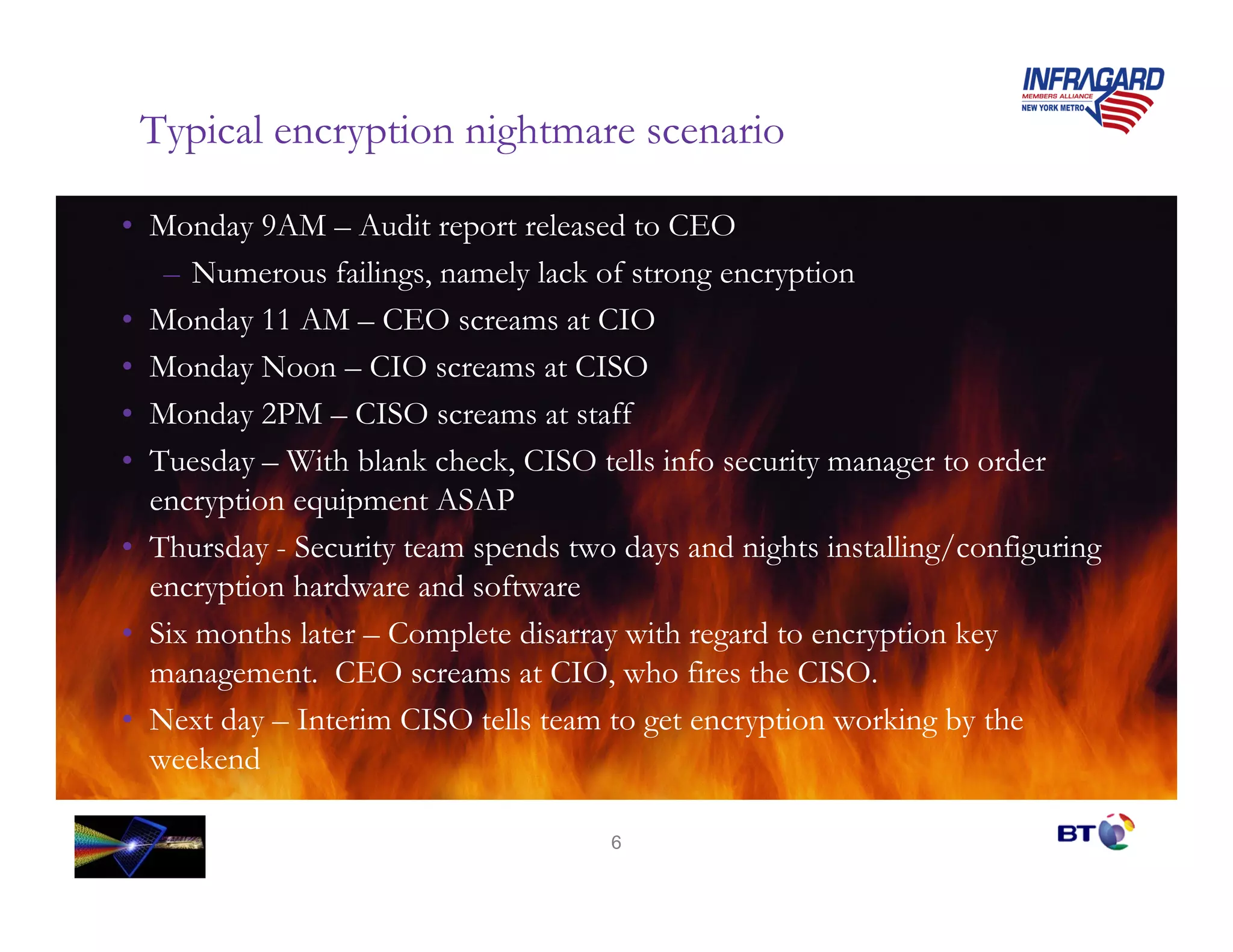
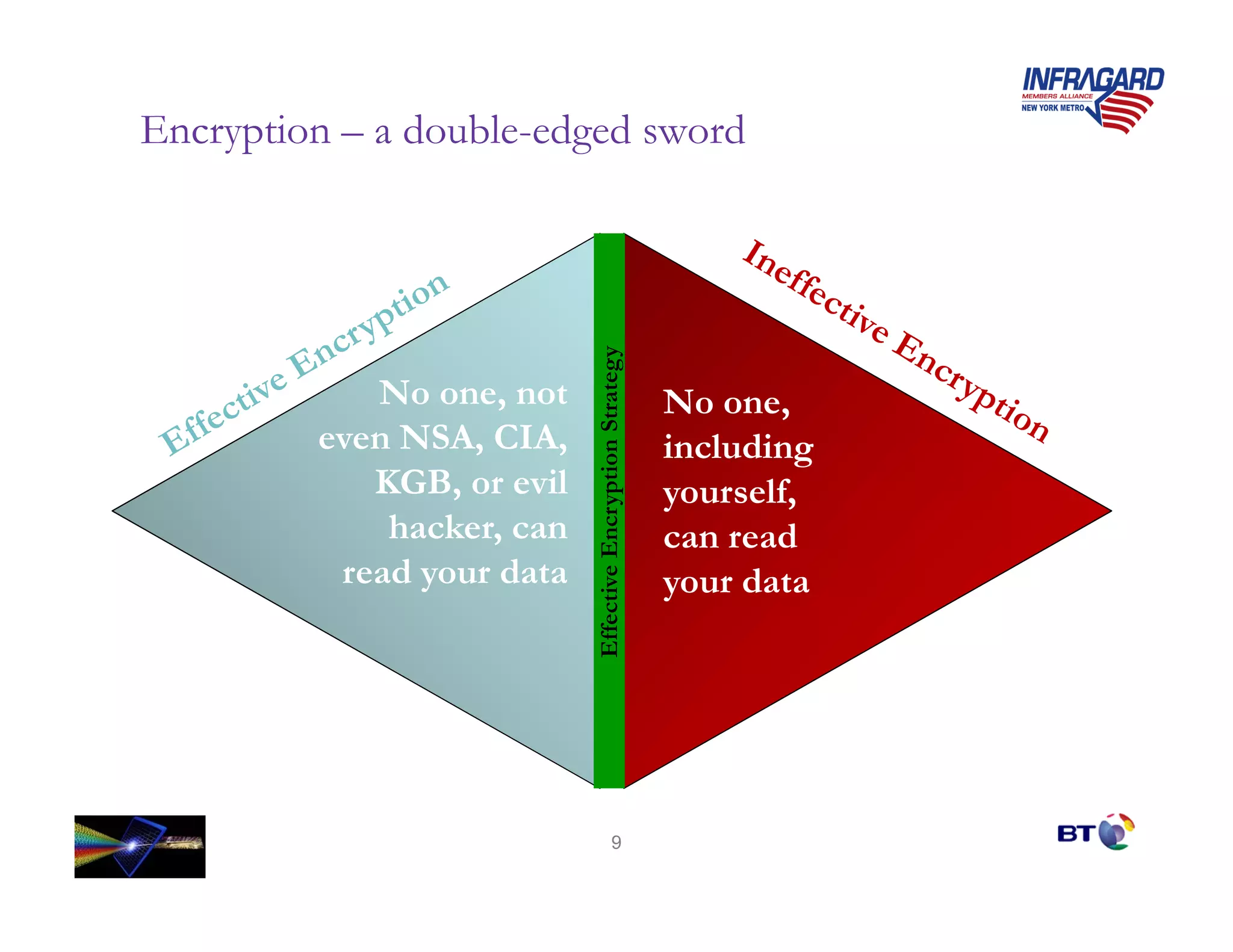
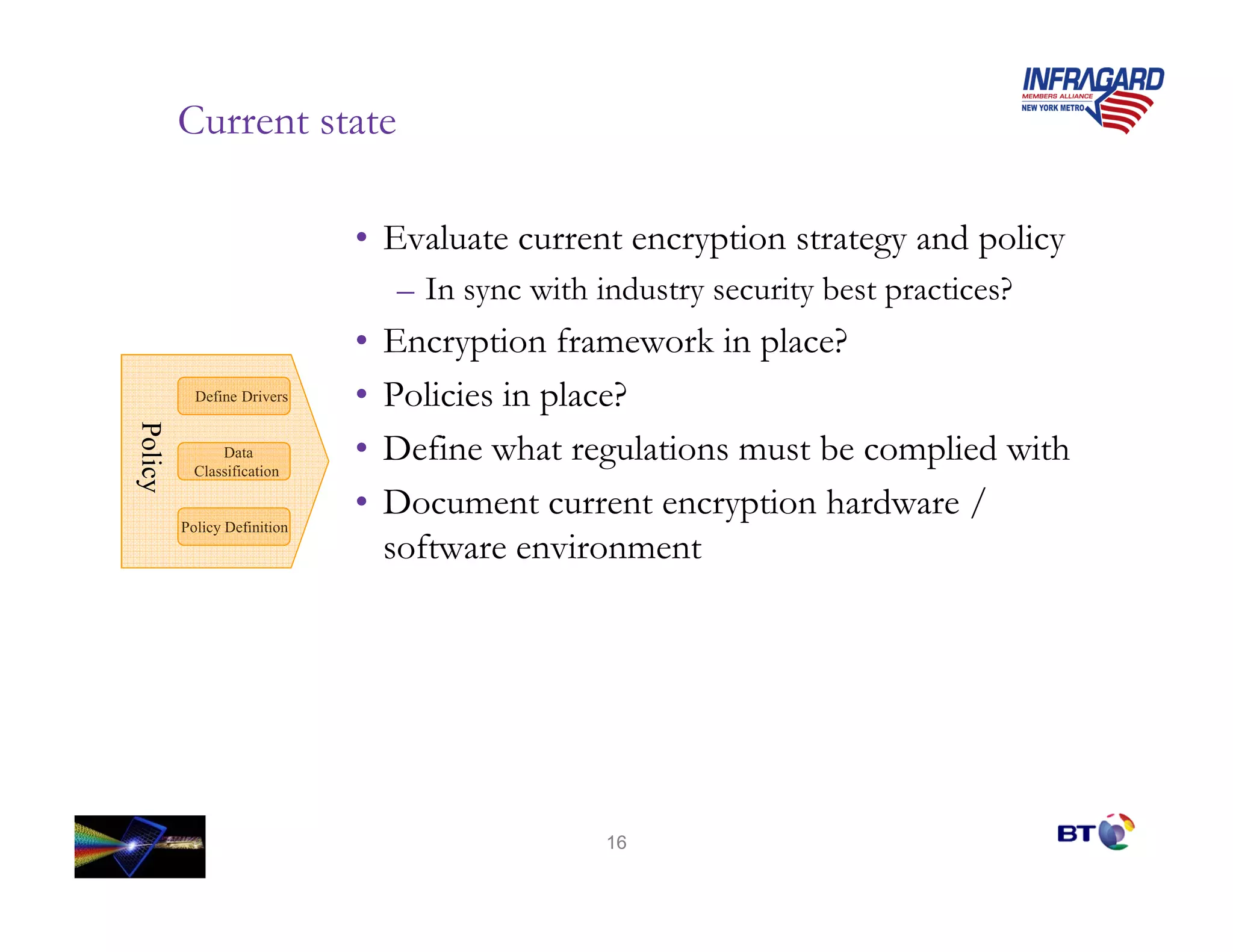
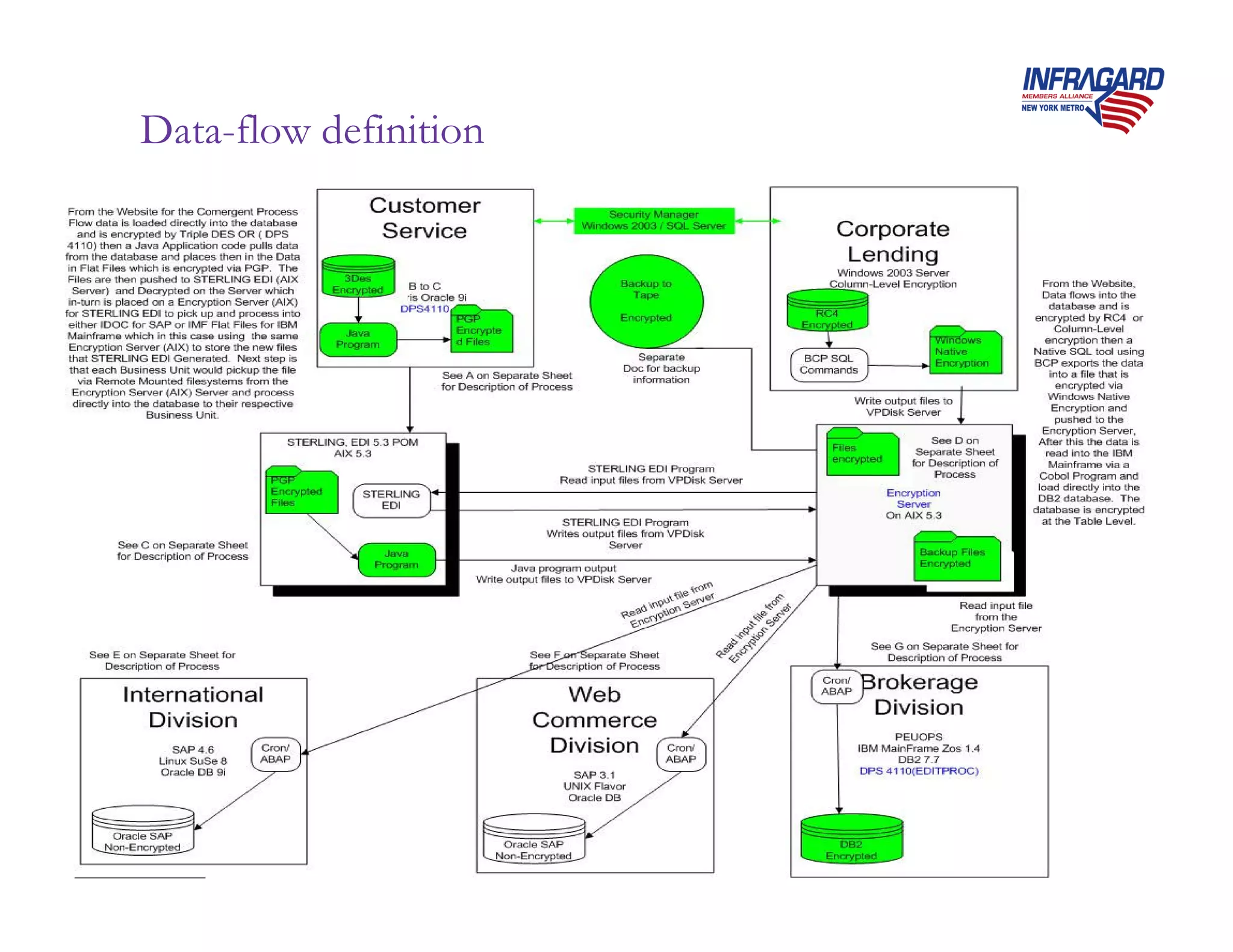
Ben Rothke presented on effective encryption deployment strategies. He began by discussing common mistakes made in encryption rollouts and emphasized that encryption is a process, not just a product. He then outlined a 3 step strategy: 1) define requirements, 2) know where sensitive data resides, and 3) create detailed implementation plans. Finally, he discussed various technical considerations for encryption deployment including full disk encryption, key management, and database encryption.