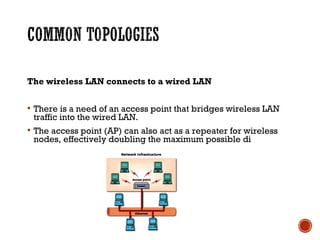
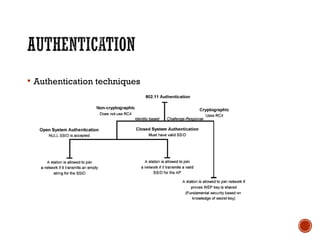
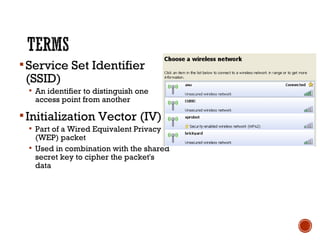
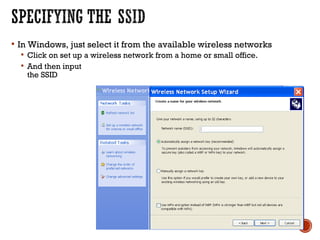
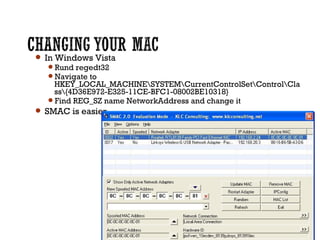
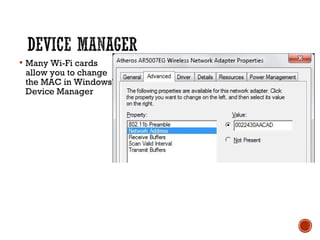
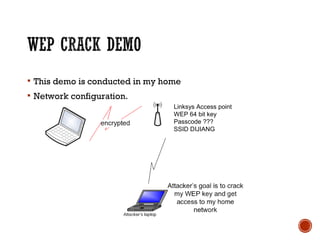
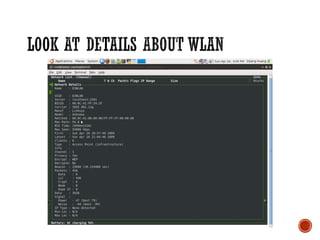
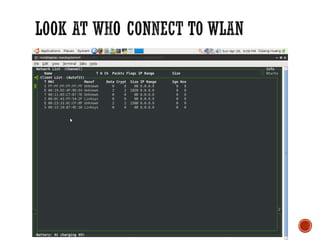
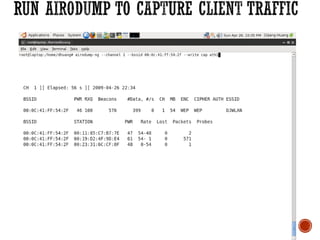
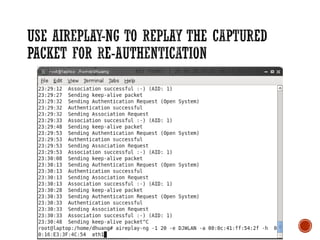
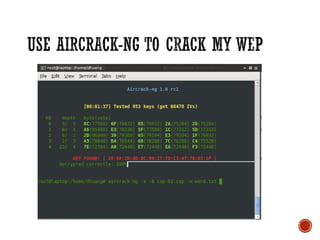
This document discusses wireless local area networks (WLANs) and wireless security. It covers WLAN basics and standards like 802.11a, 802.11b and 802.11g. It describes security protocols like Wired Equivalent Privacy (WEP) and vulnerabilities like weak encryption keys. The document discusses ways to crack WEP security and better security protocols like WPA/WPA2. It also provides instructions on how to scan and crack wireless networks using tools like Aircrack-ng on different operating systems.