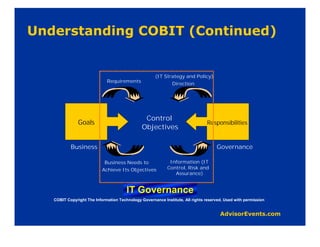
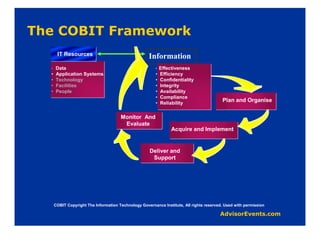
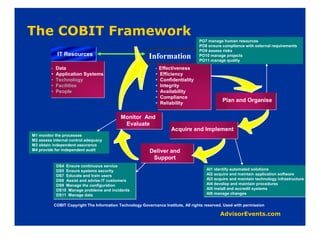
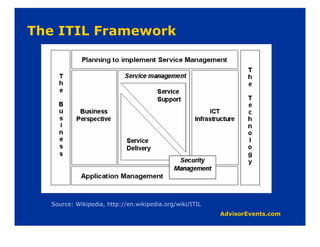
The document discusses why corporate governance and compliance are important. It notes that there are over 200 international regulatory and legal compliance requirements that must be met. Compliance is required in many areas like Sarbanes-Oxley, HIPAA, privacy laws, and more. Strong IT governance is needed to support corporate governance objectives and compliance requirements as technology is so embedded in business operations. IT should support business goals and requirements, not drive them. Various frameworks for compliance and governance are discussed like COBIT, which provides principles and guidelines.