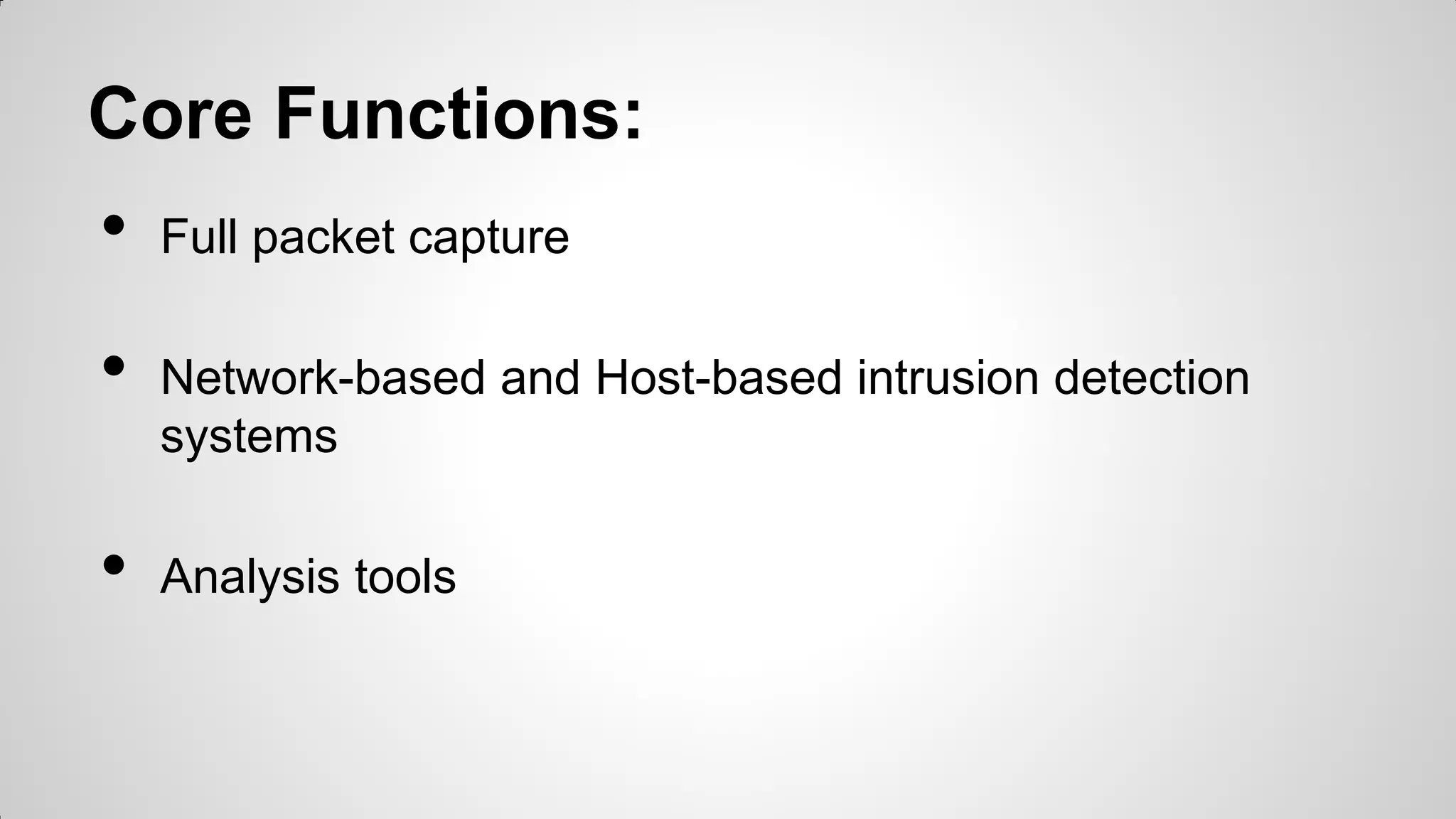
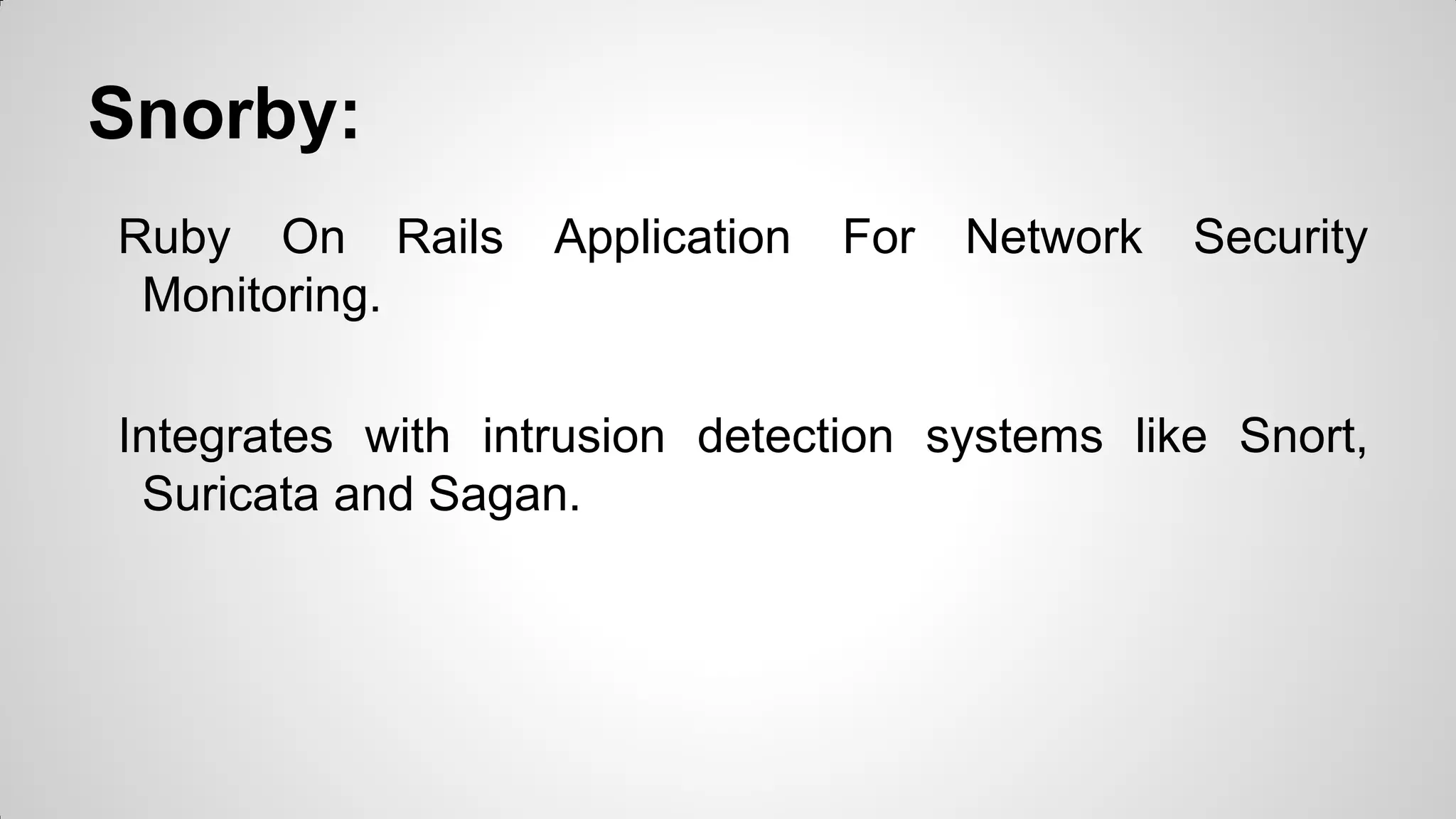
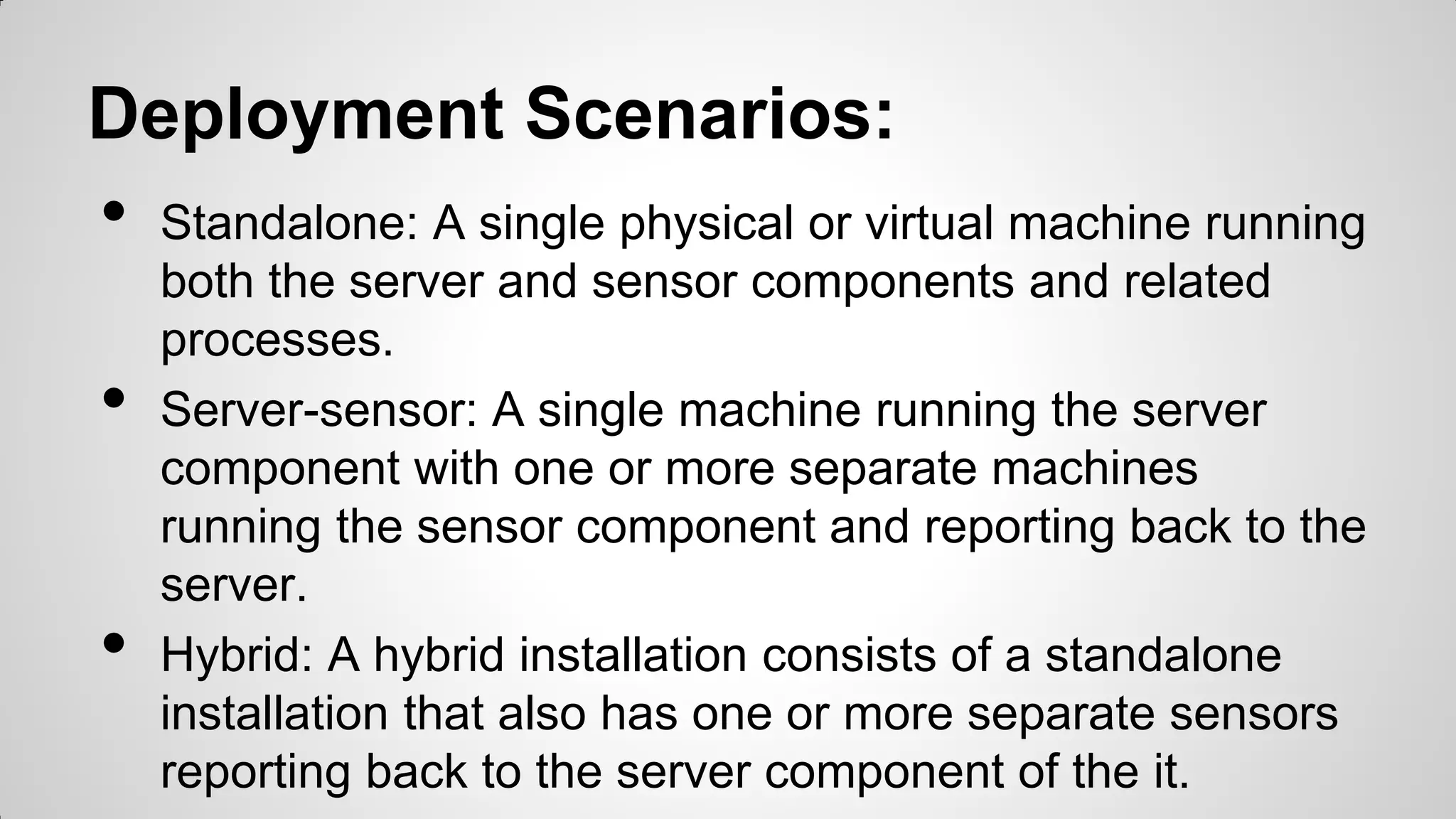
Security Onion is a Linux distribution for intrusion detection, network security monitoring, and log management. It contains tools like Snort, Suricata, Bro, OSSEC, Sguil, Squert, Snorby, ELSA, and NetworkMiner. It allows full packet capture, network and host intrusion detection, and log collection and management. Security Onion can be deployed in standalone, server-sensor, or hybrid configurations.