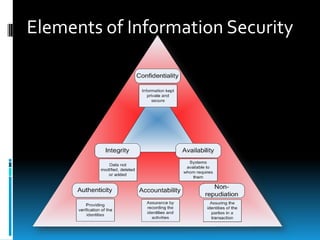
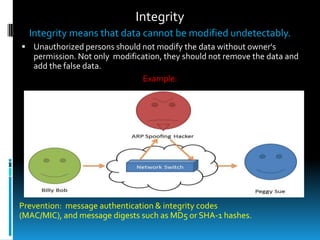
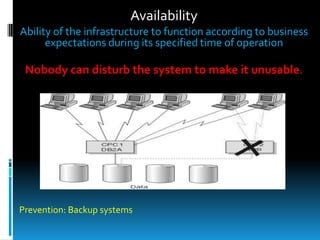
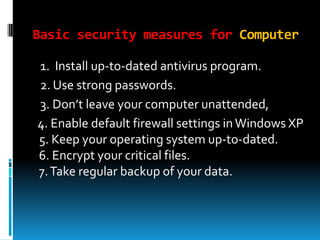
This document provides an introduction to information security. It defines information security as the protection of information and systems from unauthorized access, use, disclosure, disruption, modification, inspection, recording or destruction. The document outlines some key threats to information security like destruction, disclosure and modification of data. It also discusses the goals of information security - confidentiality, integrity, availability and authenticity - and common threats that relate to each goal. Additionally, the document covers security aspects like data security, computer security and network security and provides basic measures to enhance security in each area.