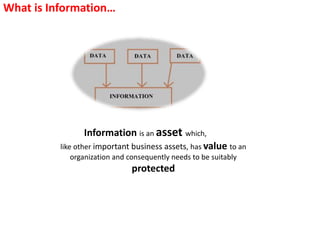
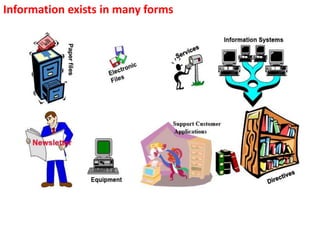
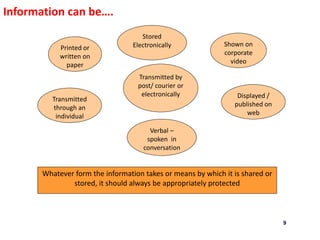
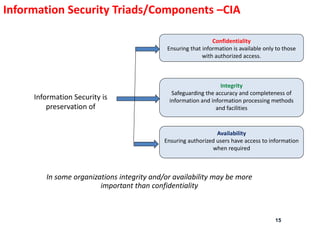
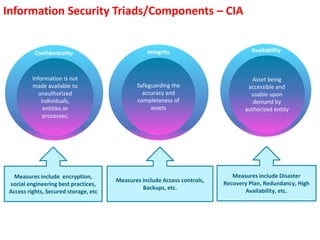
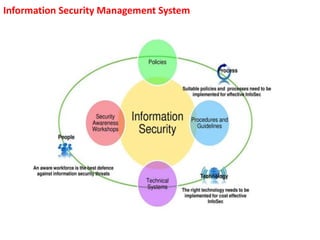
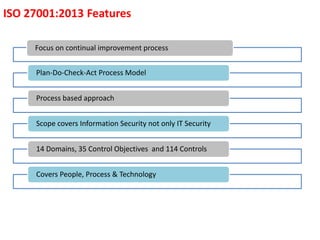
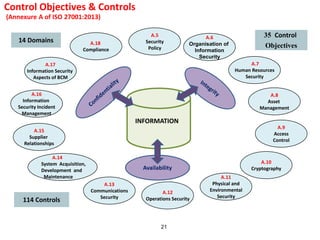
The document outlines the implementation of an Information Security Management System (ISMS) based on ISO 27001:2013, detailing risks associated with poor security practices and the necessity of protecting information assets. It includes real-world incidents of data breaches and fraud, emphasizing the importance of confidentiality, integrity, and availability in information security. The document also describes the framework, requirements, and risk management processes involved in establishing an effective ISMS to safeguard organizational assets.