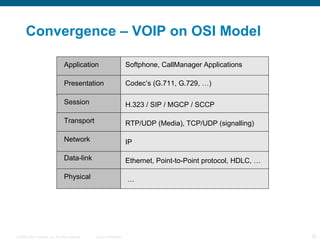
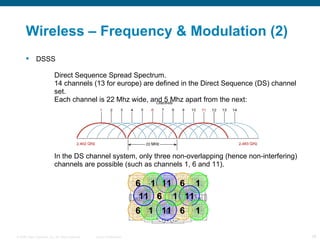
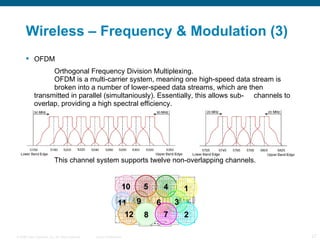
The document provides an overview of networking concepts including the OSI model, WAN technologies, convergence, wireless networking, and authentication methods. It describes the seven layers of the OSI model and technologies associated with each layer such as Ethernet and IP. It also discusses WAN options like leased lines, MPLS, and QoS mechanisms for prioritizing traffic. Wireless topics covered include frequencies, modulation, authentication, encryption, and next-generation centralized wireless network architectures.