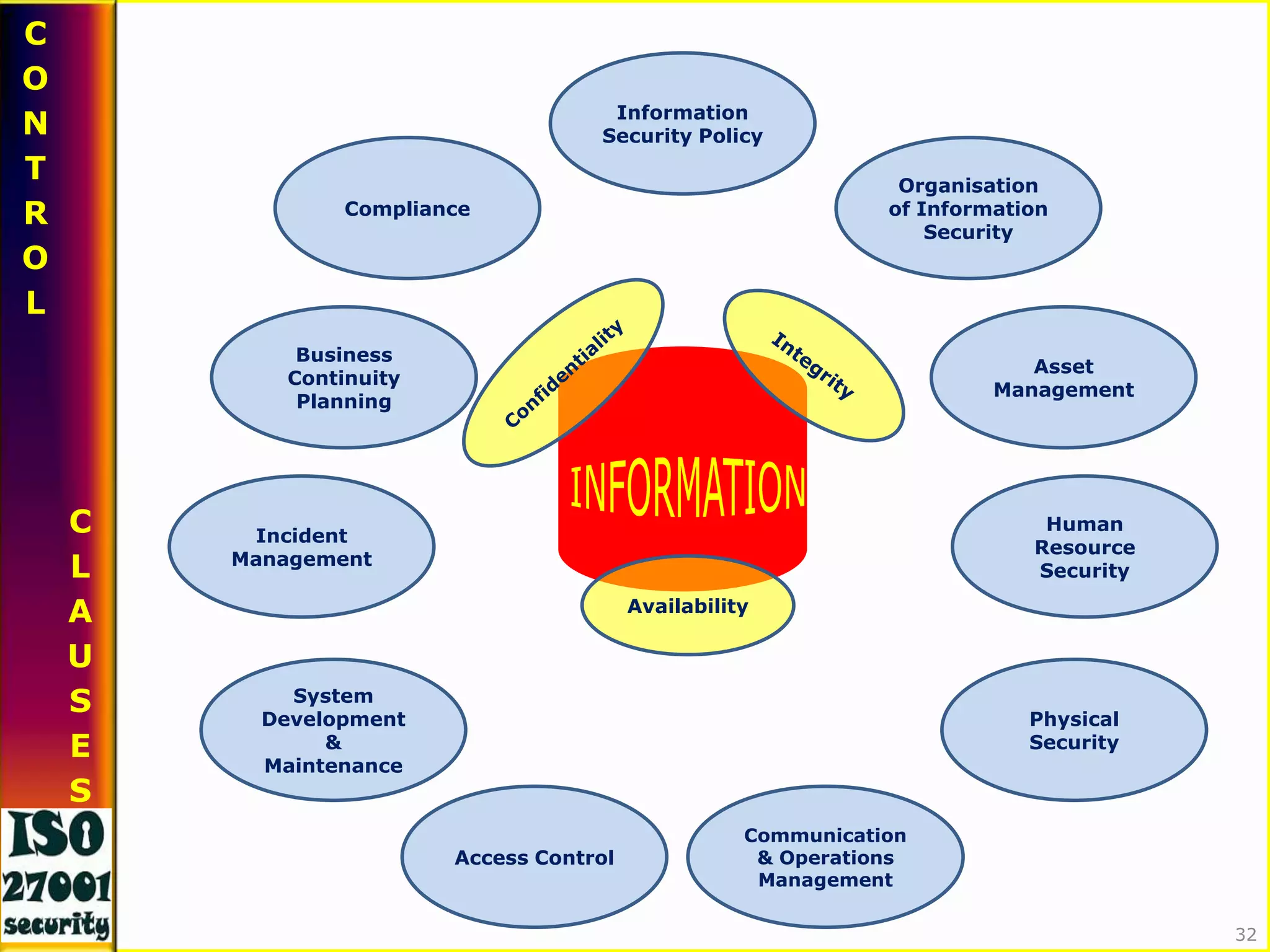
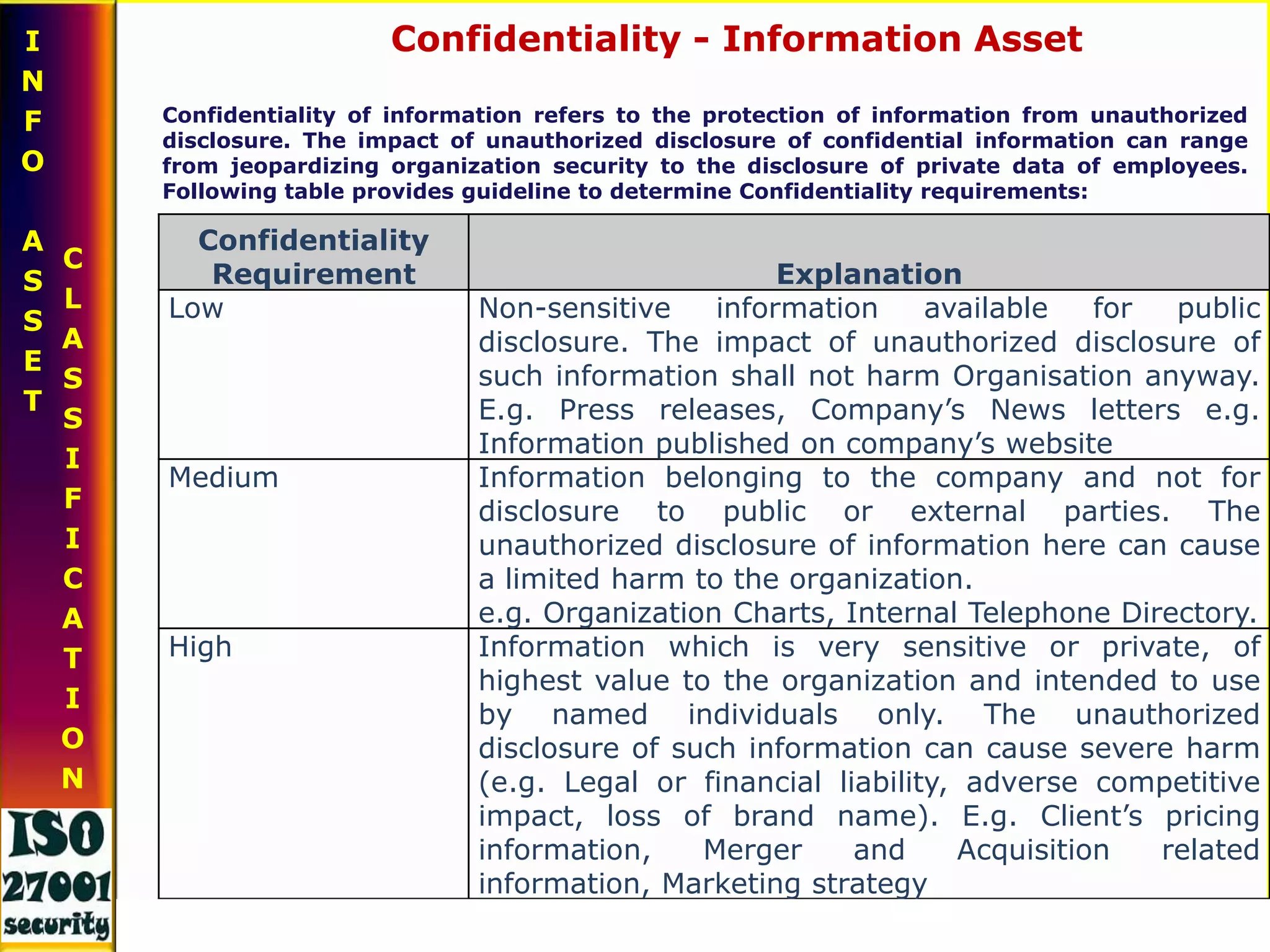
This document provides an overview of information security. It defines information and discusses its lifecycle and types. It then defines information security and its key components - people, processes, and technology. It discusses threats to information security and introduces ISO 27001, the international standard for information security management. The document outlines ISO 27001's history, features, PDCA process, domains, and some key control clauses around information security policy, organization of information security, asset management, and human resources security.