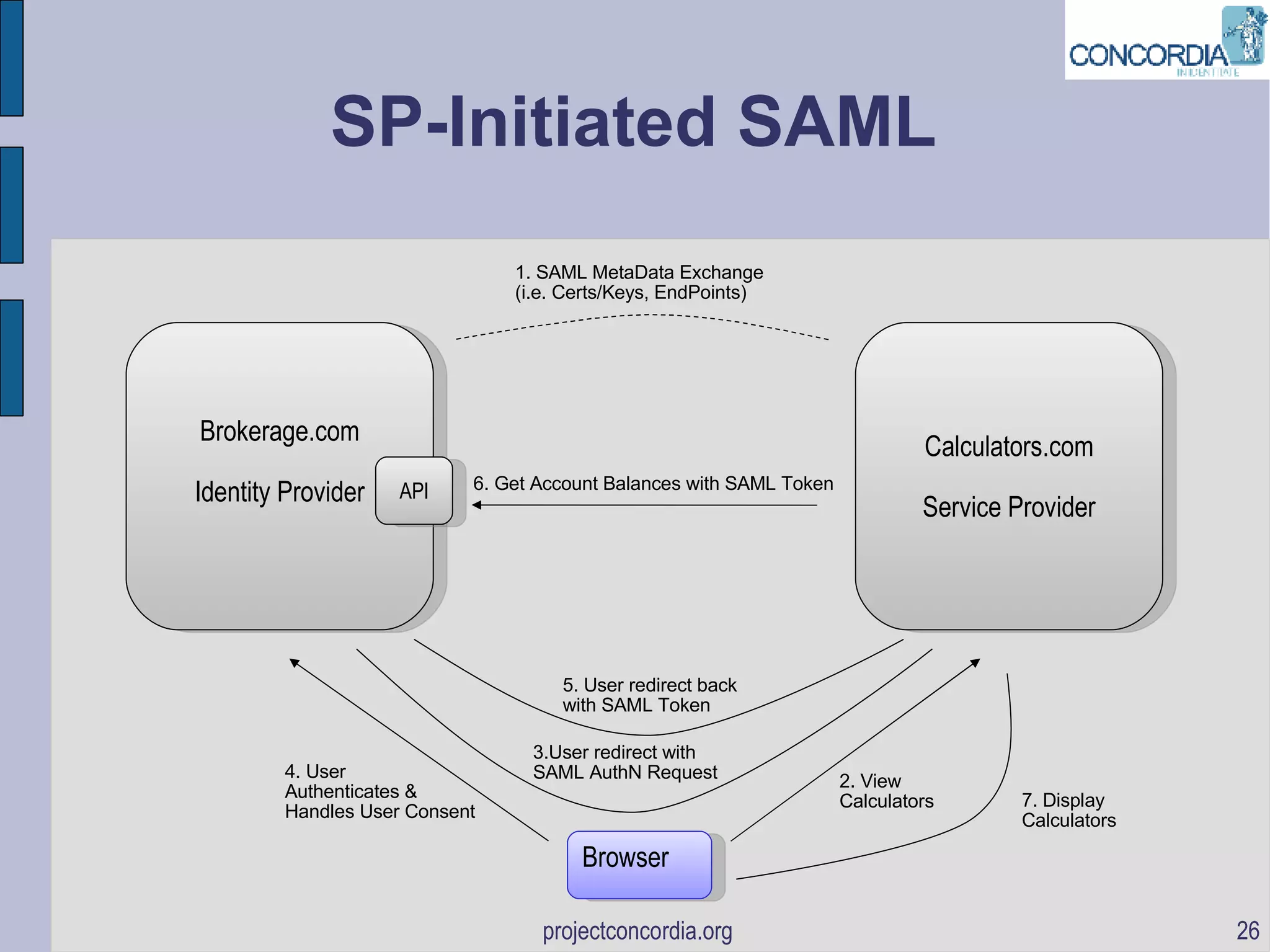
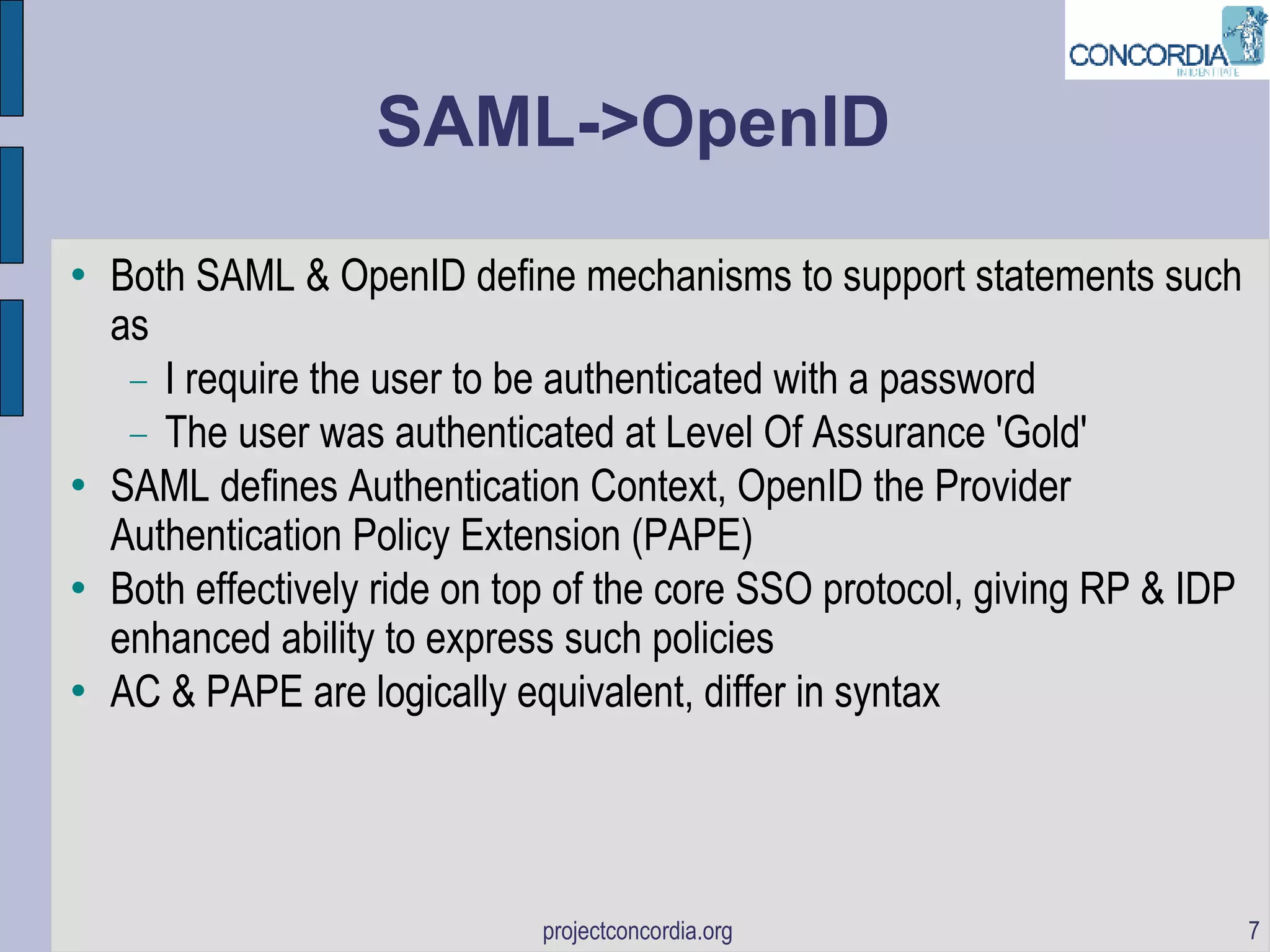
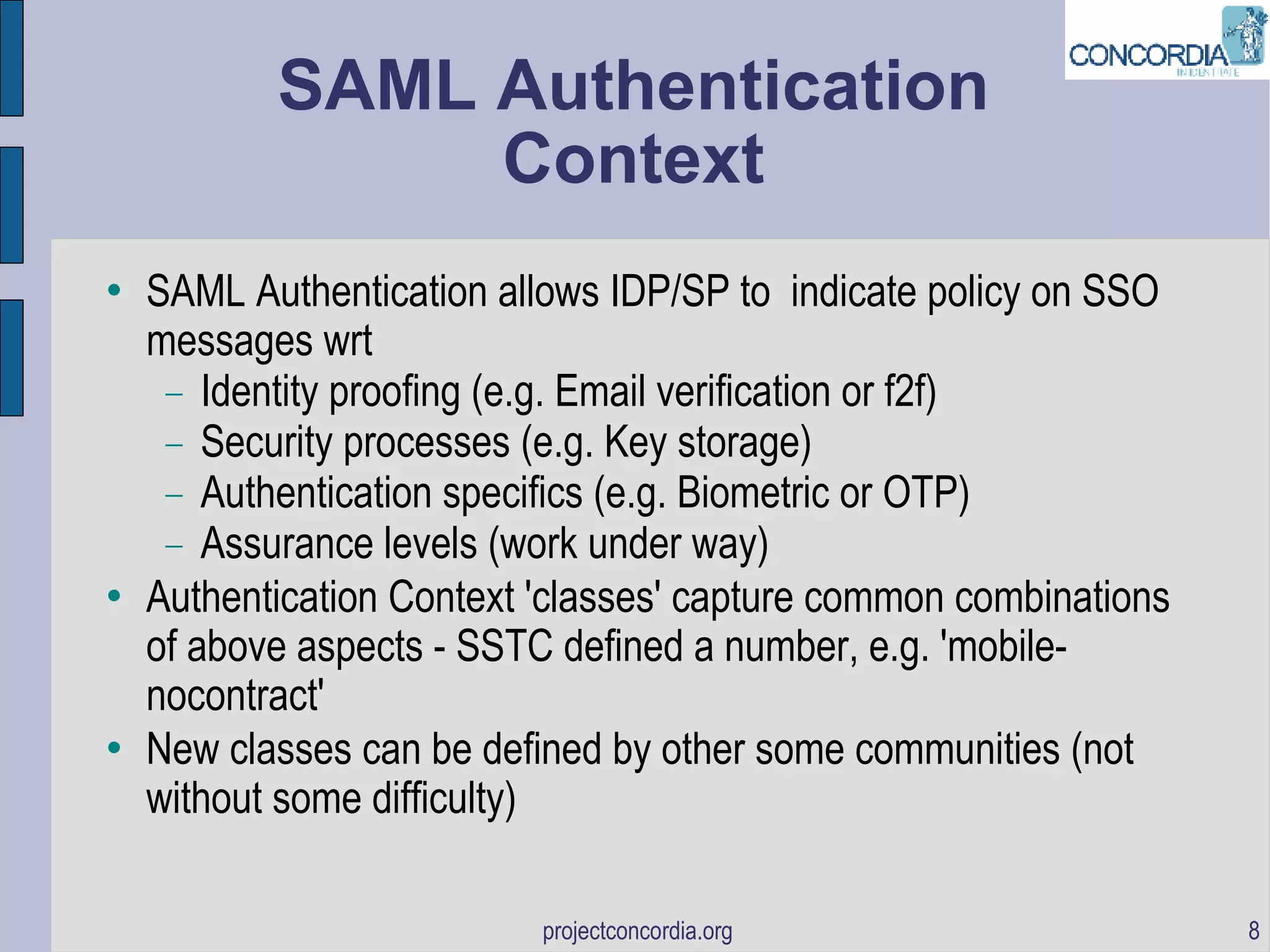
