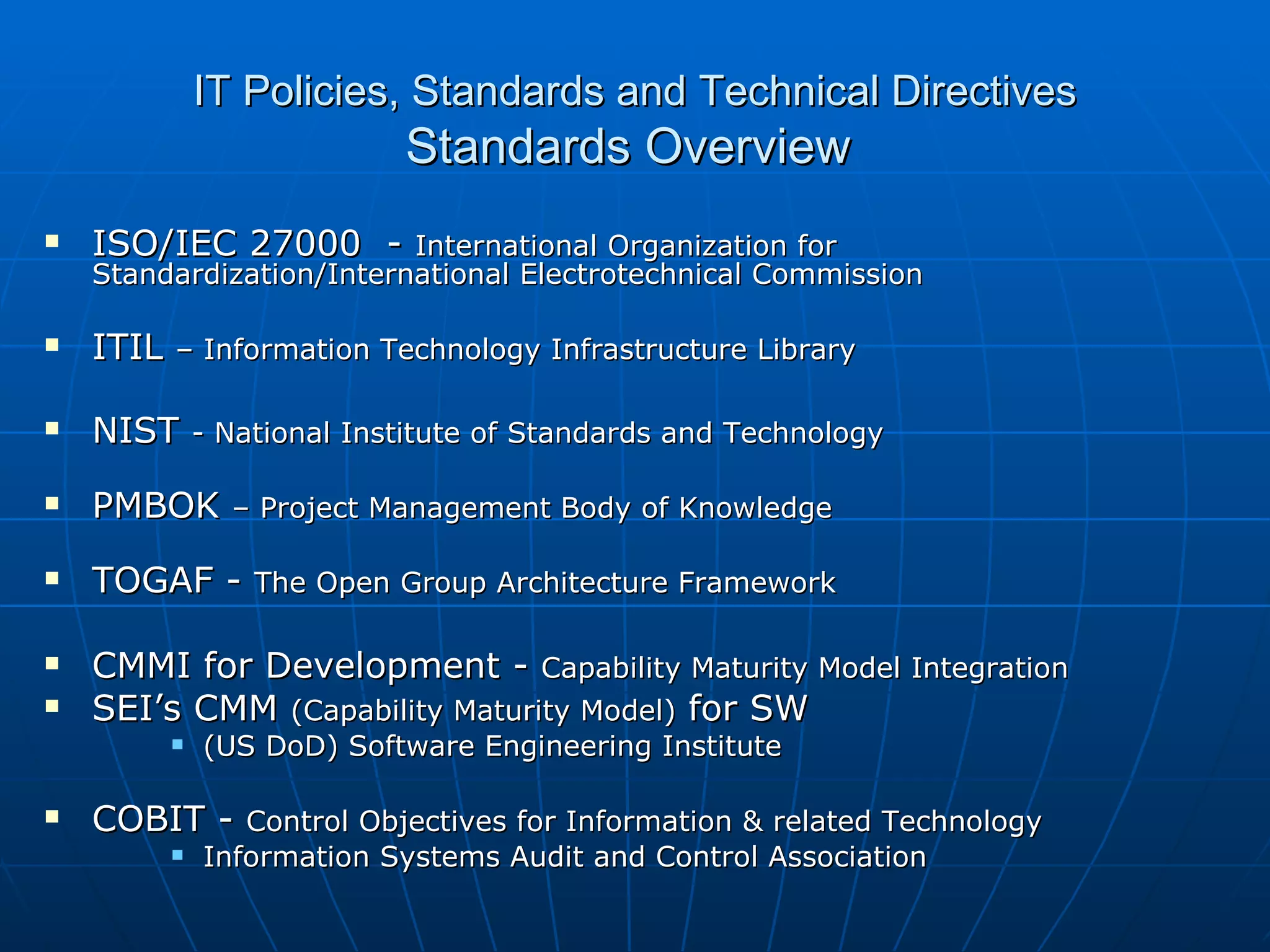
The document discusses IT policies, standards, and technical directives. It provides an overview of several frameworks for IT standards including COBIT, ISACA, ISO, ITIL, NIST, PMBOK, and TOGAF. It also summarizes the key objectives within the COBIT framework for planning and organizing, acquiring and implementing, delivering and supporting, and monitoring and evaluating IT processes. Finally, it provides details on Fidelity's process for managing over 500 technical directives across many categories.