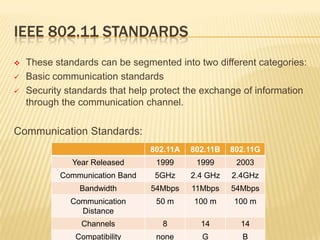
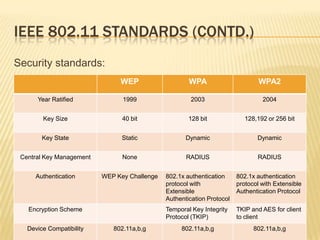
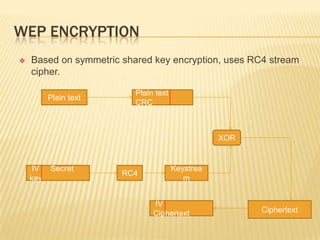
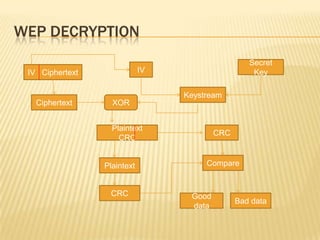
Wireless networks have become commonplace in homes and offices, enabling increased productivity and mobile connectivity. They function by connecting clients to a central access point or in an ad-hoc peer-to-peer mode. Early security standards like WEP had vulnerabilities due to short encryption keys and initialization vector reuse. WPA and its successor WPA2 were developed to address these issues through stronger encryption, authentication, and dynamic key generation. However, wireless networks remain vulnerable to insertion attacks by unauthorized clients or rogue access points, as well as traffic interception if encryption is not used.