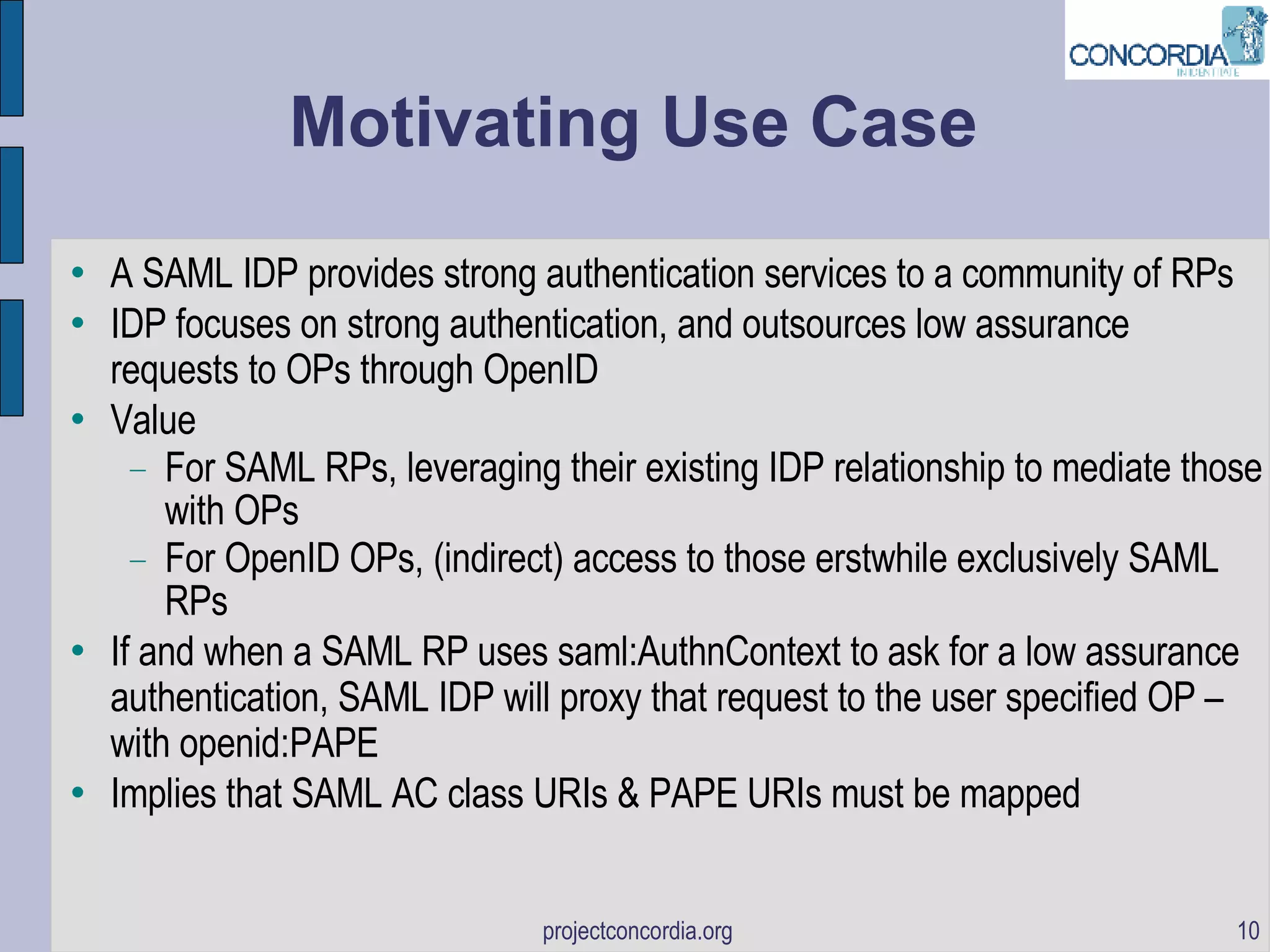
The document discusses bootstrapping identity protocols to work together, including SAML to OpenID, Infocards to ID-WSF, and SAML to OAuth. It provides examples of how these protocols can be chained together to enable single sign-on and API access across different systems.













