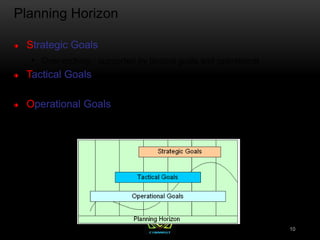
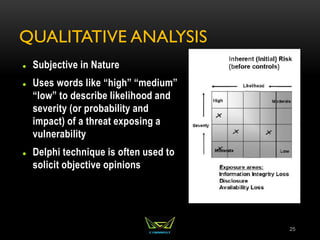
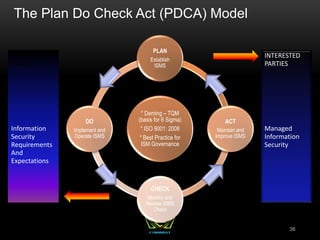
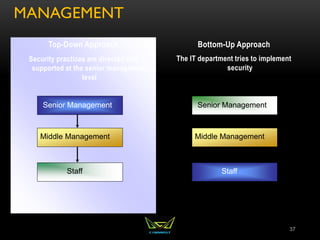
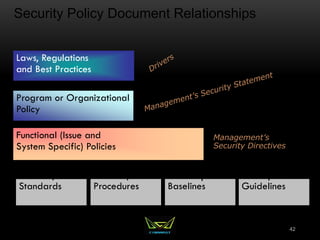
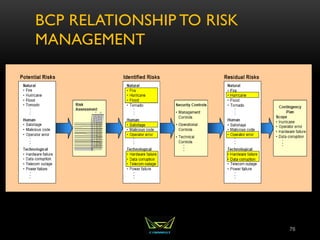
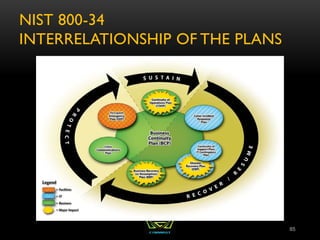
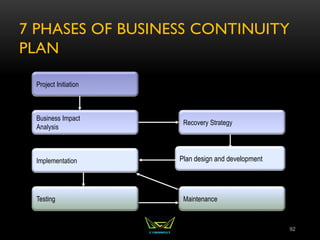
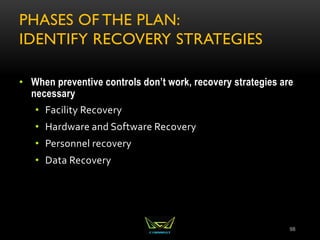
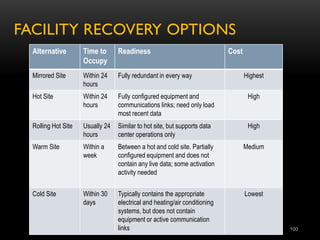
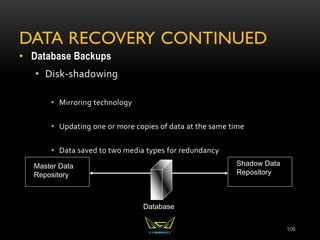
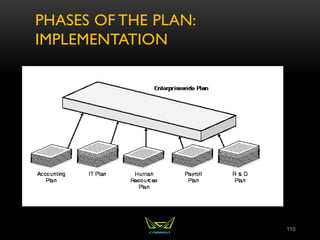
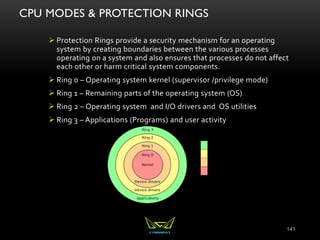
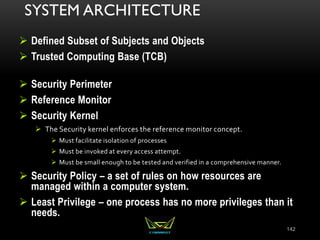
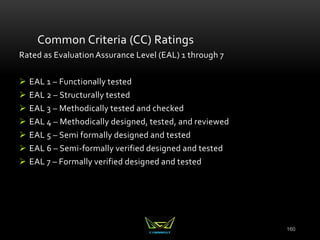
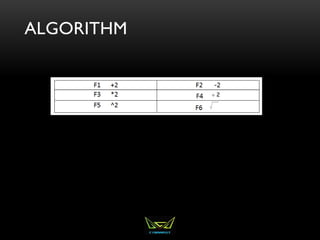
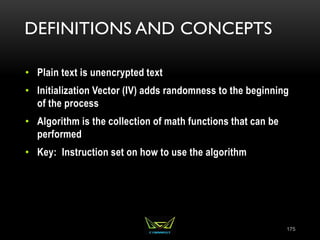
