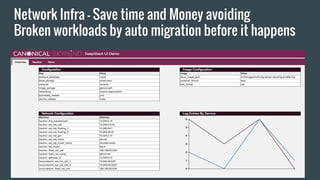
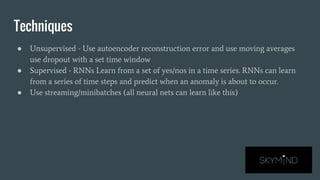
Anomaly detection in deep learning can be used for fraud detection by finding abnormal patterns in data like bad credit card transactions or fake locations. Deep learning is well-suited for anomaly detection because it can learn complex patterns from large amounts of data, represent its own features that are robust to noise, and learn cross-domain patterns. Techniques for anomaly detection include unsupervised methods using autoencoder reconstruction error and supervised methods using RNNs to learn from labeled time series data and predict anomalies. Production systems for anomaly detection can use streaming data from sources like Kafka with neural networks consuming the streaming updates.