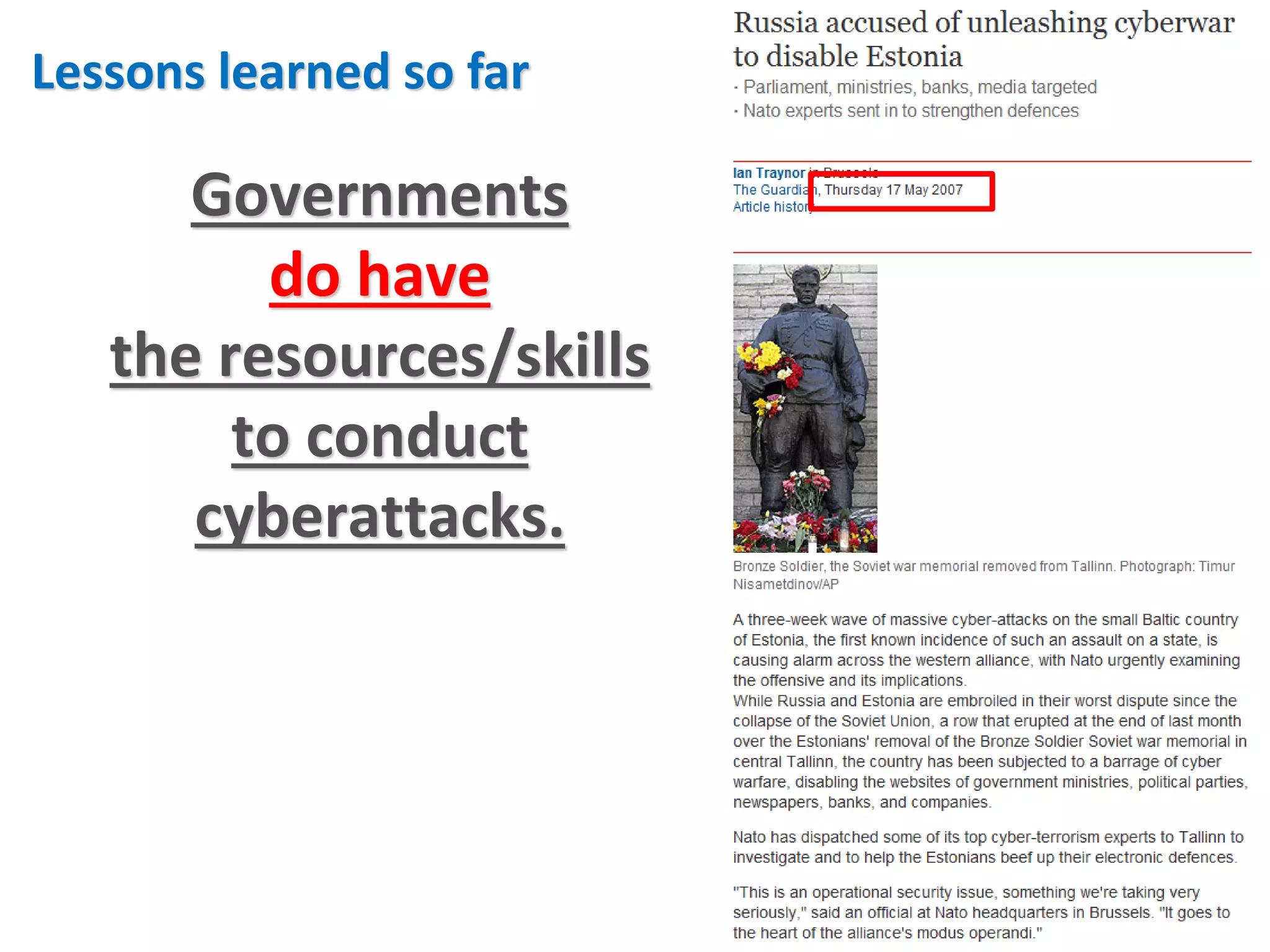
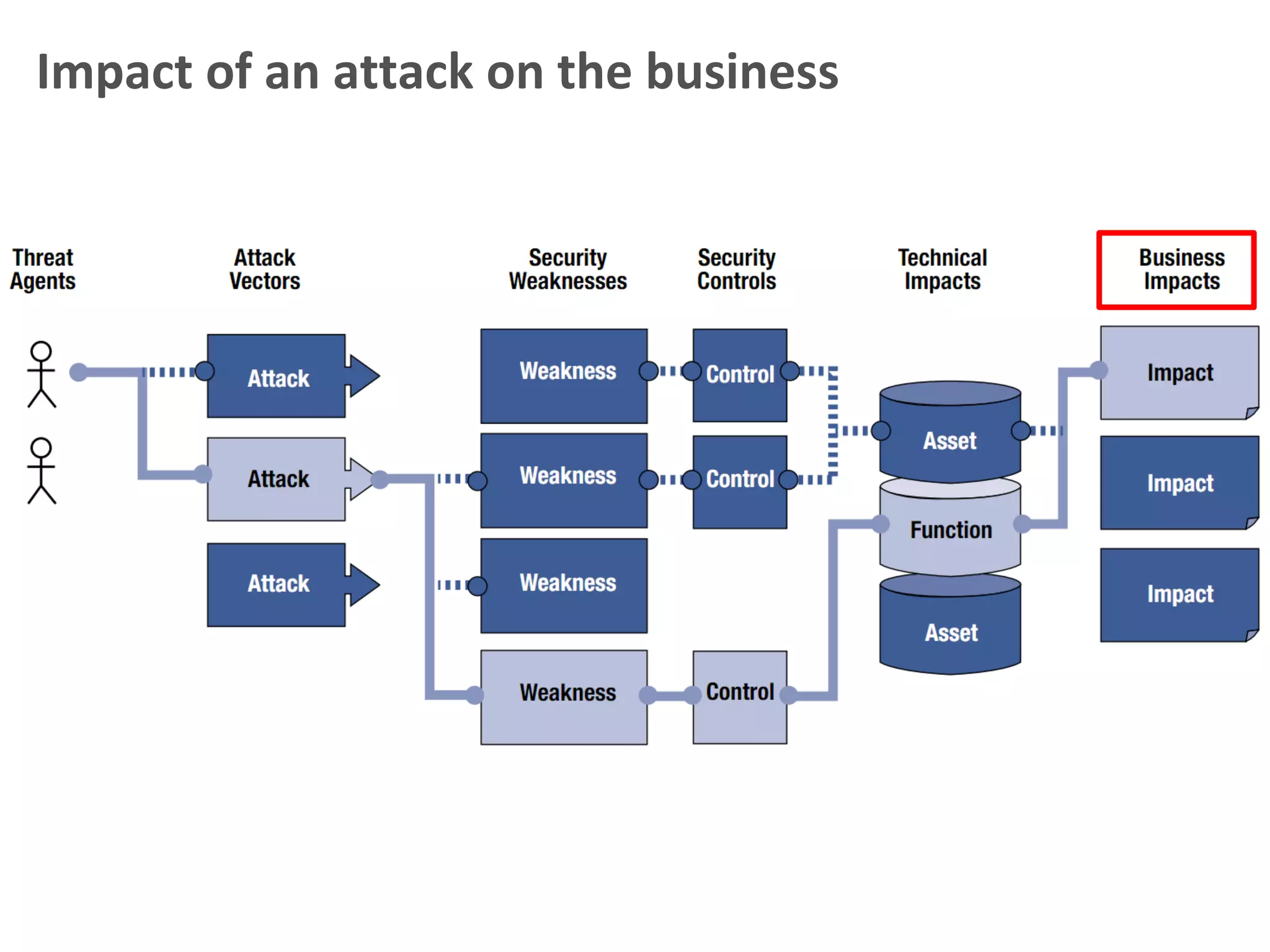
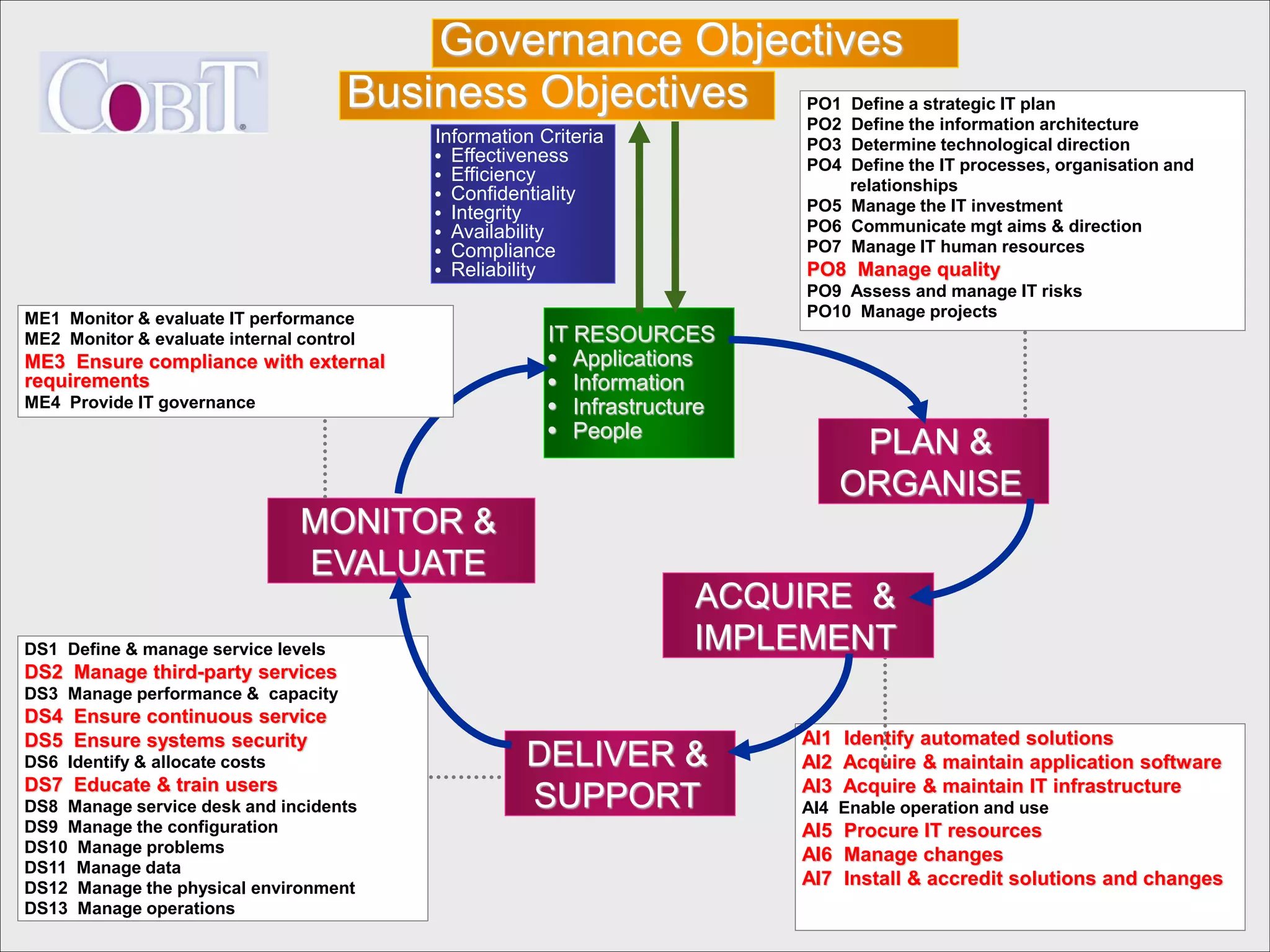
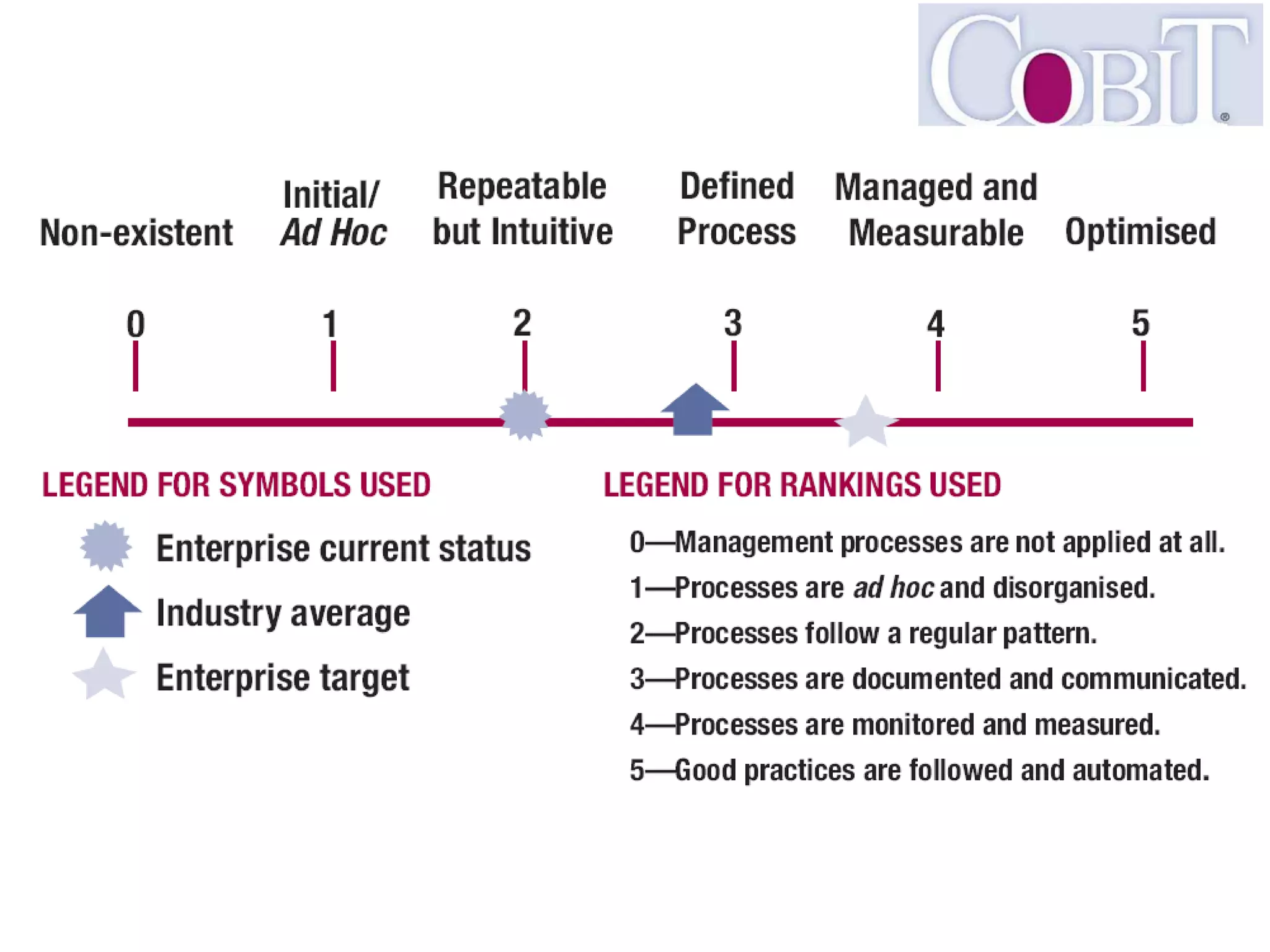
