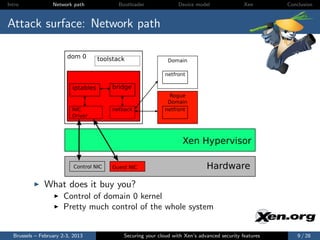
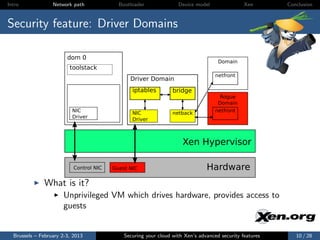
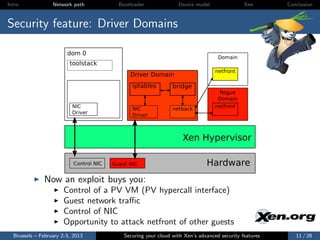
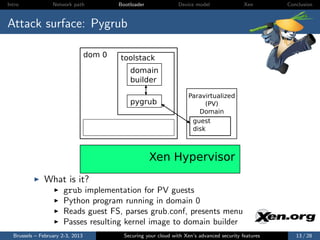
The document discusses the advanced security features of the Xen hypervisor, including driver domains, pvgrub, and stub domains, emphasizing the importance of understanding these features to secure cloud environments. It also outlines various attack surfaces and security considerations, such as threat models and best practices for implementing security measures. Ultimately, it aims to equip users with knowledge on managing security effectively within Xen architectures.





![Intro Network path Bootloader Device model Xen Conclusion
HowTo: Driver Domains
Create a VM with appropriate drivers
Any distro supporting dom0 should do
Install the xen-related hotplug scripts
Just installing the xen tools in the VM is usually good enough
Give the VM access to the physical NIC with PCI pass-through
Configure the network topology in the driver domain
Just like you would for dom0
Configure the guest vif to use the new domain ID
Add backend=domnet to vif declaration
vif = [ ’type=pv, bridge=xenbr0, backend=domnet’ ]
http://wiki.xen.org/wiki/Driver Domain
Brussels – February 2-3, 2013 Securing your cloud with Xen’s advanced security features 12 / 28](https://image.slidesharecdn.com/talk-130203020019-phpapp01/85/Securing-your-cloud-with-Xen-s-advanced-security-features-12-320.jpg)
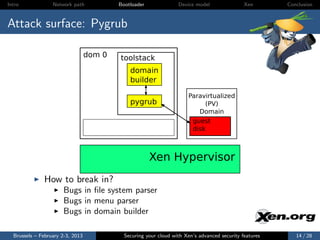
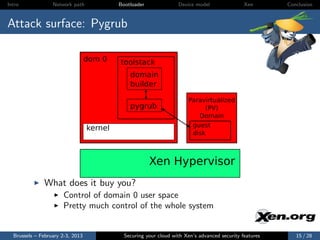
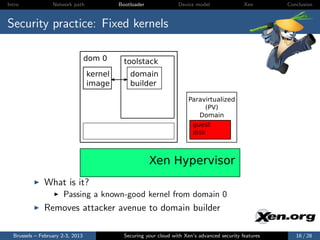
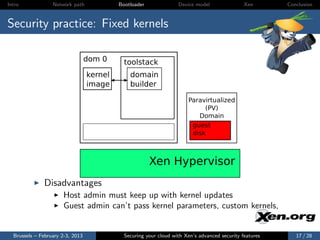
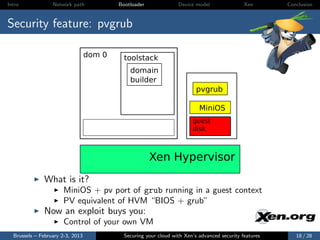


![Intro Network path Bootloader Device model Xen Conclusion
HowTo: Use the example FLASK policy
Build Xen with XSM enabled
Build the example policy
Add the appropriate label to guest config files
seclabel=[foo]
stubdom label=[foo]
WARNING: In 4.2, the example policy not extensively tested.
Use with care!
http://wiki.xen.org/wiki/Xen Security Modules : XSM-
FLASK
Brussels – February 2-3, 2013 Securing your cloud with Xen’s advanced security features 25 / 28](https://image.slidesharecdn.com/talk-130203020019-phpapp01/85/Securing-your-cloud-with-Xen-s-advanced-security-features-25-320.jpg)