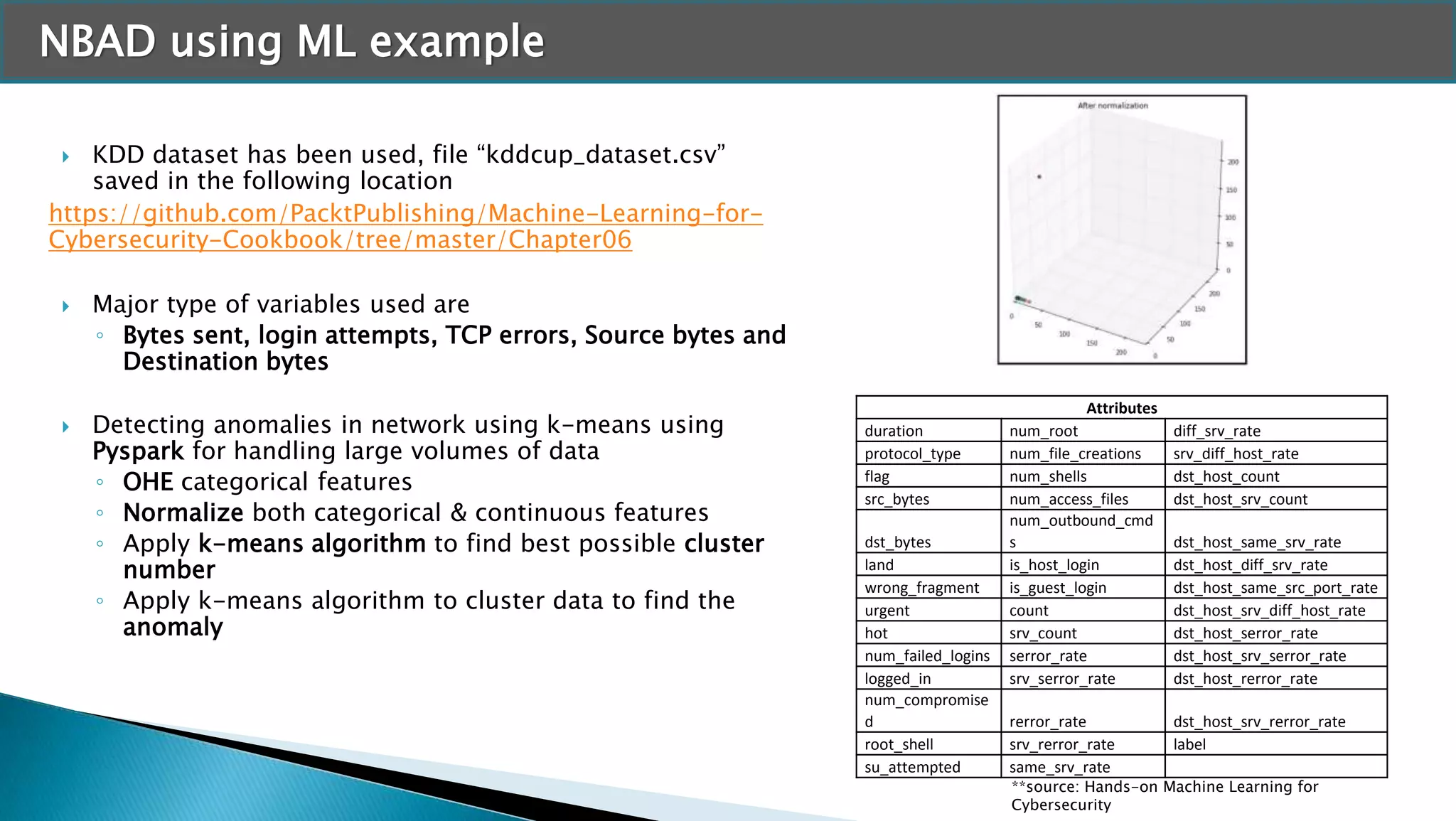
ML Methodology flow
◦ Break the password string into character level
◦ Apply TF-IDF vectorizer to convert the characters into numeric
format
◦ Split the data into Train & Test
◦ Apply XGB classifier on Train data and evaluate model on test data
**source: https://www.infosecurity-
magazine.com/blogs/password-strength-meters//
password strength
intel1 0
klara-tershina3H 2
czuodhj972 1
Trained model predicted on
1] qwerty -> 0
2] c9lCwLBFmdLbG6iWla4H -> 2
Password Dataset](https://image.slidesharecdn.com/applicationofmlcybersecuritypratap-191227073543/75/Application-of-Machine-Learning-in-Cybersecurity-15-2048.jpg)