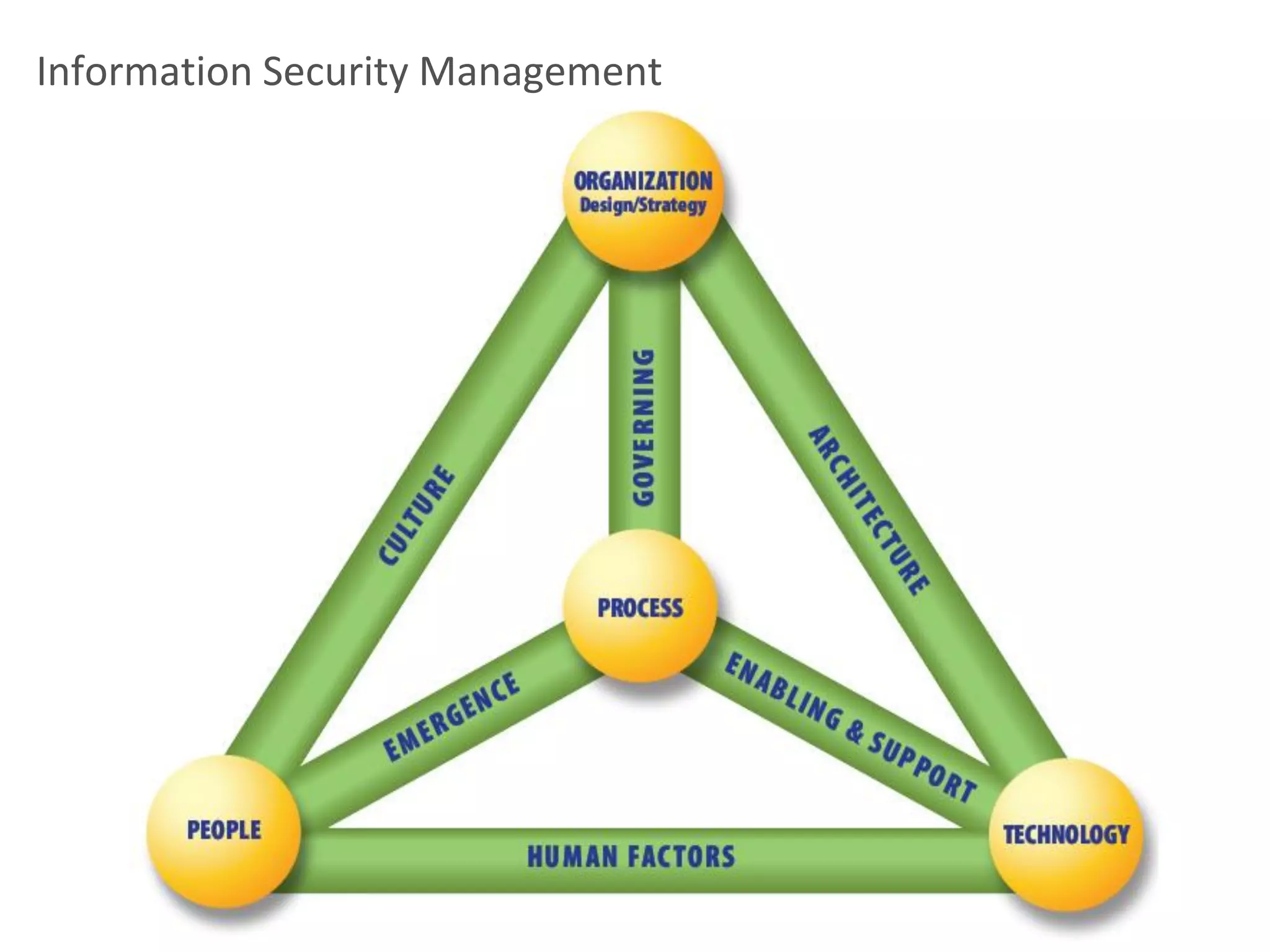
This document discusses cybersecurity threats and lessons learned regarding cyber attacks. It outlines various types of cyber threats including criminals, malware, and state-sponsored attacks. It notes that cyber attacks are difficult to execute but governments have the resources to conduct attacks. The document emphasizes that cyber attacks are a real danger and targets are often unprepared. It provides strategies for mitigating cyber attacks, including governance, policies, education, resources, and incident management. Overall, the document stresses that while technology is important, training people is also critical for cybersecurity.