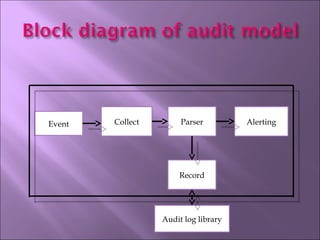
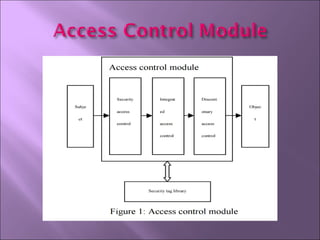
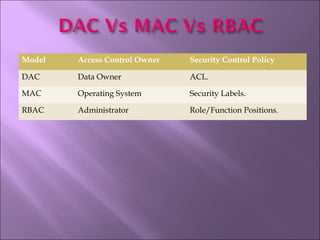
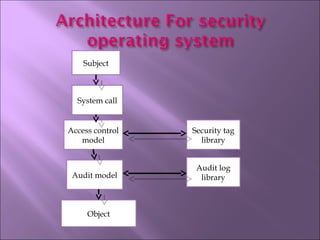
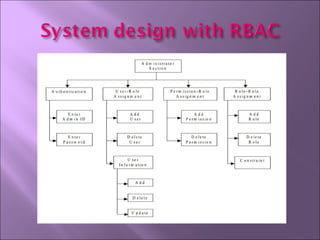
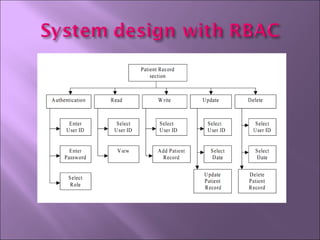
The document discusses security mechanisms in Linux operating systems. It covers access control modules, including audit, access control, and role-based access control modules. It also discusses security models like DAC, MAC, RBAC and how they integrate with the operating system's security tag library and audit log. The principles of least privilege, separation of duties and simplicity are important to the design.