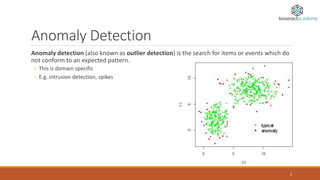
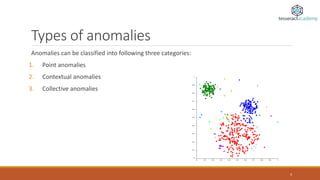
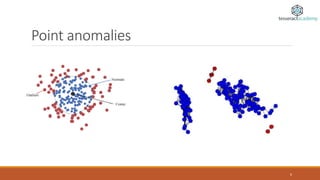
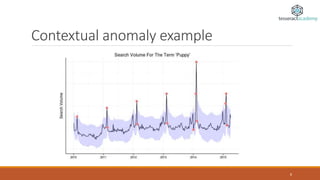
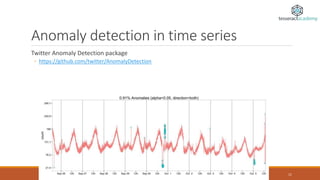
Anomaly detection, also known as outlier detection, identifies items or events that deviate from expected patterns and is applicable in various domains like intrusion detection, fraud detection, and system health monitoring. Anomalies are classified into point, contextual, and collective anomalies, each with unique characteristics and applications. Various techniques for detecting anomalies range from distance-based methods to support vector machines and neural networks.