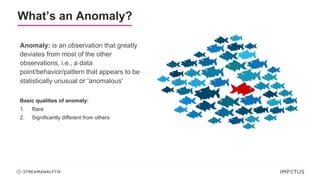
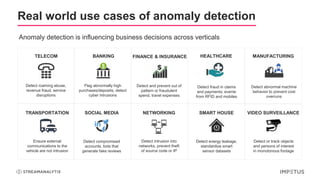
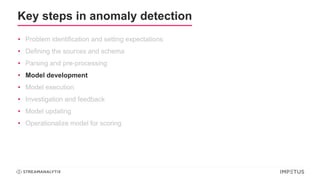
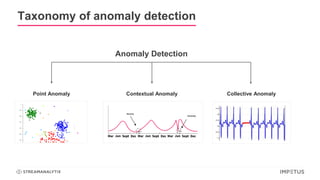
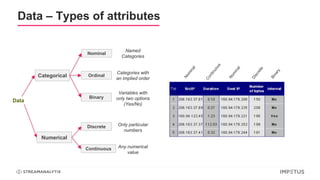
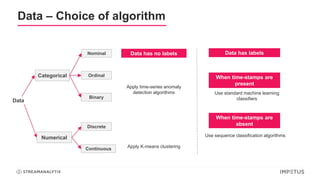
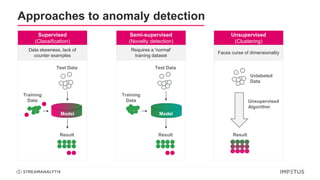
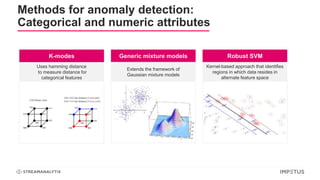
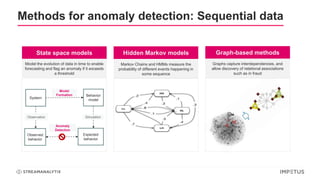
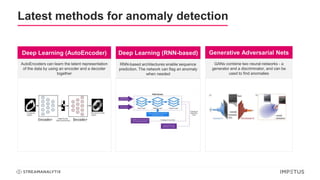
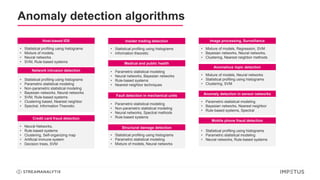
The document discusses a webinar on anomaly detection, covering its definition, real-world use cases across various industries, and key steps in building anomaly detection models. It highlights modern techniques that improve detection capabilities and the importance of real-time data processing, as well as providing details on various algorithms used for anomaly detection. Key takeaways emphasize the efficiency of modern data science methods and platforms in implementing these solutions within organizations.