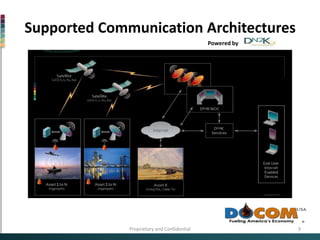
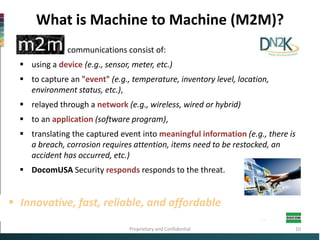
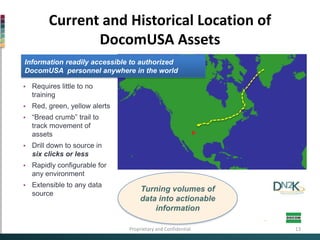
This document discusses cybersecurity and critical infrastructure protection for DocomUSA facilities. It notes that computers are crucial to DocomUSA's refining operations, distribution networks, and other systems. While computer systems run critical infrastructure, many were not designed with security in mind and are vulnerable. The document outlines DocomUSA's efforts to enhance cyber and physical security through critical infrastructure protection activities. It also reviews studies and interviews conducted to develop DocomUSA's cybersecurity protocols to defend against attacks and protect all critical assets.