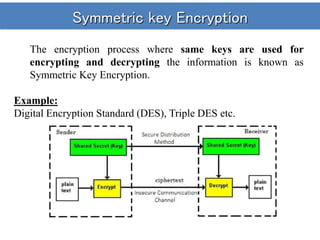
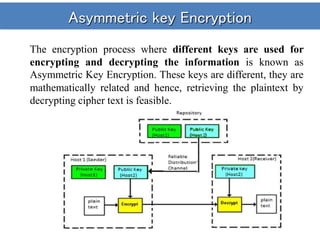
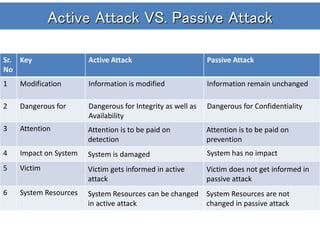
The document discusses different types of cryptosystems and cryptographic attacks. It describes symmetric key encryption, which uses the same key to encrypt and decrypt, and asymmetric key encryption, which uses different but mathematically related public and private keys. It also outlines various assumptions an attacker may make and different attack methods, including ciphertext-only attacks, known plaintext attacks, chosen plaintext attacks, and dictionary attacks. The goal of an attacker is to break the cryptosystem and determine the secret key in order to decrypt ciphertext.