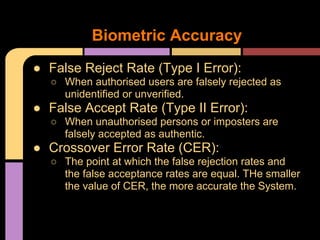
The document provides an overview of access control techniques including discretionary access controls, mandatory access controls, role-based access controls, and authentication methods like passwords, tokens, biometrics, and multifactor authentication. It discusses important access control concepts like identification, authorization, accountability, and session management. Key factors in choosing an authentication method include the value of protected assets, the threat level, potential countermeasures and costs, and usability. Maintaining accountability requires strong identification, authentication, monitoring, auditing, policies, and an organizational culture that enforces responsibility.