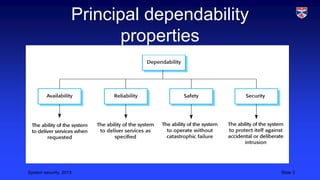
The document discusses system security and defines key related terms. System security is the ability of a system to protect itself from accidental or deliberate attacks. It is essential for availability, reliability, and safety as most systems are networked. Without proper security, systems are vulnerable to damage like denial of service, data corruption, and disclosure of confidential information. Security can be achieved through strategies such as avoiding vulnerabilities, detecting and eliminating attacks, and limiting exposure and enabling recovery from successful attacks.