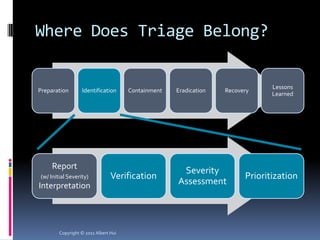
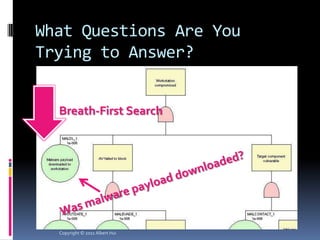
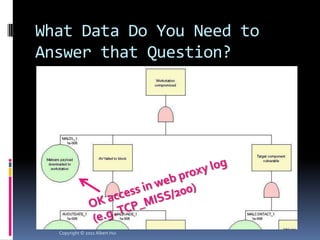
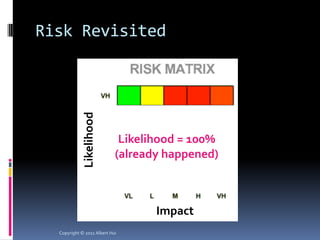
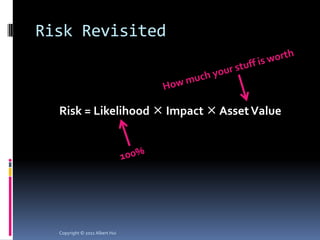
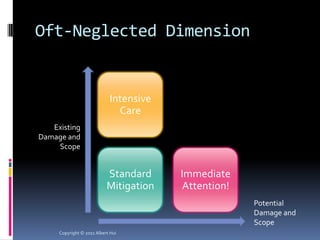
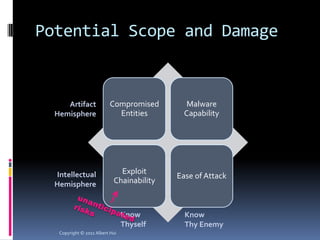
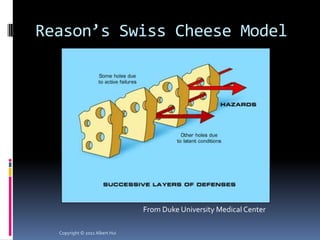
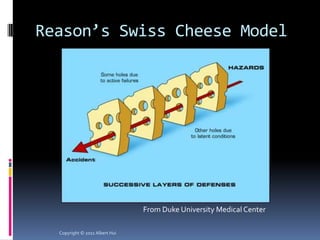
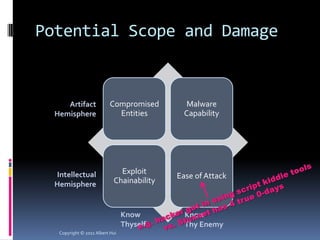
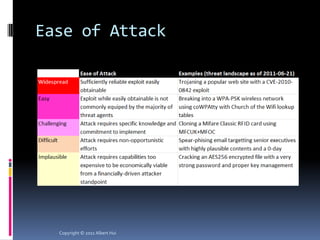
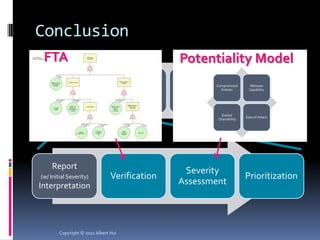
The document summarizes a presentation given by Albert Hui at the 5th Annual HTCIA Asia Pacific Conference on December 7th, 2011 in Hong Kong. The presentation discussed incident response triage, including the importance of triage in the incident response process. It covered how to systematically approach incident verification and assessing the severity and potential impact of incidents to prioritize response efforts. Key aspects of Hui's proposed severity assessment model included considering existing damage and scope, potential future damage and exploit chainability.