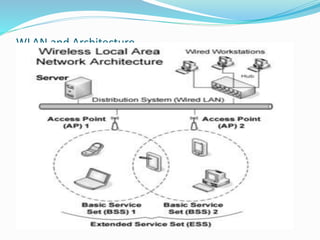
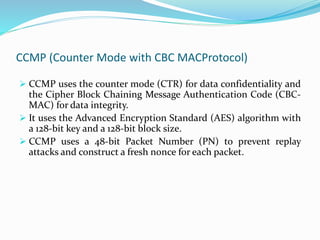
The document discusses wireless local area network (WLAN) security. It describes common WLAN security methods like service set identifiers (SSIDs), Wired Equivalent Privacy (WEP), and media access control (MAC) address authentication. It also discusses newer security protocols like Wi-Fi Protected Access (WPA) and WPA2 that improved upon WEP. WPA2 is the strongest and uses the Advanced Encryption Standard (AES) along with 802.1X authentication, the Counter Mode with CBC-MAC Protocol (CCMP), and the Temporal Key Integrity Protocol (TKIP). The document recommends using a combination of security technologies and performing a threat risk assessment to determine the optimal WLAN security solution.