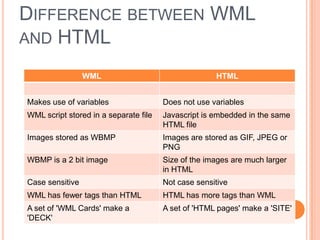
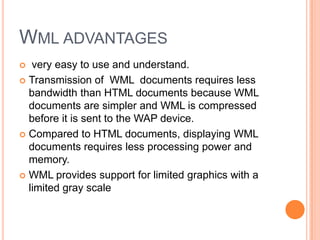
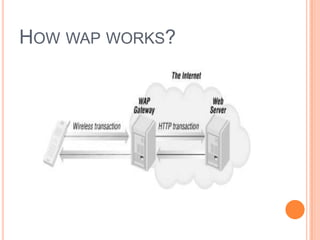
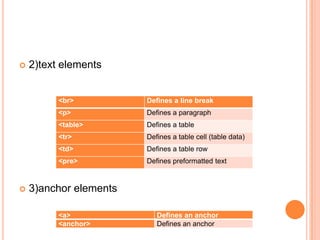
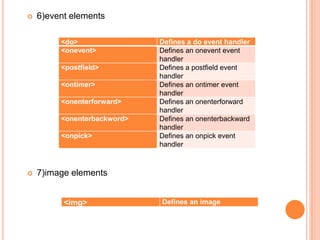
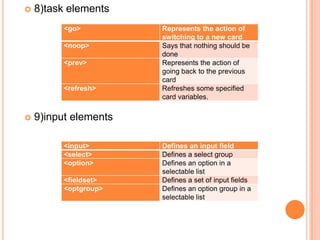
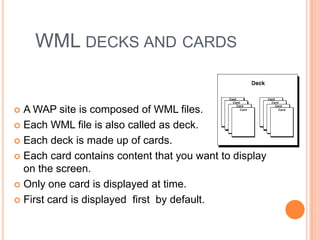
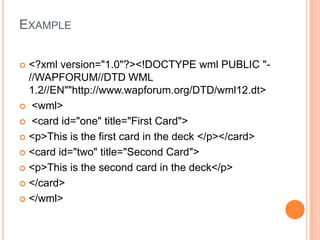
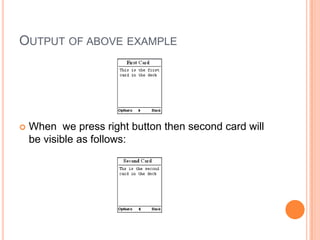
Wireless Markup Language (WML) is an XML-based language used to make content for mobile devices. It provides navigation, forms, text, images and hyperlinks similar to HTML but uses less bandwidth and processing power. A WML site consists of decks which contain cards that display content on the device screen one at a time. WML is simpler than HTML to optimize for limited mobile capabilities but has limitations in display variations across devices.