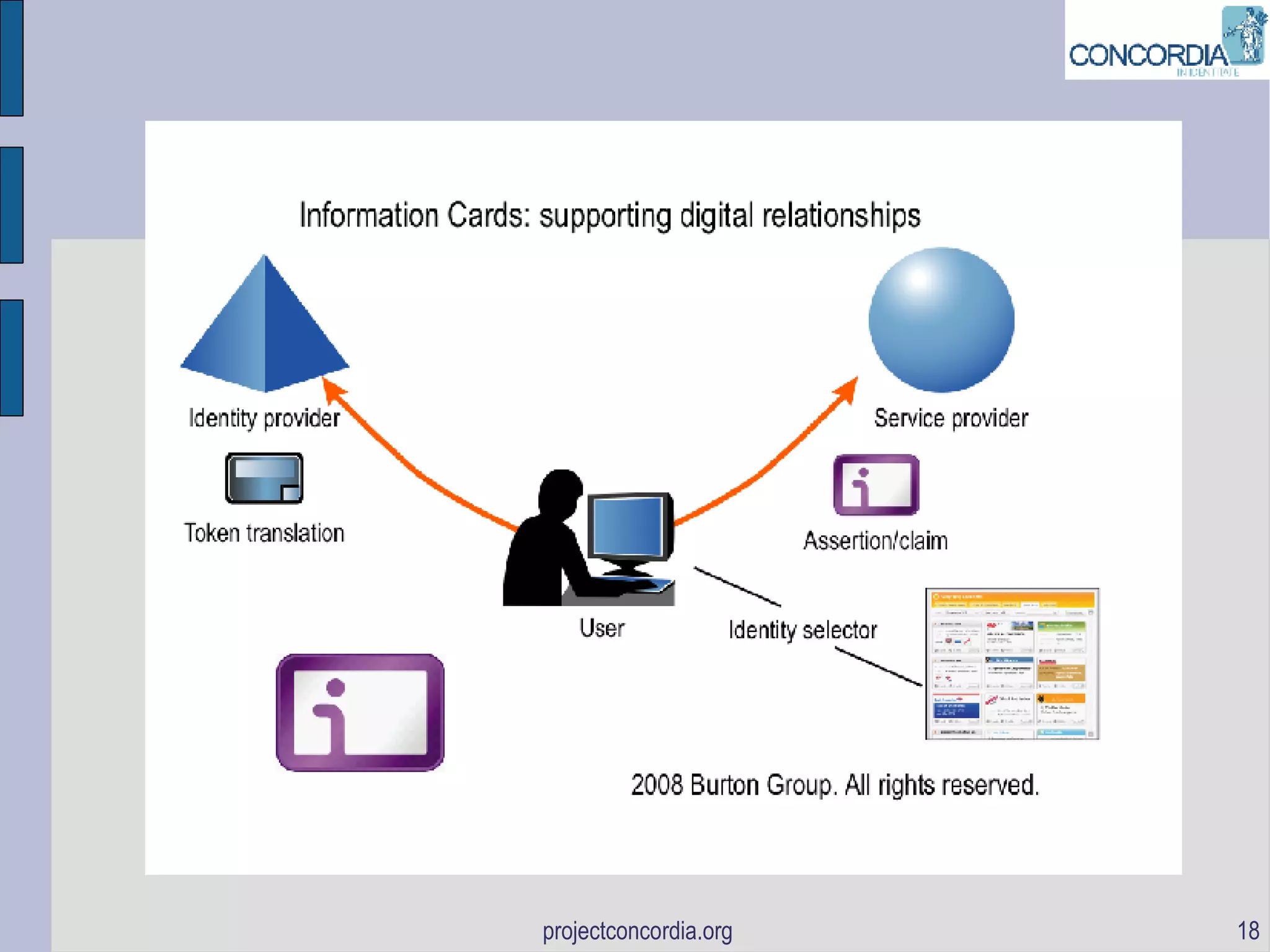

![The information card ID-WSF bootstrap The opportunity: Information Cards can be handy human consumable ID-WSF Containers (representing Discovery Service Endpoint References [DS-EPRs] EPRs and relationships such as subscriptions) Or from the other perspective, the DS provides a web services interface to the information card service](https://image.slidesharecdn.com/didwconcordiahrmfinal-1221479866803175-9/75/DIWD-Concordia-20-2048.jpg)