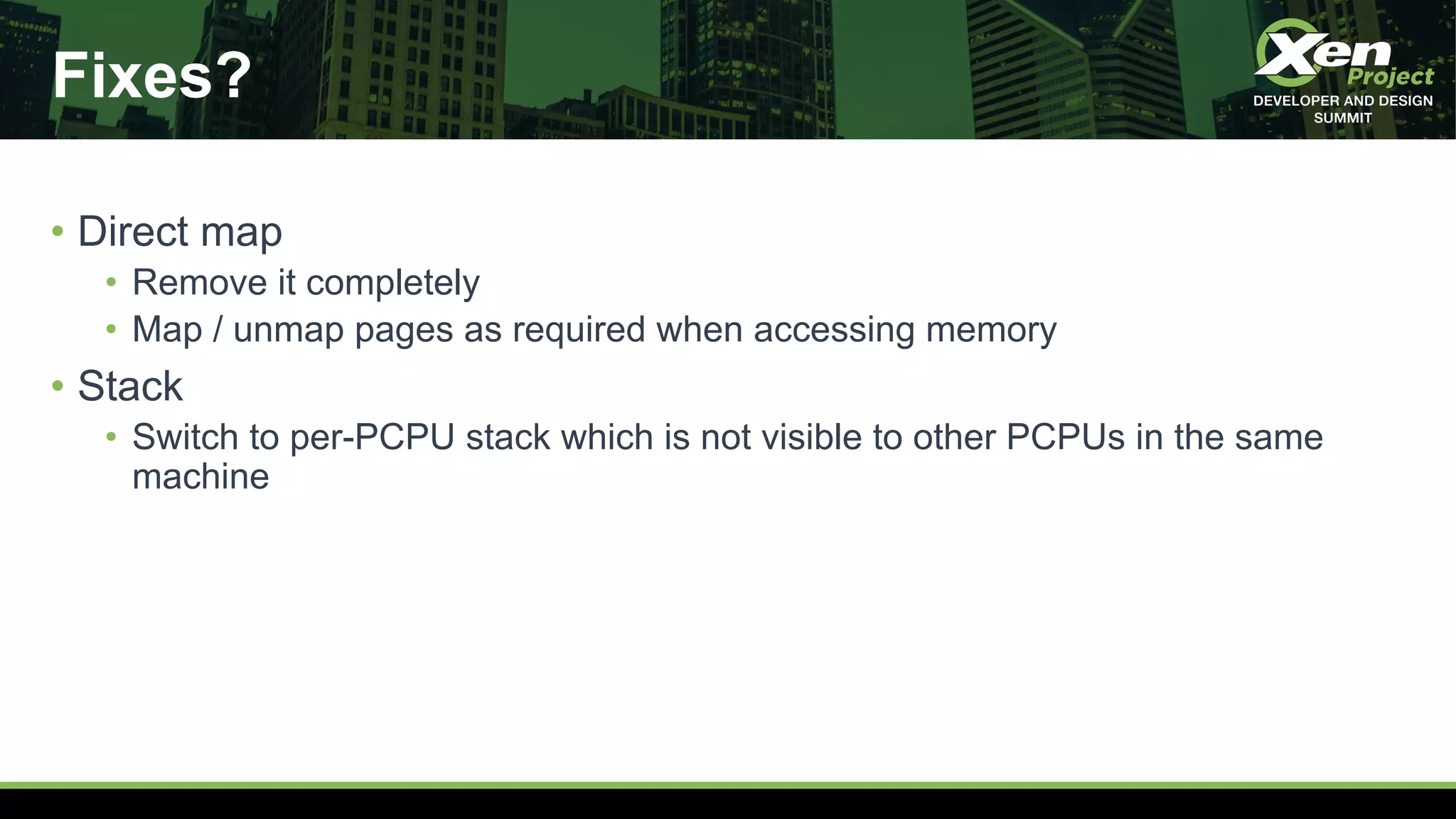
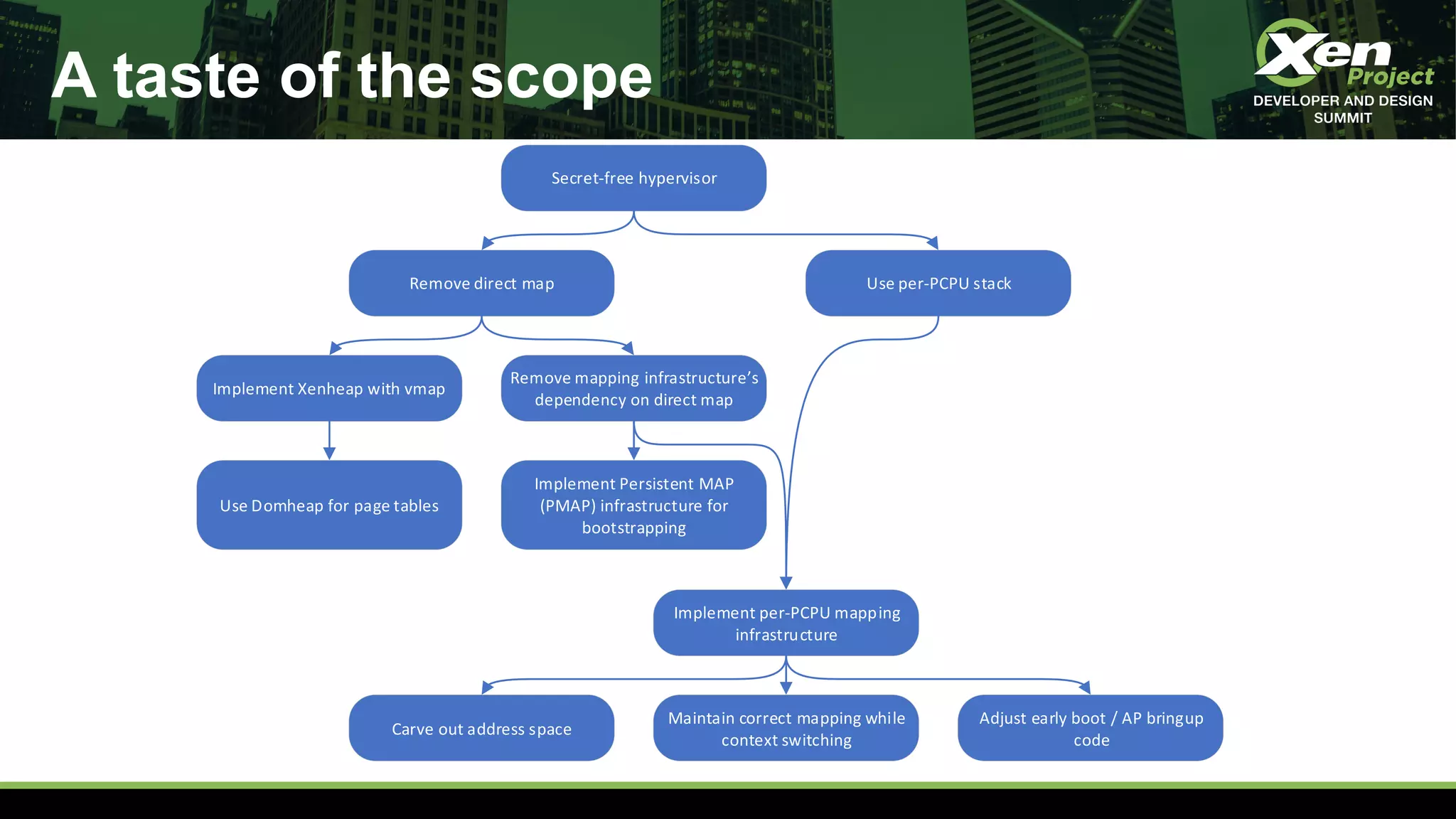
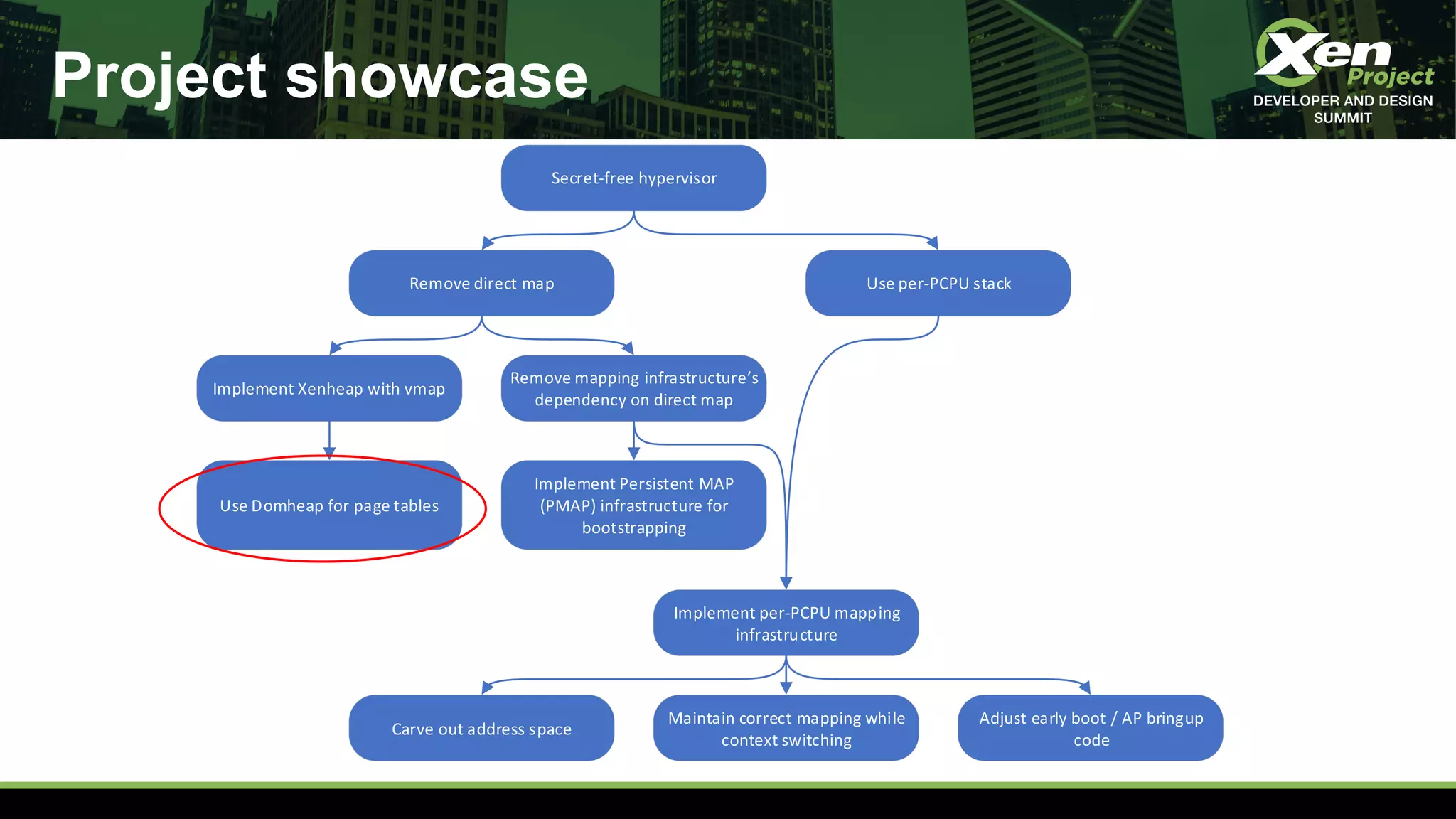
