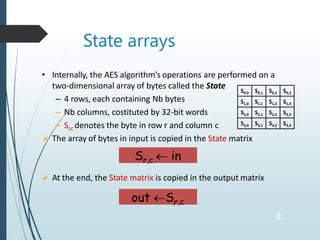
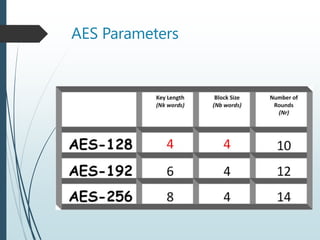
The document describes the Advanced Encryption Standard (AES) algorithm. AES is a symmetric block cipher that encrypts data blocks of 128 bits using a key of 128, 192, or 256 bits. It operates on a 4x4 matrix through a series of transformations including byte substitution, shifting rows, mixing columns, and adding a round key. The algorithm consists of 10, 12, or 14 rounds depending on the key size. AES provides security, efficiency, and flexibility for encryption.




![Round Process
In Round 2 [w8….w11] ------ K2
In Round 3[w12….w16] ------ K3
…
In Round 10[w40…w43]------K9
Total 44 words](https://image.slidesharecdn.com/aes-230214044458-0146f84e/85/AES-pptx-6-320.jpg)