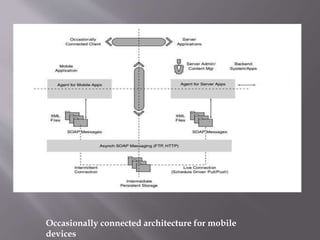
This document discusses metadata, security, transactions, and reliable messaging specifications for web services. It provides an overview of key specifications such as WSDL, WS-Security, WS-Transactions, and WS-Reliable Messaging that define standards for describing, securing, and coordinating web services and messages. The document also covers standards for integrating mobile devices into a service-oriented architecture.