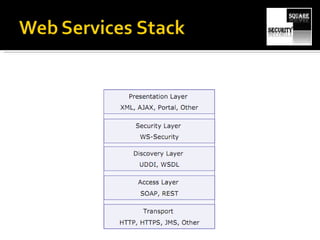
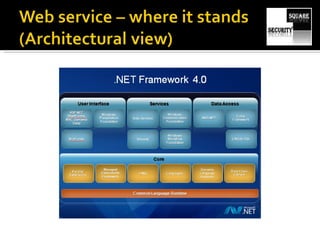
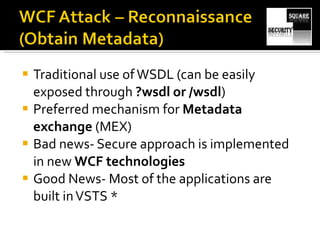
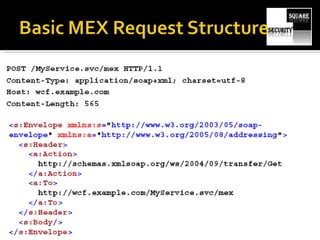
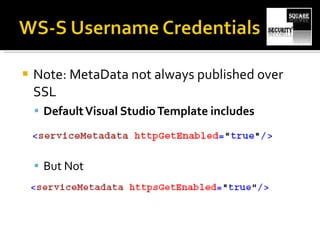
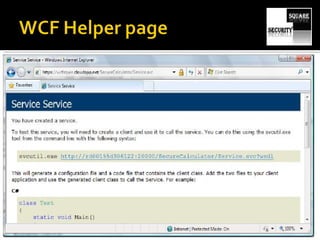
The document discusses testing the security of web services. It provides an overview of Windows Communication Foundation (WCF), explaining that it is Microsoft's framework for building networked applications and supports different protocols. It also discusses important concepts for WCF like addresses, bindings and contracts. The document then provides recommendations for tools to test WCF services, including WcfTestClient, WCF Storm and WSFuzzer, and discusses techniques like leveraging metadata and secure bindings.








![Every WCF Service has a Unique Address Transport Protocol Location Often use .svc file extension when hosted in IIS [transport]://[machine or domain][:optional port]/[optional uri]](https://image.slidesharecdn.com/wcfsecurity-110315064619-phpapp02/85/Web-Service-Security-11-320.jpg)








![Nabarun Sengupta Senior Test Engineer, Mindtree Limited Email Id: [email_address] Mobile: 9689881811](https://image.slidesharecdn.com/wcfsecurity-110315064619-phpapp02/85/Web-Service-Security-24-320.jpg)