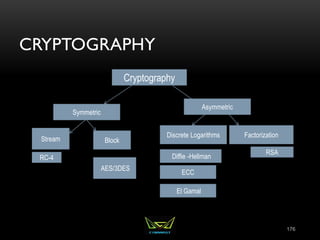
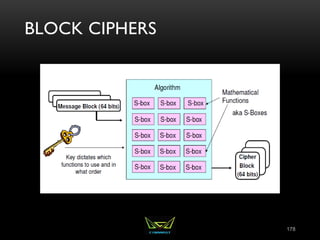
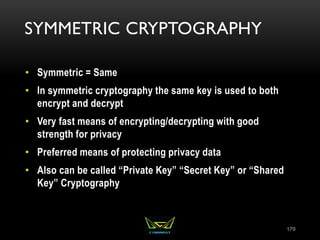
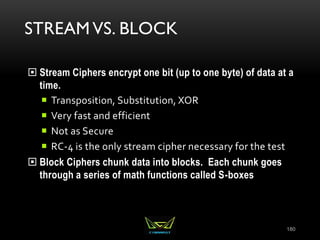
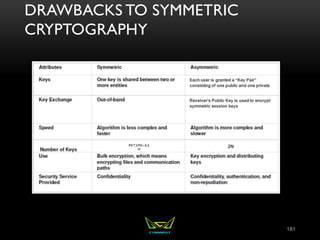
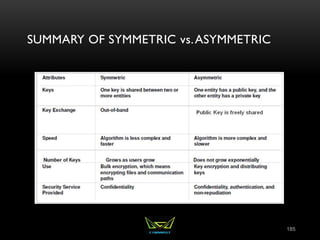
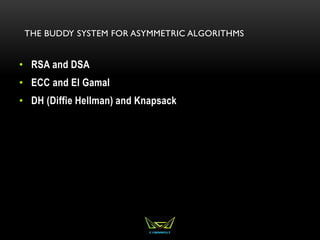
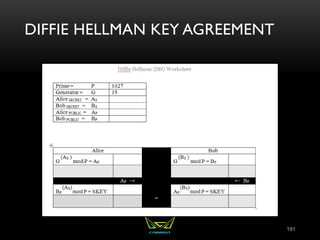
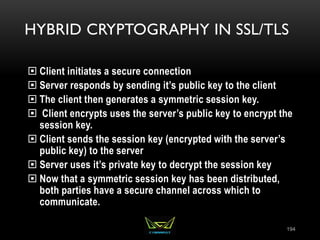
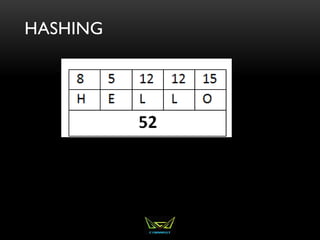
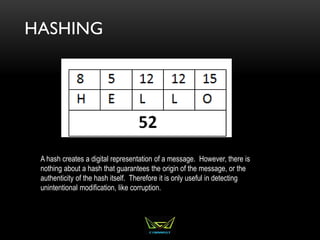
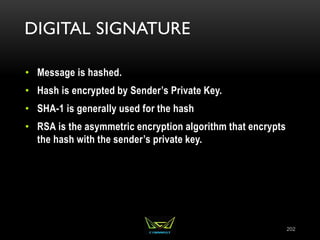
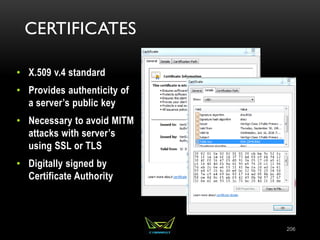
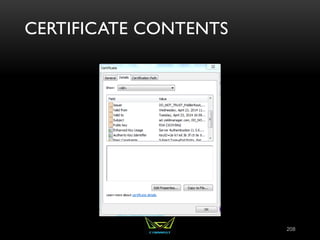
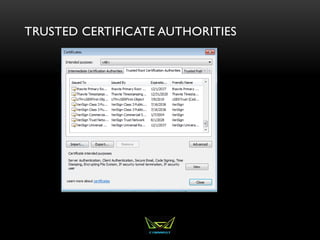
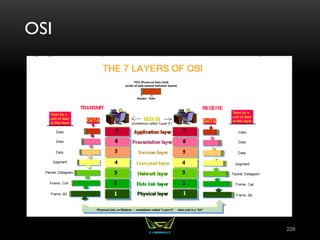
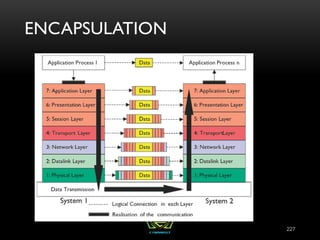
