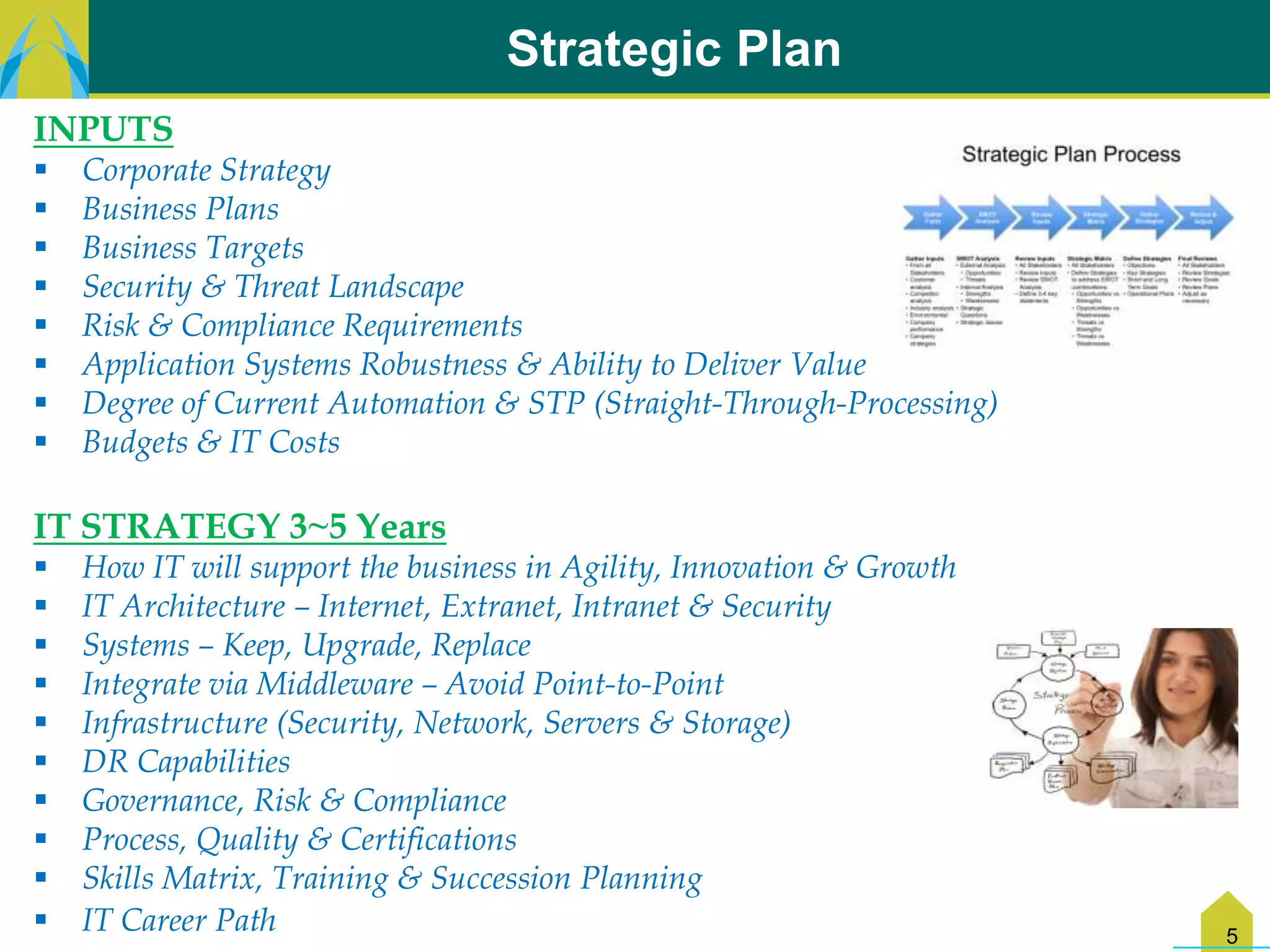
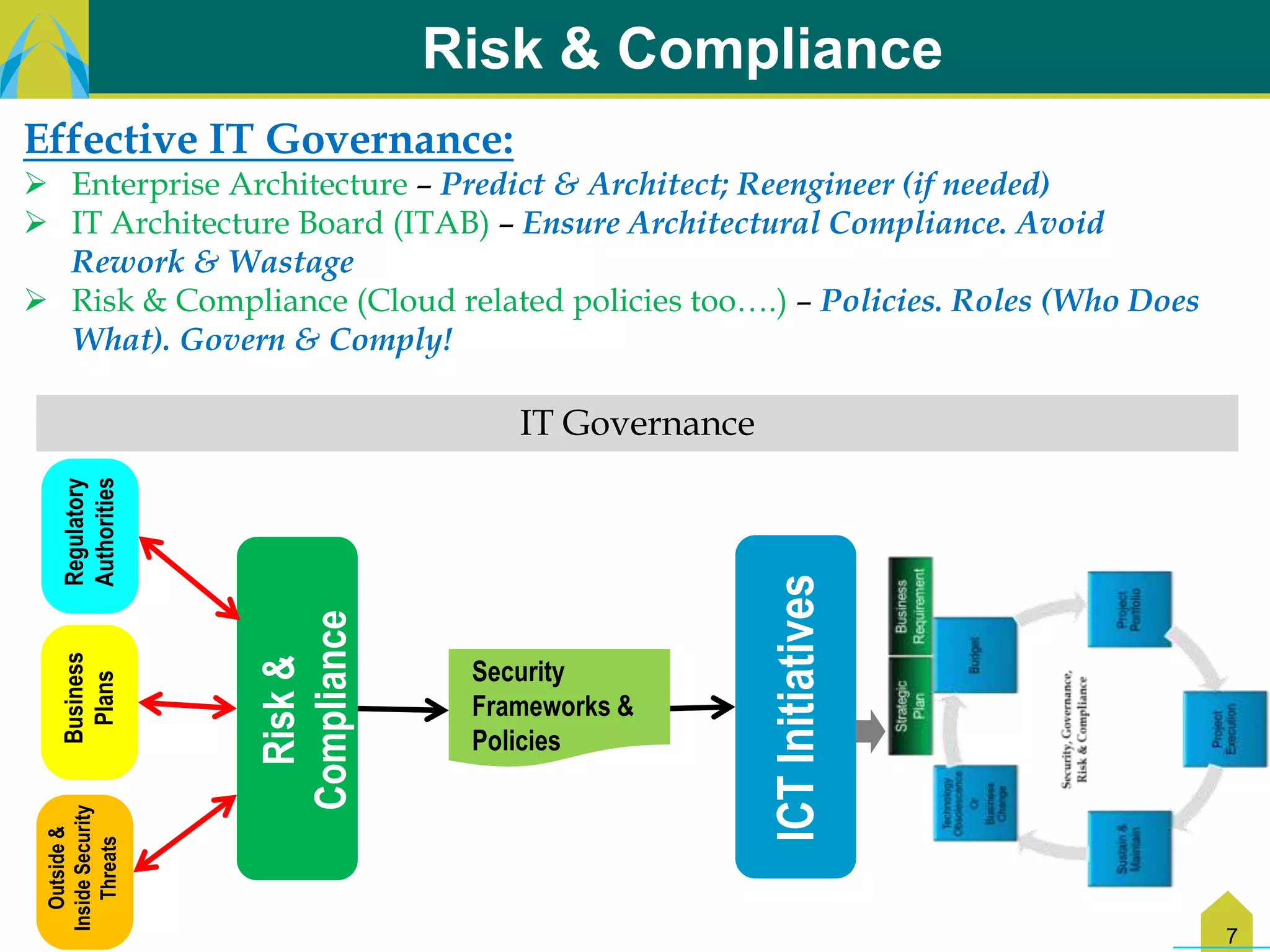
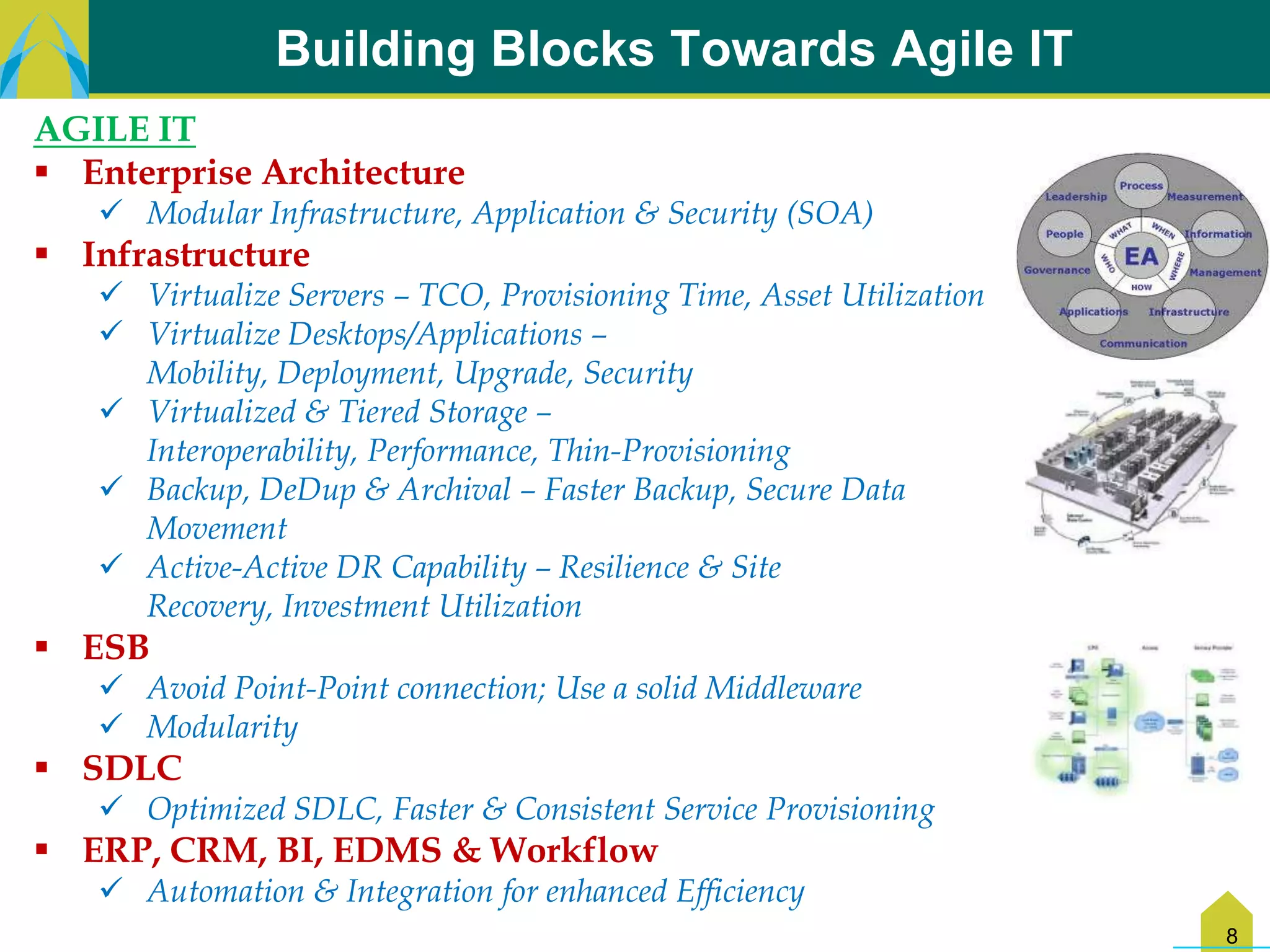
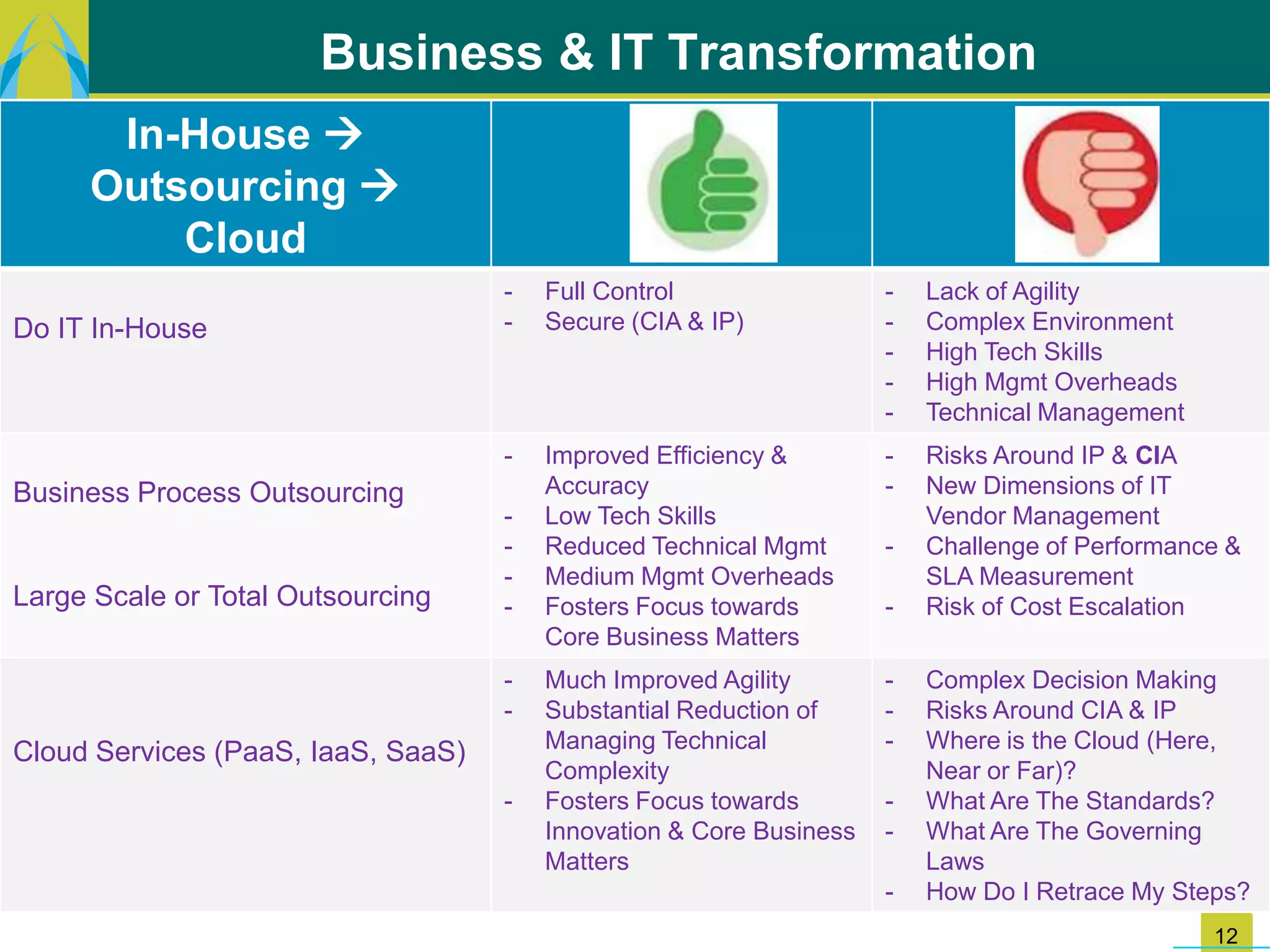
The document discusses key challenges in IT transformation including financial constraints, legacy infrastructure issues, lack of processes, and need for technical skills updates. It identifies quick wins like implementing change control and architectural blueprints. New opportunities include business-IT collaboration and proliferation of technologies. The way forward involves reducing distractions, implementing quick wins, and developing strategic and tactical plans covering people, processes, and technology. This would help build an agile IT environment leveraging approaches like cloud, outsourcing, and maturity models.