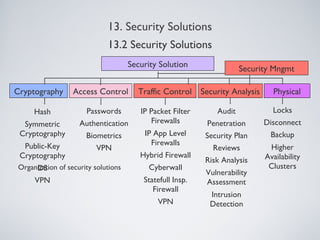
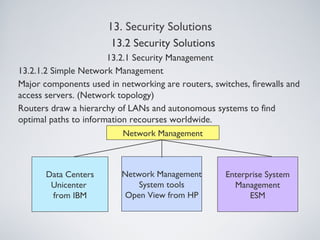
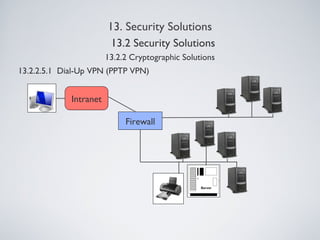
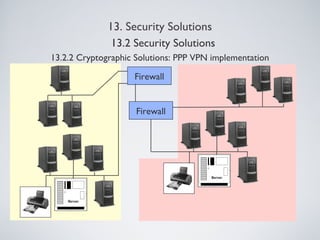
The document outlines various information security management solutions, emphasizing the importance of reducing harm from security breaches and the significant financial losses businesses incur due to attacks. It discusses key components of security management, including cryptographic solutions, access control systems, data traffic control, and security analysis processes. Additionally, it introduces frameworks like ISO and NIST that guide organizational security practices.