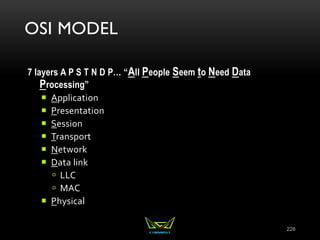
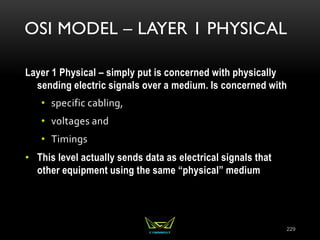
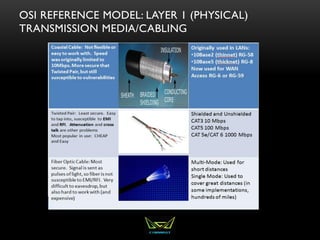
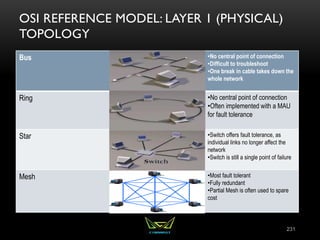
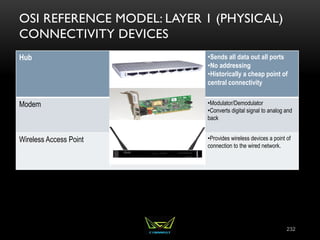
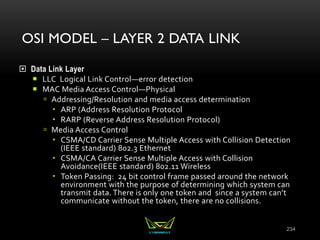
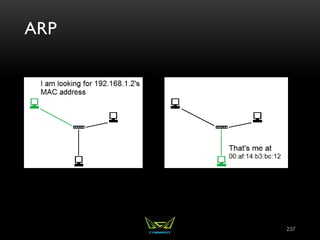
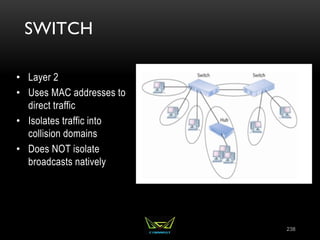
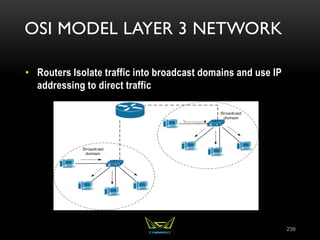
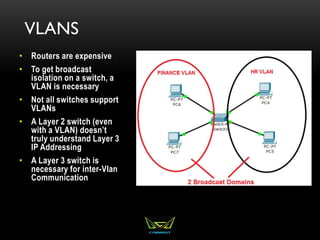
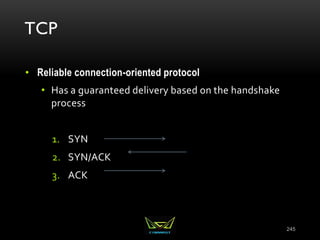
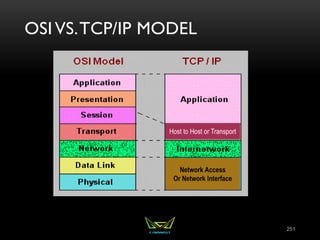
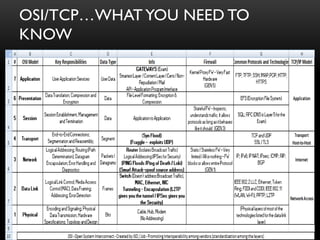
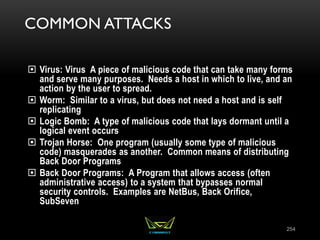
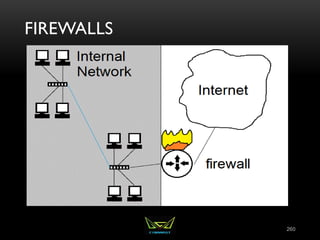
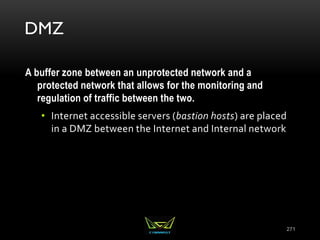
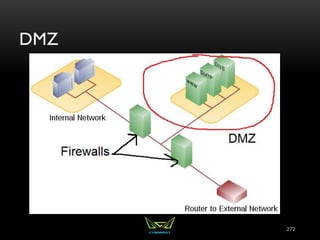
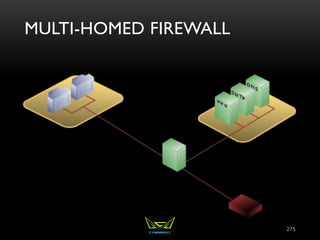
