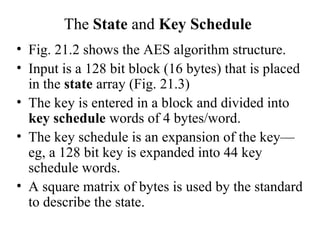
The Advanced Encryption Standard (AES) is a symmetric block cipher chosen by the U.S. government to replace the Data Encryption Standard (DES) in 2001. AES supports 128-bit blocks and key lengths of 128, 192, and 256 bits. It performs encryption and decryption through a series of transformations including substitution, shifting, mixing, and adding round keys derived from the original key. The number of transformation rounds varies based on the key length, from 10 rounds for 128-bit keys up to 14 rounds for 256-bit keys. AES provides improved security over DES with higher computational efficiency.