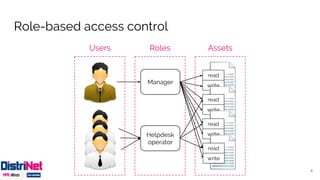
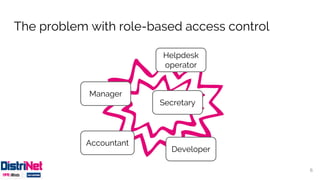
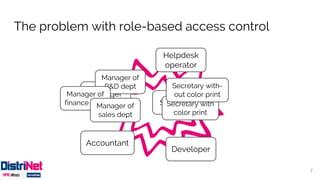
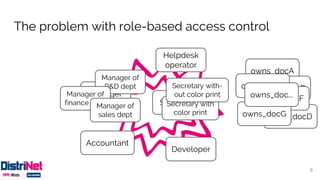
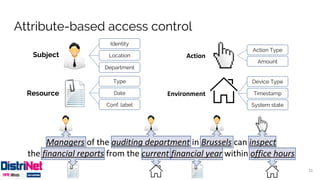
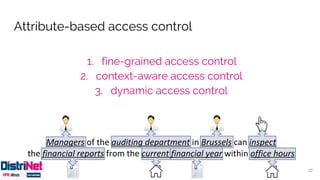
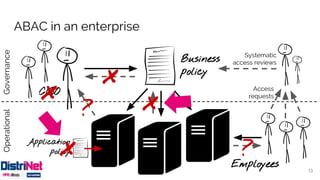
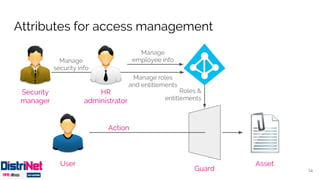
The document discusses various access control models, emphasizing attribute-based access control (ABAC) as a flexible alternative to traditional role-based approaches. It highlights the challenges of role-based access control, such as role explosion, and presents the advantages of ABAC, including fine-grained and dynamic access control. The conclusion mentions the need for careful planning and incremental implementation when transitioning to ABAC in enterprises.


![1. Attributes can be fetched remotely = good for federated applications
2. You do not need the identity of the subject = good for privacy
3. As a researcher, it looks future-proof
a. ABAC supports many advanced policies, e.g., history-based policies, dynamic separation
of duty and breaking-the-glass procedures, …
b. Many of the newest access control models can be mapped on attributes, e.g., ReBAC,
EBAC [Bogaerts2015], obligations [Park2004], ...
c. A lot is still happening in this field, e.g., formal definition of this model and its properties (e.g.,
[Jin2012a]), languages for expressing attribute-based rules (e.g., [XACML, Crampton2012]), mutable
attributes (e.g., [Park2004]), attribute aggregation in federated identity management (e.g.,
[Chadwick2009]), encryption of attributes (e.g., [Asghar2011]), policy engineering for ABAC (e.g..,
[Krau2013]), performance (e.g., [Brucker2010]), …
Attributes as an enabler for the future
16](https://image.slidesharecdn.com/attribute-basedaccesscontrol-160622101858/85/Attribute-based-access-control-16-320.jpg)

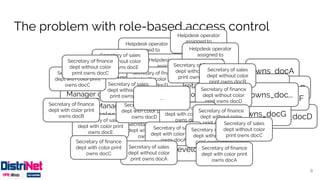
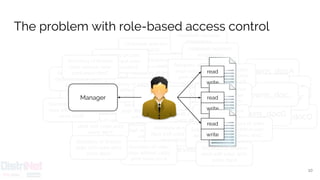
![Migrating from RBAC to ABAC
Conceptually, three approaches:
18
[Kuhn2010]
2. Dynamic roles1. Roles as an attribute 3. Constrain roles
Manager
Helpdesk
operator
Accountant
Secretary
subject.roles
owns_doc...
Identity
Location
Department
Manager
Helpdes
k
operator
Accountant
Secretar
y
owns_doc...
Identity
Location
Department
Manager
A.read B.read
B.write ...](https://image.slidesharecdn.com/attribute-basedaccesscontrol-160622101858/85/Attribute-based-access-control-18-320.jpg)

![20
Source: [NIST2014]](https://image.slidesharecdn.com/attribute-basedaccesscontrol-160622101858/85/Attribute-based-access-control-20-320.jpg)

![22
Establish a
business case for
ABAC
Understand your
operational
requirements
Technical
implementation
Deploy or adjust
business
processes
Source: [NIST2014]
Initiation Implementation Maintenance Disposal
Ensure quality
Migrating from RBAC to ABAC, revised](https://image.slidesharecdn.com/attribute-basedaccesscontrol-160622101858/85/Attribute-based-access-control-22-320.jpg)
![23
Establish a
business case for
ABAC
Understand your
operational
requirements
Technical
implementation
Deploy or adjust
business
processes
Source: [NIST2014]
Initiation Implementation Maintenance Disposal
Ensure quality
Migrating from RBAC to ABAC, revised
Work incrementally
You probably already have
many of the required
processes](https://image.slidesharecdn.com/attribute-basedaccesscontrol-160622101858/85/Attribute-based-access-control-23-320.jpg)



![References
[Asghar2011] Asghar, Muhammad Rizwan, et al. "Espoon: Enforcing encrypted security policies in outsourced
environments." 2011
[Bogaerts2015] Bogaerts, Jasper, et al. "Entity-Based Access Control: supporting more expressive access control
policies." 2015.
[Brucker2010] Brucker, Achim D., and Helmut Petritsch. "Idea: efficient evaluation of access control constraints." 2010
[Chadwick2009] Chadwick, David W., and George Inman. "Attribute aggregation in federated identity management."
2009
[Crampton2012] Crampton, Jason, and Charles Morisset. "PTaCL: A language for attribute-based access control in open
systems." 2012
[Fong2011] Fong, Philip WL. "Relationship-based access control: protection model and policy language." ACM, 2011.
27](https://image.slidesharecdn.com/attribute-basedaccesscontrol-160622101858/85/Attribute-based-access-control-27-320.jpg)
![References (continued)
[Fong2011] Fong, Philip WL. "Relationship-based access control: protection model and policy language." ACM, 2011.
[Jin2012a] Jin, Xin, Ram Krishnan, and Ravi S. Sandhu. "A Unified Attribute-Based Access Control Model Covering DAC,
MAC and RBAC." 2012
[Jin2012b] Jin, Xin, Ravi Sandhu, and Ram Krishnan. "RABAC: role-centric attribute-based access control." 2012
[Krau2013] Krautsevich, Leanid, et al. "Towards policy engineering for attribute-based access control." 2013
[Kuhn2010] Kuhn, D. Richard, Edward J. Coyne, and Timothy R. Weil. "Adding attributes to role-based access control."
2010
[Park2004] Park, Jaehong, and Ravi Sandhu. "The UCON ABC usage control model." 2004
[XACML] eXtensible Access Control Markup Language (XACML) Version 3.0. 2013. OASIS Standard
28](https://image.slidesharecdn.com/attribute-basedaccesscontrol-160622101858/85/Attribute-based-access-control-28-320.jpg)
