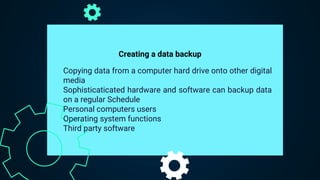
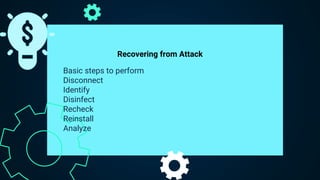
The document discusses desktop security, focusing on types of software and hardware attacks, including malware and physical theft. It outlines defenses such as antivirus software, data backups, and strategies for recovering from attacks. The importance of regularly updating security measures and protecting devices is emphasized.