This document discusses file sharing and secondary storage management in operating systems. It covers several topics:
File sharing allows multiple users to access files, but access rights and simultaneous access must be managed. Access rights include permissions levels from none to deletion. Simultaneous access requires enforcing mutual exclusion to prevent conflicts.
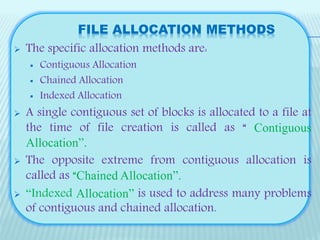
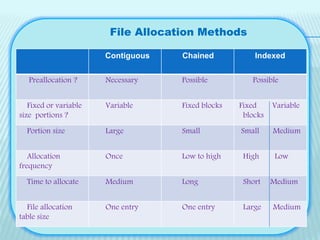
Secondary storage management involves allocating blocks to files from available disk space. File allocation methods include contiguous, chained, and indexed allocation. Contiguous allocates all blocks at once while chained uses pointers between non-contiguous blocks. Indexed addresses problems with the other methods.
Free space is managed using techniques like bit tables to track used/free blocks, chained free portions, or a free block list maintained on disk