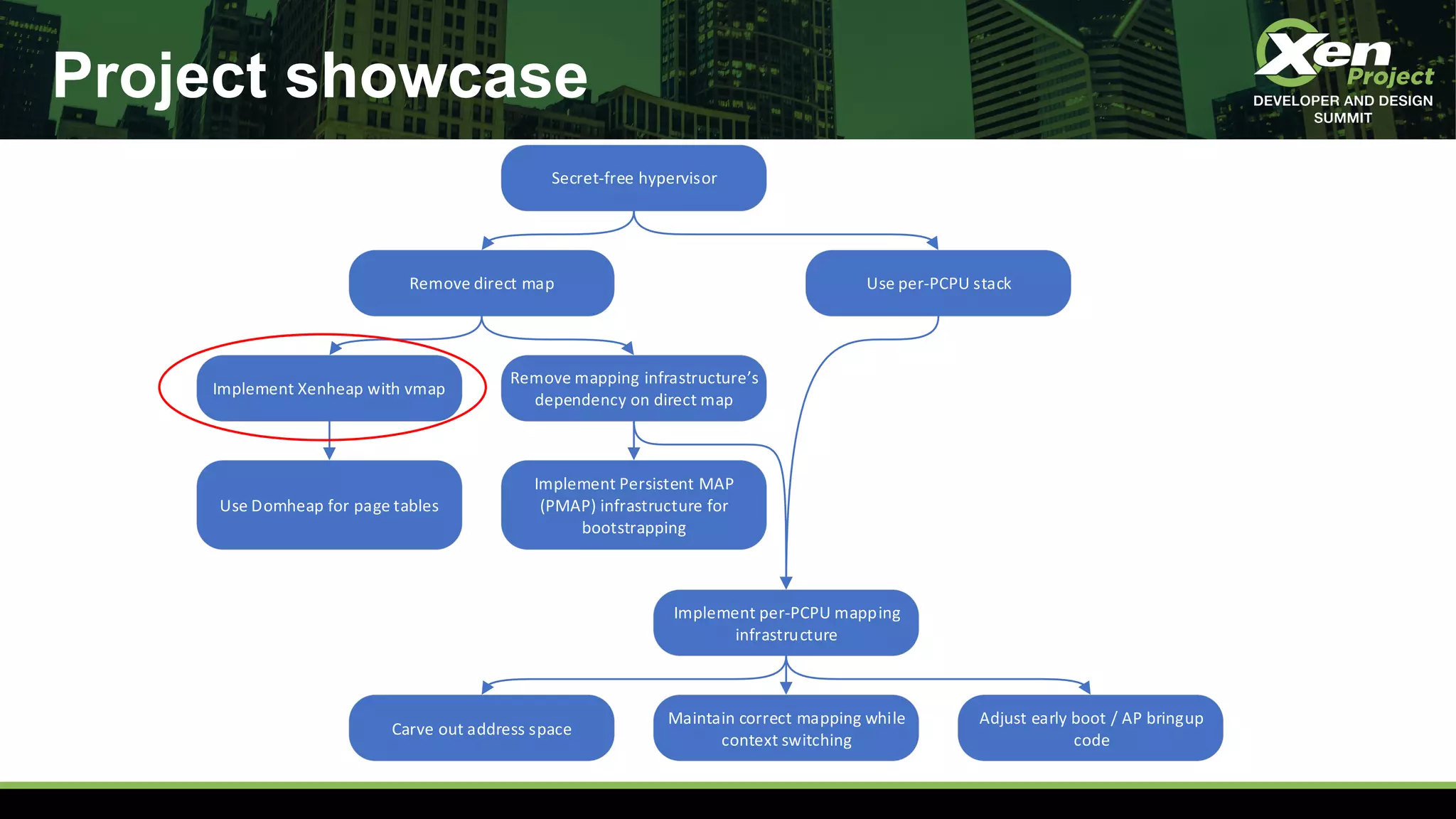
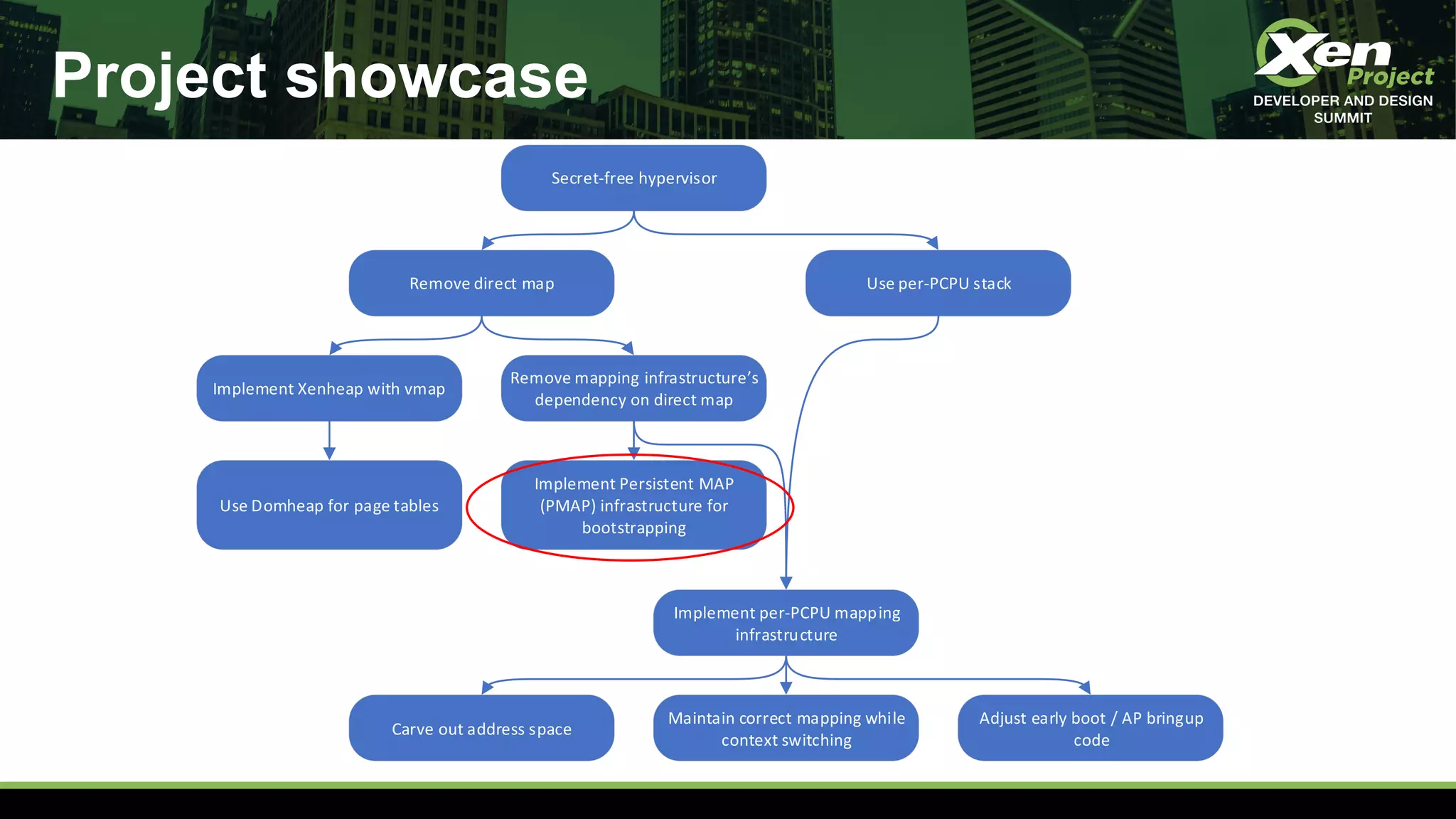
