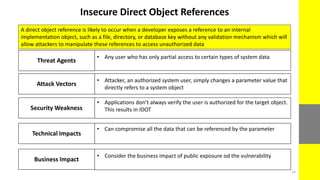
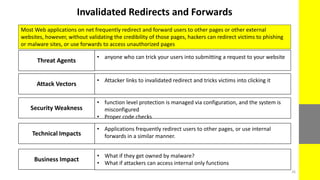
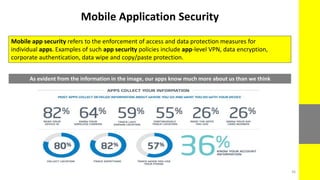
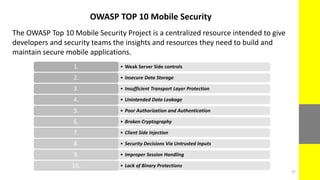
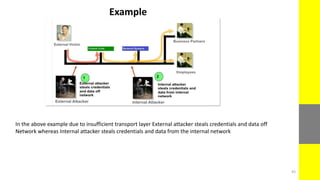
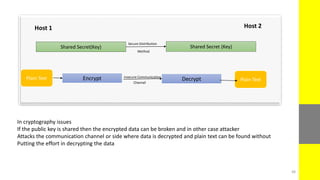
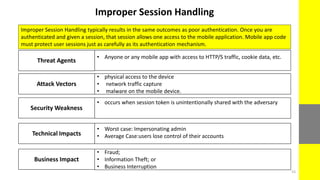
The report discusses the evolving nature of web and mobile application security, highlighting various vulnerabilities such as SQL injection, broken authentication, and cross-site scripting (XSS). It emphasizes the importance of security measures due to the high percentage of web applications with critical flaws and the potential financial damages from cybercrime. The document also outlines preventative strategies for these vulnerabilities, focusing on proper data validation and secure configuration practices.