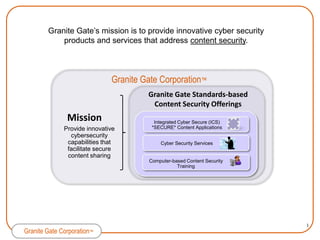
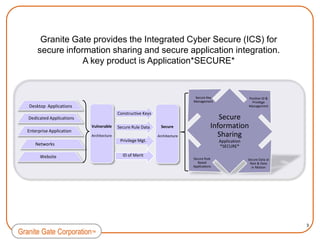
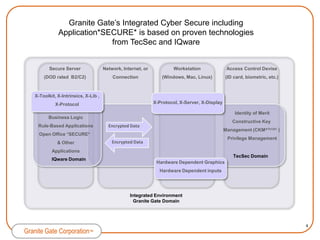
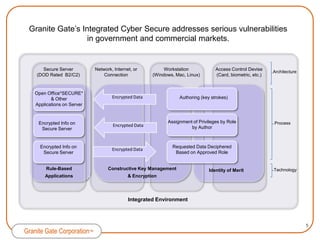
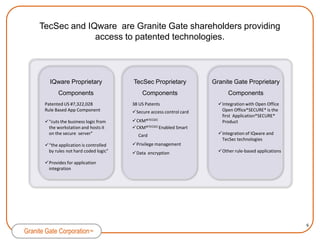
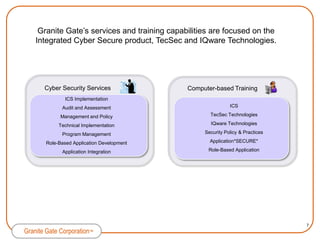
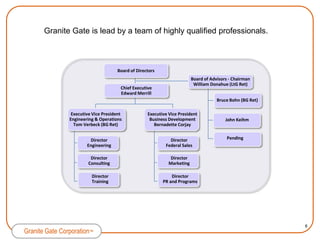
Granite Gate Corporation provides innovative cybersecurity products and services focused on content security, including their Integrated Cyber Secure solution and Application*SECURE* product. Their offerings are based on proven technologies from shareholders TecSec and IQware and address vulnerabilities in government and commercial markets. Granite Gate is led by experienced professionals and offers related services and training to support their secure content solutions.