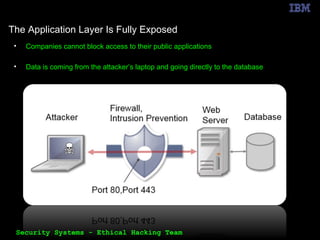
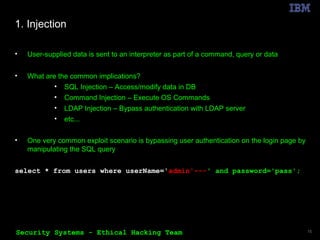
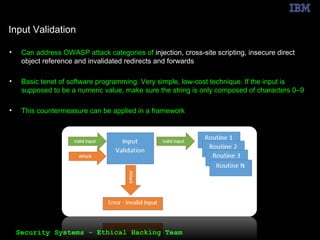
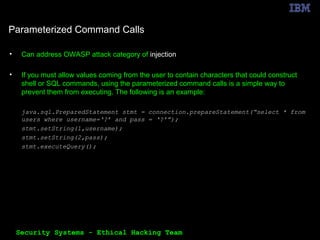
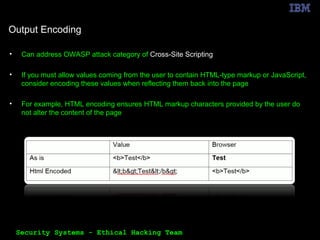
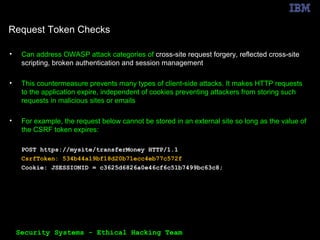
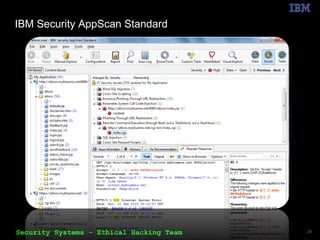
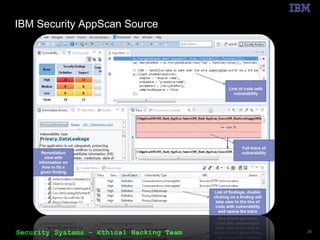
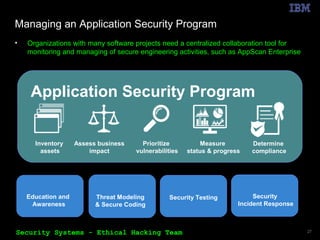
The document outlines the OWASP Top 10 web application vulnerabilities and their implications, including threats like SQL injection and cross-site scripting. It emphasizes the importance of implementing secure coding practices and threat modeling to prevent application attacks. Additionally, it suggests using automated tools for vulnerability scanning and emphasizes the cost-effectiveness of integrating security in the software development lifecycle.