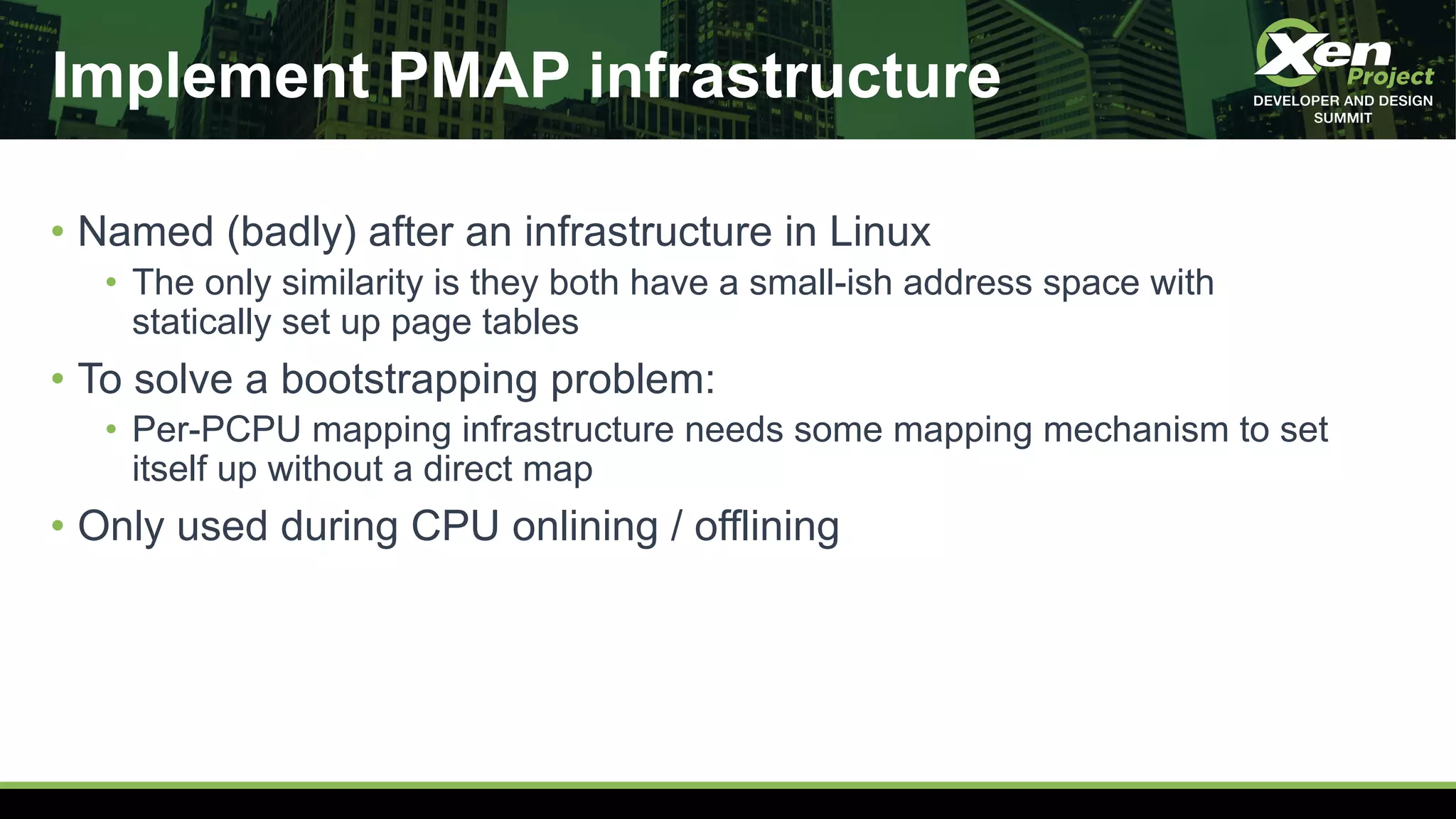
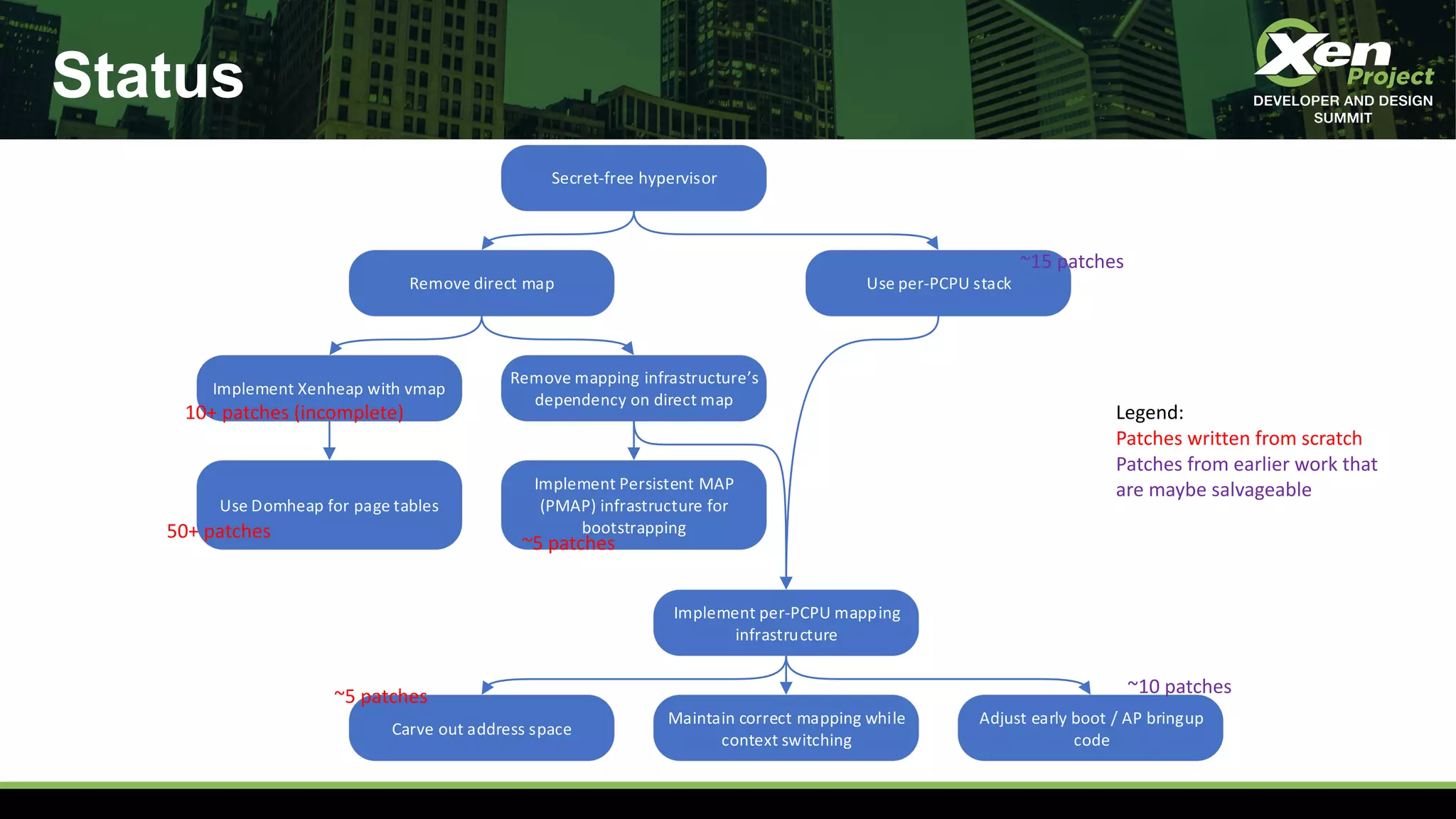
The document discusses the development of a secret-free hypervisor prompted by issues like Meltdown and Spectre, focusing on rethinking Xen's strategy to eliminate sensitive data leaks. Key targets include removing direct memory mapping, implementing per-CPU stacks, and redefining the memory allocation structure within Xen. The project involves extensive code revisions and patch development to enhance security while maintaining performance.