Embed presentation
Downloaded 115 times


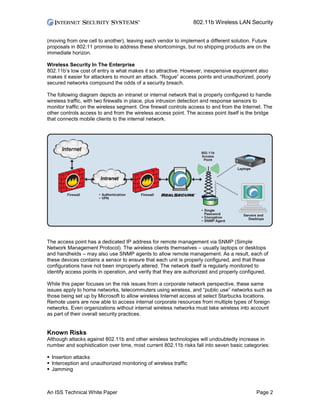




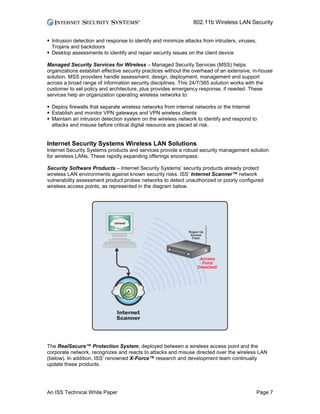

The document discusses security issues with 802.11b wireless LANs. It identifies 7 categories of risks: insertion attacks, interception of traffic, jamming, client-to-client attacks, brute force password attacks, encryption attacks, and misconfigurations. Default access point settings like SSIDs and passwords leave them vulnerable if not changed. Proper configuration of wireless access points, firewalls, intrusion detection, and encryption are recommended to secure a wireless network.









