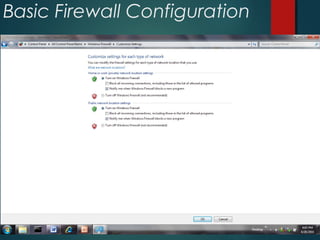
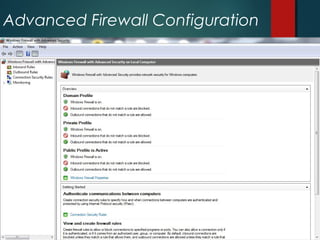
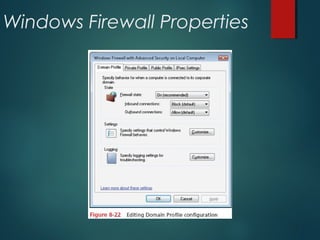
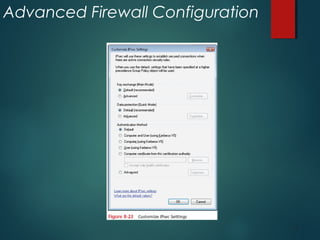
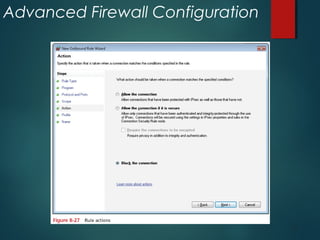
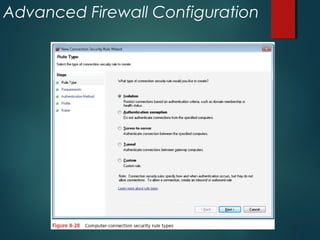
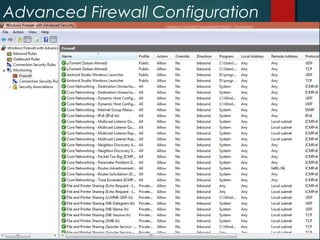
The document discusses Windows Firewall, explaining its purpose, types, and functionalities, emphasizing its role in preventing unauthorized access to computers through networks. It details the features of Windows 7 Firewall, including different profiles for various network locations (public, private, and domain) and the configuration options available for managing firewall rules and connections. Additionally, it covers the technical workings of the firewall, such as how it filters traffic and logs entries based on defined rules.