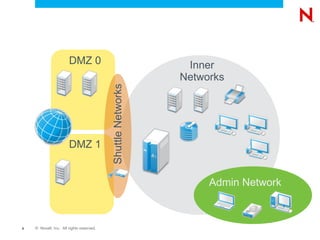
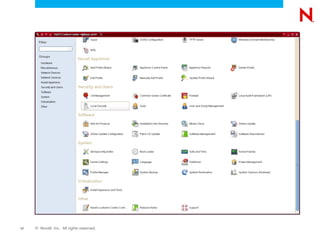
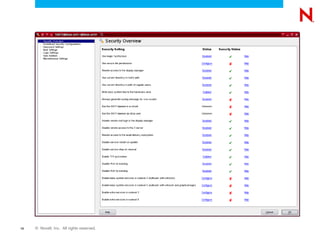
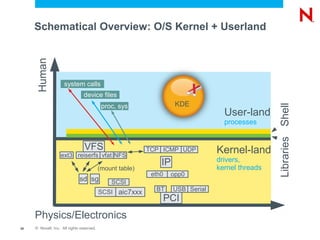
The document discusses securing and hardening a SUSE Linux Enterprise Server, emphasizing that software should be secure by functioning correctly without vulnerabilities. It outlines strategies for administration, infrastructure security, service management, and process inspection to mitigate risks and enhance system integrity. Additionally, it provides tools like YaST, AppArmor, Wireshark, and Nmap for monitoring and improving system security.