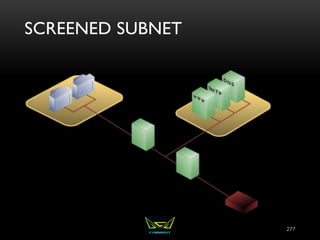
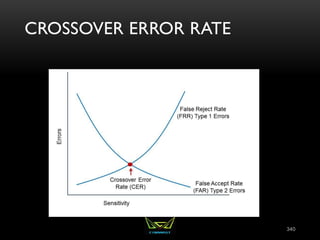
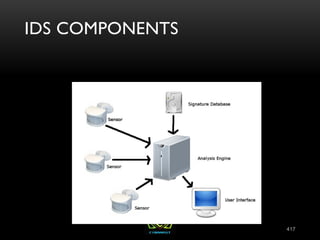
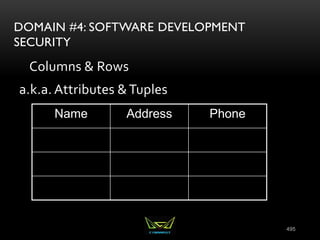
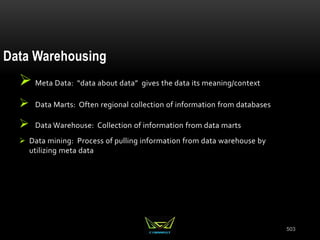
The document provides an overview of the CISSP certification course. It outlines the 8 domains that will be covered in the CISSP certification exam: Security and Risk Management, Asset Security, Security Engineering, Communications and Network Security, Identity and Access Management, Security Assessment and Testing, Security Operations, and Software Development Security. It also provides details about the exam such as the number of questions, time limit, and materials allowed.